- Table of Contents
-
- H3C Fixed Port Campus Switches Configuration Examples-B70D029-6W100
- 01-Login Management Configuration Examples
- 02-RBAC Configuration Examples
- 03-Software Upgrade Examples
- 04-ISSU Configuration Examples
- 05-Software Patching Examples
- 06-Ethernet Link Aggregation Configuration Examples
- 07-Port Isolation Configuration Examples
- 08-Spanning Tree Configuration Examples
- 09-VLAN Configuration Examples
- 10-VLAN Tagging Configuration Examples
- 11-DHCP Snooping Configuration Examples
- 12-Cross-Subnet Dynamic IP Address Allocation Configuration Examples
- 13-IPv6 over IPv4 Tunneling with OSPFv3 Configuration Examples
- 14-IPv6 over IPv4 GRE Tunnel Configuration Examples
- 15-GRE with OSPF Configuration Examples
- 16-OSPF Configuration Examples
- 17-IS-IS Configuration Examples
- 18-BGP Configuration Examples
- 19-Policy-Based Routing Configuration Examples
- 20-OSPFv3 Configuration Examples
- 21-IPv6 IS-IS Configuration Examples
- 22-Routing Policy Configuration Examples
- 23-IGMP Snooping Configuration Examples
- 24-IGMP Configuration Examples
- 25-MLD Snooping Configuration Examples
- 26-IPv6 Multicast VLAN Configuration Examples
- 27-ACL Configuration Examples
- 28-Traffic Policing Configuration Examples
- 29-GTS and Rate Limiting Configuration Examples
- 30-Priority Mapping and Queue Scheduling Configuration Examples
- 31-Traffic Filtering Configuration Examples
- 32-AAA Configuration Examples
- 33-Port Security Configuration Examples
- 34-Portal Configuration Examples
- 35-SSH Configuration Examples
- 36-IP Source Guard Configuration Examples
- 37-Ethernet OAM Configuration Examples
- 38-CFD Configuration Examples
- 39-DLDP Configuration Examples
- 40-VRRP Configuration Examples
- 41-BFD Configuration Examples
- 42-NTP Configuration Examples
- 43-SNMP Configuration Examples
- 44-NQA Configuration Examples
- 45-Mirroring Configuration Examples
- 46-sFlow Configuration Examples
- 47-OpenFlow Configuration Examples
- 48-MAC Address Table Configuration Examples
- 49-Static Multicast MAC Address Entry Configuration Examples
- 50-IP Unnumbered Configuration Examples
- 51-MVRP Configuration Examples
- 52-MCE Configuration Examples
- 53-Attack Protection Configuration Examples
- 54-Smart Link Configuration Examples
- 55-RRPP Configuration Examples
- 56-BGP Route Selection Configuration Examples
- 57-IS-IS Route Summarization Configuration Examples
- 58-IRF Configuration Examples
- 59-VXLAN Configuration Examples
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 09-VLAN Configuration Examples | 148.69 KB |
Example: Configuring port-based VLANs
Applicable hardware and software versions
Example: Configuring the super VLAN
Applicable hardware and software versions
Configuration restrictions and guidelines
Example: Configuring the private VLAN
Applicable hardware and software versions
Configuration restrictions and guidelines
Introduction
This document provides examples of configuring the port-based VLAN, super VLAN and private VLAN.
Prerequisites
The configuration examples in this document were created and verified in a lab environment, and all the devices were started with the factory default configuration. When you are working on a live network, make sure you understand the potential impact of every command on your network.
This document assumes that you have basic knowledge of VLANs.
Example: Configuring port-based VLANs
Network configuration
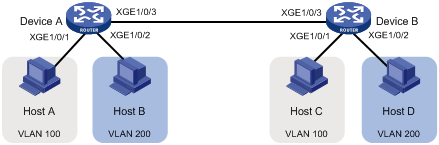
As shown in Figure 1:
· Host A and Host C belong to Department A. VLAN 100 is assigned to Department A.
· Host B and Host D belong to Department B. VLAN 200 is assigned to Department B.
Configure port-based VLANs so that hosts only in the same department can communicate with each other.
Applicable hardware and software versions
The following matrix shows the hardware and software versions to which this configuration example is applicable:
|
Hardware |
Software version |
|
S6520X-HI switch series S6520X-EI switch series |
Supported in Release 1110P01 |
|
S6520X-SI switch series S6520-SI switch series S5000-EI switch series MS4600 switch series |
Supported in Release 1110P01 |
Procedures
# Configure the ports Ten-GigabitEthernet 1/0/1 through Ten-GigabitEthernet 1/0/3 to operate in bridge mode.
[DeviceA] interface range ten-gigabitethernet 1/0/1 to ten-gigabitethernet 1/0/3
[DeviceA-if-range] port link-mode bridge
[DeviceA-if-range] quit
# Create VLAN 100, and assign Ten-GigabitEthernet 1/0/1 to VLAN 100.
[DeviceA-vlan100] port ten-gigabitethernet 1/0/1
[DeviceA-vlan100] quit
# Create VLAN 200, and assign Ten-GigabitEthernet 1/0/2 to VLAN 200.
[DeviceA-vlan200] port ten-gigabitethernet 1/0/2
[DeviceA-vlan200] quit
# Configure Ten-GigabitEthernet 1/0/3 as a trunk port, and assign it to VLANs 100 and 200.
[DeviceA] interface ten-gigabitethernet 1/0/3
[DeviceA-Ten-GigabitEthernet1/0/3] port link-type trunk
[DeviceA-Ten-GigabitEthernet1/0/3] port trunk permit vlan 100 200
2. Configure Device B in the same way Device A is configured. (Details not shown.)
3. Configure hosts:
a. Configure Host A and Host C to be on the same IP subnet. For example, 192.168.100.0/24.
b. Configure Host B and Host D to be on the same IP subnet. For example, 192.168.200.0/24.
Verifying the configuration
# Verify that Host B and Host D can ping each other, but they both fail to ping Host A or Host C. (Details not shown.)
# Display information about VLANs 100 and 200 on Device A.
[DeviceA-Ten-GigabitEthernet1/0/3] display vlan 100
VLAN ID: 100
VLAN type: Static
Route interface: Not configured
Description: VLAN 0100
Name: VLAN 0100
Tagged ports:
Ten-GigabitEthernet1/0/3
Untagged ports:
Ten-GigabitEthernet1/0/1
[DeviceA-Ten-GigabitEthernet1/0/3] display vlan 200
VLAN ID: 200
VLAN type: Static
Route interface: Not configured
Description: VLAN 0200
Name: VLAN 0200
Tagged ports:
Ten-GigabitEthernet1/0/3
Untagged ports:
Ten-GigabitEthernet1/0/2
The output shows that:
· Ten-GigabitEthernet 1/0/3 and Ten-GigabitEthernet 1/0/1 permit packets from 100 to pass through.
· Ten-GigabitEthernet 1/0/3 and Ten-GigabitEthernet 1/0/2 permit packets from 200 to pass through.
Configuration files
Configuration files on both Device B and Device A are the same. The following configuration files use Device A as an example.
#
vlan 100
#
vlan 200
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 100
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 200
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port link-type trunk
port trunk permit vlan 1 100 200
#
Example: Configuring the super VLAN
Network configuration
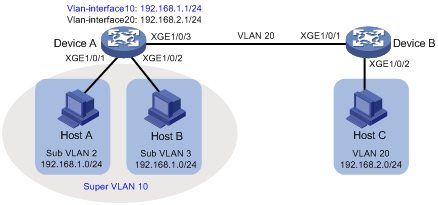
As shown in Figure 2:
· Users in VLAN 2 access the network through Ten-GigabitEthernet 1/0/1 of Device A.
· Users in VLAN 3 access the network through Ten-GigabitEthernet 1/0/2 of Device A.
· Ten-GigabitEthernet 1/0/3 of Device A and Ten-GigabitEthernet 1/0/1 of Device B are in VLAN 20.
· Users in VLAN 20 use the gateway address 192.168.2.1 and IP addresses on the IP network segment 192.168.2.0/24.
Configure a super VLAN to meet the following requirements:
· Users in VLAN 2 and VLAN 3 use the gateway address 192.168.1.1 and IP addresses on the IP network segment 192.168.1.0/24.
· Users in VLAN 2, VLAN 3, and VLAN 20 are isolated at Layer 2 but interoperable at Layer 3.
Applicable hardware and software versions
The following matrix shows the hardware and software versions to which this configuration example is applicable:
|
Hardware |
Software version |
|
S6520X-HI switch series S6520X-EI switch series |
Supported in Release 1110P01 |
|
S6520X-SI switch series S6520-SI switch series S5000-EI switch series MS4600 switch series |
Supported in Release 1110P01 |
Configuration restrictions and guidelines
A super VLAN does not have physical ports. A VLAN that has physical ports cannot be configured as a super VLAN.
Procedures
Configuring Device A
# Create VLAN 10 and configure it as a super VLAN.
<DeviceA> system-view
[DeviceA] vlan 10
[DeviceA-vlan10] supervlan
[DeviceA-vlan10] quit
# Create VLAN 2, and assign Ten-GigabitEthernet 1/0/1 to VLAN 2.
[DeviceA] vlan 2
[DeviceA-vlan2] port ten-gigabitethernet 1/0/1
[DeviceA-vlan2] quit
# Create VLAN 3, and assign Ten-GigabitEthernet 1/0/2 to VLAN 3.
[DeviceA] vlan 3
[DeviceA-vlan3] port ten-gigabitethernet 1/0/2
[DeviceA-vlan3] quit
# Associate super VLAN 10 with VLANs 2 and 3.
[DeviceA] vlan 10
[DeviceA-vlan10] subvlan 2 3
[DeviceA-vlan10] quit
# Create VLAN-interface 10, and assign IP address 192.168.1.1 to it.
[DeviceA] interface vlan-interface 10
[DeviceA-Vlan-interface10] ip address 192.168.1.1 24
# Enable local proxy ARP on VLAN-interface 10.
[DeviceA-Vlan-interface10] local-proxy-arp enable
[DeviceA-Vlan-interface10] quit
# Create VLAN 20.
[DeviceA] vlan 20
[DeviceA-vlan20] quit
# Configure Ten-GigabitEthernet 1/0/3 as a trunk port, and remove the port from VLAN 1.
[DeviceA] interface ten-gigabitethernet 1/0/3
[DeviceA-Ten-GigabitEthernet1/0/3] port link-type trunk
[DeviceA-Ten-GigabitEthernet1/0/3] undo port trunk permit vlan 1
# Assign Ten-GigabitEthernet 1/0/3 to VLAN 20.
[DeviceA-Ten-GigabitEthernet1/0/3] port trunk permit vlan 20
# Create VLAN-interface 20, and assign IP address 192.168.2.1 to it.
[DeviceA] interface Vlan-interface 20
[DeviceA-Vlan-interface20] ip address 192.168.2.1 24
[DeviceA-Vlan-interface20] quit
Configuring Device B
# Create VLAN 20.
[DeviceB] vlan 20
[DeviceB-vlan20] quit
# Configure Ten-GigabitEthernet 1/0/1 as a trunk port, and remove the port from VLAN 1.
[DeviceB] interface ten-gigabitethernet 1/0/1
[DeviceB-Ten-GigabitEthernet1/0/1] port link-type trunk
[DeviceB-Ten-GigabitEthernet1/0/1] undo port trunk permit vlan 1
# Assign Ten-GigabitEthernet 1/0/1 to VLAN 20.
[DeviceB-Ten-GigabitEthernet1/0/1] port trunk permit vlan 20
# Assign Ten-GigabitEthernet 1/0/2 to VLAN 20.
[DeviceB] vlan 20
[DeviceB-vlan20] port ten-gigabitethernet 1/0/2
[DeviceB-vlan20] quit
Verifying the configuration
# Verify the super VLAN configuration.
[DeviceA] display supervlan
Super VLAN ID: 10
Sub-VLAN ID: 2-3
VLAN ID: 10
VLAN type: Static
It is a super VLAN.
Route interface: Configured
IPv4 address: 192.168.1.1
IPv4 subnet mask: 255.255.255.0
Description: VLAN 0010
Name: VLAN 0010
Tagged ports: none
Untagged ports: none
VLAN ID: 2
VLAN type: Static
It is a sub-VLAN.
Route interface: Configured
IPv4 address: 192.168.1.1
IPv4 subnet mask: 255.255.255.0
Description: VLAN 0002
Name: VLAN 0002
Tagged ports: none
Untagged ports:
Ten-GigabitEthernet1/0/1
VLAN ID: 3
VLAN type: Static
It is a sub-VLAN.
Route interface: Configured
IPv4 address: 192.168.1.1
IPv4 subnet mask: 255.255.255.0
Description: VLAN 0003
Name: VLAN 0003
Tagged ports: none
Untagged ports:
Ten-GigabitEthernet1/0/2
# Verify that Host A and Host B can ping each other. In the ARP table of Host A, the IP address of Host B corresponds to the MAC address of VLAN-interface 10. In the ARP table of Host B, the IP address of Host A corresponds to the MAC address of VLAN-interface 10. (Details not shown.)
# Verify that Host A and Host C can ping each other. In the ARP table of Host A, no entry about Host C exists. In the ARP table of Host C, no entry about Host A exists. (Details not shown.)
# Verify that Host B and Host C can ping each other. In the ARP table of Host B, no entry about Host C exists. In the ARP table of Host C, no entry about Host B exists. (Details not shown.)
Configuration files
· Device A:
#
vlan 2
#
vlan 3
#
vlan 10
supervlan
subvlan 2 3
#
vlan 20
#
interface Vlan-interface10
ip address 192.168.1.1 255.255.255.0
local-proxy-arp enable
#
interface Vlan-interface20
ip address 192.168.2.1 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 2
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 3
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 20
#
· Device B:
#
vlan 20
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 20
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 20
#
Example: Configuring the private VLAN
Network configuration
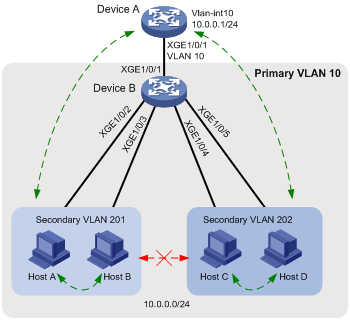
As shown in Figure 3:
· The aggregation-layer device Device A assigns VLAN 10 to Device B. Hosts access the network through VLAN-interface 10.
· Users connected to Device B are on the same subnet 10.0.0.0/24.
· Host A and Host B are in the Marketing department. Host C and Host D are in the Finance department.
Configure the private VLAN feature to meet the following requirements:
· Device A is only aware of the primary VLAN 10.
· Hosts in the same secondary VLAN are interoperable at Layer 2.
· Hosts in different secondary VLANs are isolated at Layer 2.
Requirements analysis
The private VLAN configuration is required only on Device B.
Applicable hardware and software versions
The following matrix shows the hardware and software versions to which this configuration example is applicable:
|
Hardware |
Software version |
|
S6520X-HI switch series S6520X-EI switch series |
Supported in Release 1110P01 |
|
S6520X-SI switch series S6520-SI switch series S5000-EI switch series MS4600 switch series |
Supported in Release 1110P01 |
Configuration restrictions and guidelines
The system default VLAN (VLAN 1) does not support the private VLAN configuration.
Procedures
Configuring Device B
# Create VLAN 10 and configure it as a primary VLAN.
<DeviceB> system-view
[DeviceB] vlan 10
[DeviceB-vlan10] private-vlan primary
[DeviceB-vlan10] quit
# Create VLANs 201 and 202.
[DeviceB] vlan 201 to 202
# Associate primary VLAN 10 with secondary VLANs 201 and 202.
[DeviceB] vlan 10
[DeviceB-vlan10] private-vlan secondary 201 to 202
[DeviceB-vlan10] quit
# Configure the uplink port Ten-GigabitEthernet 1/0/1 as a promiscuous port of VLAN 10.
[DeviceB] interface ten-gigabitethernet 1/0/1
[DeviceB-Ten-GigabitEthernet1/0/1] port private-vlan 10 promiscuous
[DeviceB-Ten-GigabitEthernet1/0/1] quit
# Assign the downlink ports Ten-GigabitEthernet 1/0/2 and Ten-GigabitEthernet 1/0/3 to VLAN 201 as host ports.
[DeviceB] interface range ten-gigabitethernet 1/0/2 to ten-gigabitethernet 1/0/3
[DeviceB-if-range] port link-mode bridge
[DeviceB-if-range] port access vlan 201
[DeviceB-if-range] port private-vlan host
[DeviceB-if-range] quit
# Assign the downlink ports Ten-GigabitEthernet 1/0/4 and Ten-GigabitEthernet 1/0/5 to VLAN 202 as host ports.
[DeviceB] interface range ten-gigabitethernet 1/0/4 to ten-gigabitethernet 1/0/5
[DeviceB-if-range] port link-mode bridge
[DeviceB-if-range] port access vlan 202
[DeviceB-if-range] port private-vlan host
[DeviceB-if-range] quit
Configuring Device A
# Create VLAN 10.
<DeviceA> system-view
[DeviceA] vlan 10
[DeviceA] quit
# Assign Ten-GigabitEthernet 1/0/1 to VLAN 10.
[DeviceA] interface ten-gigabitethernet 1/0/1
[DeviceA-Ten-GigabitEthernet1/0/1] port link-mode bridge
[DeviceA-Ten-GigabitEthernet1/0/1] port access vlan 10
[DeviceA-Ten-GigabitEthernet1/0/1] quit
# Create VLAN-interface 10, and assign IP address 10.0.0.1 to it.
[DeviceA] interface vlan-interface 10
[DeviceA-Vlan-interface10] ip address 10.0.0.1 24
[DeviceA-Vlan-interface10] quit
Verifying the configuration
# Verify that Device A can ping Host A, Host B, Host C, and Host D successfully. (Details not shown.)
# Display the ARP table of Device A.
[DeviceA] display arp
Type: S-Static D-Dynamic O-Openflow R-Rule M-Multiport I-Invalid
IP address MAC address VLAN/VSI Interface/Link ID Aging Type
10.0.0.2 d485-64a1-7e4a 10 XGE1/0/1 19 D
10.0.0.3 7446-a0aa-7774 10 XGE1/0/1 19 D
10.0.0.4 6805-ca05-39ae 10 XGE1/0/1 20 D
10.0.0.5 6805-ca05-414e 10 XGE1/0/1 20 D
# Display the private VLAN configuration on Device B.
[DeviceB] display private-vlan
Primary VLAN ID: 10
Secondary VLAN ID: 201-202
VLAN ID: 10
VLAN type: Static
Private VLAN type: Primary
Route interface: Not configured
Description: VLAN 0010
Name: VLAN 0010
Tagged ports: None
Untagged ports:
Ten-GigabitEthernet1/0/1 Ten-GigabitEthernet1/0/2
Ten-GigabitEthernet1/0/3 Ten-GigabitEthernet1/0/4
Ten-GigabitEthernet1/0/5
VLAN ID: 201
VLAN type: Static
Private VLAN type: Secondary
Route interface: Not configured
Description: VLAN 0201
Name: VLAN 0201
Tagged ports: None
Untagged ports:
Ten-GigabitEthernet1/0/1 Ten-GigabitEthernet1/0/2
Ten-GigabitEthernet1/0/3
VLAN ID: 202
VLAN type: Static
Private VLAN type: Secondary
Route interface: Not configured
Description: VLAN 0202
Name: VLAN 0202
Tagged ports: None
Untagged ports:
Ten-GigabitEthernet1/0/1 Ten-GigabitEthernet1/0/4
Ten-GigabitEthernet1/0/5
The output shows that:
· The promiscuous port Ten-GigabitEthernet1/0/1 is an untagged member of primary VLAN 10 and secondary VLANs 201 and 202.
· The host ports Ten-GigabitEthernet 1/0/2 and Ten-GigabitEthernet 1/0/3 are untagged members of secondary VLANs 201.
· The host ports Ten-GigabitEthernet 1/0/4 and Ten-GigabitEthernet 1/0/5 are untagged members of secondary VLANs 202.
# Verify that Hosts in the same secondary VLAN can ping each other, but they fail to ping hosts in the other secondary VLAN. (Details not shown.)
Configuration files
· Device B:
#
vlan 1
#
vlan 10
private-vlan primary
private-vlan secondary 201 to 202
#
vlan 201 to 202
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port link-type hybrid
undo port hybrid vlan 1
port hybrid vlan 10 201 to 202 untagged
port hybrid pvid vlan 10
port private-vlan 10 promiscuous
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port link-type hybrid
undo port hybrid vlan 1
port hybrid vlan 10 201 untagged
port hybrid pvid vlan 201
port private-vlan host
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port link-type hybrid
undo port hybrid vlan 1
port hybrid vlan 10 201 untagged
port hybrid pvid vlan 201
port private-vlan host
#
interface Ten-GigabitEthernet1/0/4
port link-mode bridge
port link-type hybrid
undo port hybrid vlan 1
port hybrid vlan 10 202 untagged
port hybrid pvid vlan 202
port private-vlan host
#
interface Ten-GigabitEthernet1/0/5
port link-mode bridge
port link-type hybrid
undo port hybrid vlan 1
port hybrid vlan 10 202 untagged
port hybrid pvid vlan 202
port private-vlan host
#
· Device A:
#
vlan 1
#
vlan 10
#
interface Vlan-interface10
ip address 10.0.0.1 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 10
#

