- Table of Contents
-
- H3C WX6103 Access Controller Switch Interface Board Configuration Guide-6W102
- 00-Preface
- 01-Login Configuration
- 02-VLAN Configuration
- 03-IP Addressing and IP Performance Configuration
- 04-QinQ-BPDU Tunneling Configuration
- 05-Port Correlation Configuration
- 06-Link Aggregation Configuration
- 07-MAC Address Table Management Configuration
- 08-Port Security Configuration
- 09-MSTP Configuration
- 10-IP Routing-GR Overview Configuration
- 11-IPv4 Routing Configuration
- 12-IP Source Guard Configuration
- 13-DLDP Configuration
- 14-Multicast Configuration
- 15-LLDP Configuration
- 16-sFlow Configuration
- 17-ARP Configuration
- 18-DHCP Configuration
- 19-ACL Configuration
- 20-QoS Configuration
- 21-Port Mirroring Configuration
- 22-UDP Helper Configuration
- 23-SNMP-RMON Configuration
- 24-NTP Configuration
- 25-DNS Configuration
- 26-File System Management Configuration
- 27-Information Center Configuration
- 28-System Maintaining and Debugging Configuration
- 29-NQA Configuration
- 30-SSH Configuration
- 31-SSL-HTTPS Configuration
- 32-PKI Configuration
- 33-Track Configuration
- 34-Acronyms
- 35-Index
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 12-IP Source Guard Configuration | 104.89 KB |
Table of Contents
1 IP Source Guard Configuration
Configuring a Static Binding Entry
Configuring Dynamic Binding Function
IP Source Guard Configuration Examples
Static Binding Entry Configuration Example
Dynamic Binding Function Configuration Example
Failed to Configure Static Binding Entries and Dynamic Binding Function
![]()
The term switch in this document refers to a switching device in a generic sense or an access controller configured with the switching function unless otherwise specified.
When configuring IP Source Guard, go to these sections for information you are interested in:
l Configuring a Static Binding Entry
l Configuring Dynamic Binding Function
l IP Source Guard Configuration Examples
IP Source Guard Overview
By filtering packets on a per-port basis, IP source guard prevents packets with illegal IP addresses and MAC addresses from traveling through, improving the network security. After receiving a packet, the port looks up the key attributes (including IP address, MAC address and VLAN tag) of the packet in the binding entries of the IP source guard. If there is a matching entry, the port will forward the packet. Otherwise, the port will abandon the packet.
IP source guard filters packets based on the following types of binding entries:
l IP-port binding entry
l MAC-port binding entry
l IP-MAC-port binding entry
You can manually set static binding entries, or use DHCP Snooping to provide dynamic binding entries. Binding is on a per-port basis. After a binding entry is configured on a port, it is effective only to the port, instead of other ports.
![]()
IP source guard and aggregation group configuration are mutually exclusive.
Configuring a Static Binding Entry
Follow these steps to configure a static binding entry:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter interface view |
interface interface-type interface-number |
— |
|
Configure a static binding entry |
user-bind { ip-address ip-address | ip-address ip-address mac-address mac-address | mac-address mac-address } |
Required No static binding entry exists by default. |
![]()
l The system does not support repeatedly configuring a binding entry to one port. A binding entry can be configured to multiple ports.
l In a valid binding entry, the MAC address cannot be all 0s, all Fs (a broadcast address), or a multicast address, and the IP address can only be a Class A, Class B, or Class C address and can be neither 127.x.x.x nor 0.0.0.0.
Configuring Dynamic Binding Function
After the dynamic binding function is enabled on a port, IP source guard will receive and process corresponding DHCP Snooping entries, which contain such information as MAC address, IP address, VLAN tag, port information or entry type. It adds the obtained information to the dynamic binding entries to enable the port to filter packets according to the binding entries.
Follow these steps to configure dynamic binding function:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter interface view |
interface interface-type interface-number |
— |
|
Configure dynamic binding function |
ip check source { ip-address | ip-address mac-address | mac-address } |
Required Not configured by default |
Displaying IP Source Guard
|
To do… |
Use the command… |
Remarks |
|
Display information about static binding entries |
display user-bind [ interface interface-type interface-number | ip-address ip-address | mac-address mac-address ] |
Available in any view |
|
Display information about dynamic binding entries |
display ip check source [ interface interface-type interface-number | ip-address ip-address | mac-address mac-address ] |
Available in any view |
IP Source Guard Configuration Examples
Static Binding Entry Configuration Example
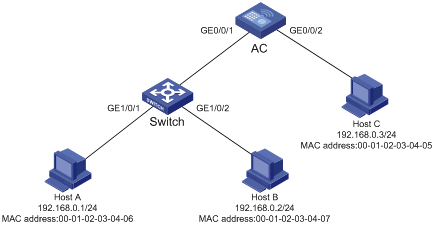
Network requirements
As shown in Figure 1-1, an access controller (AC), a switch and Hosts A, B and C are on an Ethernet. Host A and Host B are connected to ports GigabitEthernet1/0/1 and GigabitEthernet 1/0/2 of the switch respectively, Host C is connected to port GigabitEthernet 0/0/2 of the AC, while the switch is connected to port GigabitEthernet 0/0/1 of the AC.
Detailed requirements are as follows:
l On port GigabitEthernet 0/0/2 of AC, only IP packets with the source MAC address of 00-01-02-03-04-05 and the source IP address of 192.168.0.3 can pass.
l On port GigabitEthernet 0/0/1 of AC, only IP packets with the source MAC address of 00-01-02-03-04-06 and the source IP address of 192.168.0.1 can pass.
l On port GigabitEthernet 1/0/1 of Switch, only IP packets with the source MAC address of 00-01-02-03-04-06 and the source IP address of 192.168.0.1 can pass.
l On port GigabitEthernet 1/0/2 of Switch, only IP packets with the source MAC address of 00-01-02-03-04-07 and the source IP address of 192.168.0.2 can pass.
Network diagram
Figure 1-1 Network diagram for configuring static binding entries
Configuration procedure
1) Configure AC
# Configure the IP addresses of various interfaces (omitted).
# Configure port GigabitEthernet 0/0/2 of AC to allow only IP packets with the source MAC address of 00-01-02-03-04-05 and the source IP address of 192.168.0.3 to pass.
<AC> system-view
[AC] interface GigabitEthernet 0/0/2
[AC-GigabitEthernet0/0/2] user-bind ip-address 192.168.0.3 mac-address 0001-0203-0405
[AC-GigabitEthernet0/0/2] quit
# Configure port GigabitEthernet 0/0/1 of AC to allow only IP packets with the source MAC address of 00-01-02-03-04-06 and the source IP address of 192.168.0.1 to pass.
[AC] interface GigabitEthernet 0/0/1
[AC-GigabitEthernet0/0/1] user-bind ip-address 192.168.0.1 mac-address 0001-0203-0406
2) Configure Switch
# Configure the IP addresses of various interfaces (omitted).
# Configure port GigabitEthernet 1/0/1 of Switch to allow only IP packets with the source MAC address of 00-01-02-03-04-06 and the source IP address of 192.168.0.1 to pass.
<Switch> system-view
[Switch] interface gigabitethernet 1/0/1
[Switch-GigabitEthernet1/0/1] user-bind ip-address 192.168.0.1 mac-address 0001-0203-0406
[Switch-GigabitEthernet1/0/1] quit
# Configure port GigabitEthernet 1/0/2 of Switch to allow only IP packets with the source MAC address of 00-01-02-03-04-07 and the source IP address of 192.168.0.2 to pass.
[Switch] interface gigabitethernet 1/0/2
[Switch-GigabitEthernet1/0/2] user-bind ip-address 192.168.0.2 mac-address 0001-0203-0407
3) Verify the configuration
# On AC, static binding entries are configured successfully.
<AC> display user-bind
The following user address bindings have been configured:
MAC IP Vlan Port Status
0001-0203-0405 192.168.0.3 N/A GigabitEthernet0/0/2 Static
0001-0203-0406 192.168.0.1 N/A GigabitEthernet0/0/1 Static
------------------2 binding entries queried, 2 listed------------------
# On Switch, static binding entries are configured successfully.
<Switch> display user-bind
The following user address bindings have been configured:
MAC IP Vlan Port Status
0001-0203-0406 192.168.0.1 N/A GigabitEthernet1/0/1 Static
0001-0203-0407 192.168.0.2 N/A GigabitEthernet1/0/2 Static
------------------2 binding entries queried, 2 listed------------------
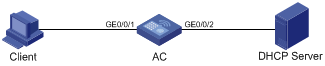
Dynamic Binding Function Configuration Example
Network requirements
AC connects to Client and DHCP Server through GigabitEthernet 0/0/1 and GigabitEthernet 0/0/2 respectively. DHCP Snooping is enabled on AC.
Detailed requirements are as follows:
l Client (with the MAC address of 00-01-02-03-04-06) obtains an IP address through the DHCP Server.
l On AC, create the DHCP Snooping entry of Client.
l On port GigabitEthernet 0/0/1 of AC, enable dynamic binding function to prevent attacks from using forged IP addresses to attack the server.
![]()
For detailed configuration of DHCP Server, refer to DHCP in H3C WX6103 Access Controller Switch Interface Board Configuration Guide.
Network diagram
Figure 1-2 Network diagram for configuring dynamic binding
Configuration procedure
1) Configure AC
# Configure dynamic binding on port GigabitEthernet 0/0/1.
<AC> system-view
[AC] interface GigabitEthernet 0/0/1
[AC-GigabitEthernet0/0/1] ip check source ip-address mac-address
[AC-GigabitEthernet0/0/1] quit
# Enable DHCP snooping on Switch A.
[AC] dhcp-snooping
# Configure port GigabitEthernet 0/0/2 connected to the DHCP server as a trusted port.
[AC] interface GigabitEthernet0/0/2
[AC-GigabitEthernet0/0/2] dhcp-snooping trust
[AC-GigabitEthernet0/0/2] quit
2) Verify the configuration
# Display the dynamic binding entries that port GigabitEthernet 0/0/1 has obtained from DHCP Snooping.
<AC> display ip check source
The following user address bindings have been configured:
MAC IP Vlan Port Status
0001-0203-0406 192.168.0.1 1 GigabitEthernet0/0/1 DHCP-SNP
-----------------1 binding entries queried, 1 listed------------------
# Display the dynamic entries of DHCP Snooping and check it is identical with the dynamic entries that port GigabitEthernet 0/0/1 has obtained.
<AC> display dhcp-snooping
DHCP Snooping is enabled.
The client binding table for all untrusted ports.
Type : D--Dynamic , S--Static
Type IP Address MAC Address Lease VLAN Interface
==== =============== ============== ============ ==== =================
D 192.168.0.1 0001-0203-0406 86335 1 GigabitEthernet0/0/1
As you see, port GigabitEthernet 0/0/1 has obtained the dynamic entries generated by DHCP Snooping after it is configured with dynamic binding function.
Troubleshooting
Failed to Configure Static Binding Entries and Dynamic Binding Function
Symptom
Configuring static binding entries and dynamic binding function fails on a port.
Analysis
IP Source Guard is not supported on the port which has joined an aggregation group. Neither static binding entries nor dynamic binding function can be configured on the port which has joined an aggregation group.
Solution
Remove the port from the aggregation group.

