- Table of Contents
-
- 05-Network Connectivity Configuration Guide
- 00-Preface
- 01-MAC address table configuration
- 02-Ethernet link aggregation configuration
- 03-VLAN configuration
- 04-Loop detection configuration
- 05-Spanning tree configuration
- 06-LLDP configuration
- 07-Layer 2 forwarding configuration
- 08-VLAN termination configuration
- 09-PPP configuration
- 10-L2TP configuration
- 11-ARP configuration
- 12-IP addressing configuration
- 13-DHCP configuration
- 14-DHCPv6 configuration
- 15-DNS configuration
- 16-NAT configuration
- 17-IP performance optimization configuration
- 18-IPv6 basics configuration
- 19-GRE configuration
- 20-Tunneling configuration
- 21-Basic IP routing configuration
- 22-IP forwarding basics configuration
- 23-Static routing configuration
- 24-IPv6 static routing configuration
- 25-Policy-based routing configuration
- 26-IPv6 policy-based routing configuration
- 27-RIP configuration
- 28-RIPng configuration
- 29-Multicast overview
- 30-IGMP snooping configuration
- 31-MLD snooping configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 27-RIP configuration | 188.09 KB |
Contents
Restrictions and guidelines for configuring basic RIP
Controlling RIP reception and advertisement on interfaces
Configuring an additional routing metric
Configuring RIPv2 route summarization
Disabling host route reception
Configuring received/redistributed route filtering
Configuring RIP route redistribution
Tuning and optimizing RIP networks
Enabling split horizon and poison reverse
Setting the maximum number of RIP ECMP routes
Setting the RIP triggered update interval
Configuring the RIP packet sending rate
Setting the maximum length of RIP packets
Configuring RIP network management
Enabling zero field check for incoming RIPv1 messages
Enabling source IP address check for incoming RIP updates
Configuring RIPv2 message authentication
Display and maintenance commands for RIP
Example: Configuring basic RIP
Configuring RIP
About RIP
Routing Information Protocol (RIP) is a distance-vector IGP suited to small-sized networks. It employs UDP to exchange route information through port 520.
RIP routing metrics
RIP uses a hop count to measure the distance to a destination. The hop count from a router to a directly connected network is 0. The hop count from a router to a directly connected router is 1. To limit convergence time, RIP restricts the value range of the metric from 0 to 15. A destination with a metric value of 16 (or greater) is considered unreachable. For this reason, RIP is not suitable for large-sized networks.
RIP route entries
RIP stores routing entries in a database. Each routing entry contains the following elements:
· Destination address—IP address of a destination host or a network.
· Next hop—IP address of the next hop.
· Egress interface—Egress interface of the route.
· Metric—Cost from the local router to the destination.
· Route time—Time elapsed since the last update. The time is reset to 0 when the routing entry is updated.
· Route tag—Used for marking an external route.
RIP operation
RIP works as follows:
1. RIP sends request messages to neighboring routers. Neighboring routers return response messages that contain their routing tables.
2. RIP uses the received responses to update the local routing table and sends triggered update messages to its neighbors. All RIP routers on the network do this to learn latest routing information.
3. RIP periodically sends the local routing table to its neighbors. After a RIP neighbor receives the message, it updates its routing table, selects optimal routes, and sends an update to other neighbors. RIP ages routes to keep only valid routes.
Routing loop prevention
RIP uses the following mechanisms to prevent routing loops:
· Counting to infinity—A destination with a metric value of 16 is considered unreachable. When a routing loop occurs, the metric value of a route will increment to 16 to avoid endless looping.
· Triggered updates—RIP immediately advertises triggered updates for topology changes to reduce the possibility of routing loops and to speed up convergence.
· Split horizon—Disables RIP from sending routes through the interface where the routes were learned to prevent routing loops and save bandwidth.
· Poison reverse—Enables RIP to set the metric of routes received from a neighbor to 16 and sends these routes back to the neighbor. The neighbor can delete such information from its routing table to prevent routing loops.
RIP versions
There are two RIP versions, RIPv1 and RIPv2.
RIPv1 is a classful routing protocol. It advertises messages only through broadcast. RIPv1 messages do not carry mask information, so RIPv1 can only recognize natural networks such as Class A, B, and C. For this reason, RIPv1 does not support discontiguous subnets.
RIPv2 is a classless routing protocol. It has the following advantages over RIPv1:
· Supports route tags.
· Supports masks, route summarization, and CIDR.
· Supports designated next hops to select the best ones on broadcast networks.
· Supports multicasting route updates so only RIPv2 routers can receive these updates to reduce resource consumption.
· Supports plain text authentication and MD5 authentication to enhance security.
RIPv2 supports two transmission modes: broadcast and multicast. Multicast is the default mode using 224.0.0.9 as the multicast address. An interface operating in RIPv2 broadcast mode can also receive RIPv1 messages.
Protocols and standards
· RFC 1058, Routing Information Protocol
· RFC 1723, RIP Version 2 - Carrying Additional Information
· RFC 1721, RIP Version 2 Protocol Analysis
· RFC 1722, RIP Version 2 Protocol Applicability Statement
· RFC 1724, RIP Version 2 MIB Extension
· RFC 2082, RIPv2 MD5 Authentication
· RFC 2091, Triggered Extensions to RIP to Support Demand Circuits
RIP tasks at a glance
To configure RIP, perform the following tasks:
a. Enabling RIP
b. (Optional.) Controlling RIP reception and advertisement on interfaces
c. (Optional.) Configuring a RIP version
To enable RIP on a link that does not support broadcast or multicast, you must manually specify a RIP neighbor.
2. (Optional.) Configuring RIP route control
¡ Configuring an additional routing metric
¡ Configuring RIPv2 route summarization
¡ Disabling host route reception
¡ Configuring received/redistributed route filtering
¡ Setting a preference for RIP
¡ Configuring RIP route redistribution
3. (Optional.) Tuning and optimizing RIP networks
¡ Enabling split horizon and poison reverse
¡ Setting the maximum number of RIP ECMP routes
¡ Setting the RIP triggered update interval
¡ Configuring the RIP packet sending rate
¡ Setting the maximum length of RIP packets
4. (Optional.) Configuring RIP network management
5. Enhancing RIP availability
6. (Optional.) Enhancing RIP security
¡ Enabling zero field check for incoming RIPv1 messages
¡ Enabling source IP address check for incoming RIP updates
¡ Configuring RIPv2 message authentication
Configuring basic RIP
Restrictions and guidelines for configuring basic RIP
To enable multiple RIP processes on a router, you must specify an ID for each process. A RIP process ID has only local significance. Two RIP routers having different process IDs can also exchange RIP packets.
Enabling RIP
About this task
You can enable RIP on a network and specify a wildcard mask for the network. After that, only the interface attached to the network runs RIP.
Restrictions and guidelines
If you configure RIP settings in interface view before enabling RIP, the settings do not take effect until RIP is enabled.
If a physical interface is attached to multiple networks, you cannot advertise these networks in different RIP processes.
You cannot enable multiple RIP processes on a physical interface.
The rip enable command takes precedence over the network command.
Enabling RIP on a network
1. Enter system view.
system-view
2. Enable RIP and enter RIP view.
rip [ process-id ]
By default, RIP is disabled.
3. Enable RIP on a network.
network network-address [ wildcard-mask ]
By default, RIP is disabled on a network.
The network 0.0.0.0 command can enable RIP on all interfaces in a single process, but does not apply to multiple RIP processes.
Enabling RIP on an interface
1. Enter system view.
system-view
2. Enable RIP and enter RIP view.
rip [ process-id ]
By default, RIP is disabled.
3. Return to system view.
quit
4. Enter interface view.
interface interface-type interface-number
5. Enable RIP on the interface.
rip process-id enable [ exclude-subip ]
By default, RIP is disabled on an interface.
Controlling RIP reception and advertisement on interfaces
About this task
You can perform this task to configure the following features:
· Suppressing an interface. The suppressed interface can receive RIP messages but cannot send RIP messages.
· Disabling an interface from sending RIP messages.
· Disabling an interface from receiving RIP messages.
Restrictions and guidelines for RIP reception and advertisement control on interfaces
An interface suppressed by using the silent-interface command can only receive RIP messages. It cannot send RIP messages. You can use the silent-interface all command to suppress all interfaces. The silent-interface command takes precedence over the rip input and rip output commands.
Suppressing an interface
1. Enter system view.
system-view
2. Enter RIP view.
rip [ process-id ]
3. Suppress an interface.
silent-interface { interface-type interface-number | all }
By default, all RIP-enabled interfaces can send RIP messages.
The suppressed interface can still receive RIP messages and respond to unicast requests containing unknown ports.
Disabling an interface from receiving RIP messages
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Disable an interface from receiving RIP messages.
undo rip input
By default, a RIP-enabled interface can receive RIP messages.
Disabling an interface from sending RIP messages
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Disable an interface from sending RIP messages.
undo rip output
By default, a RIP-enabled interface can send RIP messages.
Configuring a RIP version
About this task
You can configure a global RIP version in RIP view or an interface-specific RIP version in interface view.
An interface preferentially uses the interface-specific RIP version. If no interface-specific version is specified, the interface uses the global RIP version. If neither a global nor interface-specific RIP version is configured, the interface sends RIPv1 broadcasts and can receive the following:
· RIPv1 broadcasts and unicasts.
· RIPv2 broadcasts, multicasts, and unicasts.
Procedure
1. Enter system view.
system-view
2. Specify a RIP version.
¡ Execute the following commands in sequence to specify a global RIP version:
rip [ process-id ]
version { 1 | 2 }
By default, no global version is specified. An interface sends RIPv1 broadcasts, and can receive RIPv1 broadcasts and unicasts, and RIPv2 broadcasts, multicasts, and unicasts.
¡ Execute the following commands in sequence to specify a RIP version on an interface:
interface interface-type interface-number
rip version { 1 | 2 [ broadcast | multicast ] }
By default, no interface-specific RIP version is specified. The interface sends RIPv1 broadcasts, and can receive RIPv1 broadcasts and unicasts, and RIPv2 broadcasts, multicasts, and unicasts.
Specifying a RIP neighbor
About this task
Typically RIP messages are sent in broadcast or multicast. To enable RIP on a link that does not support broadcast or multicast, you must manually specify a RIP neighbor.
Restrictions and guidelines
As a best practice, do not use the peer ip-address command to specify a directly connected neighbor. The neighbor might receive a route update in both unicast and multicast (or broadcast) messages from the device.
Procedure
1. Enter system view.
system-view
2. Enter RIP view.
rip [ process-id ]
3. Specify a RIP neighbor.
peer ip-address
By default, RIP does not unicast updates to any peer.
4. Disable source IP address check on inbound RIP updates.
undo validate-source-address
By default, source IP address check is enabled on inbound RIP updates.
If the specified neighbor is not directly connected, disable source address check on incoming updates.
Configuring RIP route control
Configuring an additional routing metric
About this task
An additional routing metric (hop count) can be added to the metric of an inbound or outbound RIP route.
· An outbound additional metric is added to the metric of a sent route, and it does not change the route's metric in the routing table.
· An inbound additional metric is added to the metric of a received route before the route is added into the routing table, and the route's metric is changed. If the sum of the additional metric and the original metric is greater than 16, the metric of the route is 16.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Specify an inbound additional routing metric.
rip metricin value
By default, the additional metric of an inbound route is 0.
4. Specify an outbound additional routing metric.
rip metricout value
By default, the additional metric of an outbound route is 1.
Configuring RIPv2 route summarization
About this task
Perform this task to summarize contiguous subnets into a summary network and sends the network to neighbors. The smallest metric among all summarized routes is used as the metric of the summary route.
You can use the following methods to summarize routes in RIPv2:
· Automatic summarization—Configure RIPv2 to generate a natural network for contiguous subnets. For example, suppose there are three subnet routes 10.1.1.0/24, 10.1.2.0/24, and 10.1.3.0/24. Automatic summarization automatically creates and advertises a summary route 10.0.0.0/8 instead of the more specific routes.
· Manual summarization—Manually configure a summary route. RIPv2 advertises the summary route rather than more specific routes. For example, suppose contiguous subnets routes 10.1.1.0/24, 10.1.2.0/24, and 10.1.3.0/24 exist in the routing table. You can create a summary route 10.1.0.0/16 on GigabitEthernet 1/0/1 to advertise the summary route instead of the more specific routes. By default, natural masks are used to advertise summary routes. To manually configure a summary route on an interface, you must first disable RIPv2 automatic route summarization.
Restrictions and guidelines
To prevent loops caused by route summarization, create a black hole route by specifying interface NULL 0 as the output interface of the summary route. Packets that match the black hole route are dropped.
Enabling RIPv2 automatic route summarization
1. Enter system view.
system-view
2. Enter RIP view.
rip [ process-id ]
3. Enable RIPv2 automatic route summarization.
summary
By default, RIPv2 automatic route summarization is enabled.
If subnets in the routing table are not contiguous, disable automatic route summarization to advertise more specific routes.
Advertising a summary route
1. Enter system view.
system-view
2. Enter RIP view.
rip [ process-id ]
3. Disable RIPv2 automatic route summarization.
undo summary
By default, RIPv2 automatic route summarization is enabled.
4. Return to system view.
quit
5. Enter interface view.
interface interface-type interface-number
6. Configure a summary route.
rip summary-address ip-address { mask-length | mask }
By default, no summary route is configured.
Disabling host route reception
About this task
This task disables RIPv2 from receiving host routes from the same network to save network resources. This feature does not apply to RIPv1.
Procedure
1. Enter system view.
system-view
2. Enter RIP view.
rip [ process-id ]
3. Disable RIP from receiving host routes.
undo host-route
By default, RIP receives host routes.
Advertising a default route
About this task
You can advertise a default route on all RIP interfaces in RIP view or on a specific RIP interface in interface view. The interface view setting takes precedence over the RIP view settings.
To disable an interface from advertising a default route, use the rip default-route no-originate command on the interface.
The router enabled to advertise a default route does not accept default routes from RIP neighbors.
Procedure
1. Enter system view.
system-view
2. Advertise a default route.
¡ Execute the following commands in sequence to configure RIP to advertise a default route:
rip [ process-id ]
default-route { only | originate } [ cost cost-value ]
By default, RIP does not advertise a default route.
¡ Execute the following commands in sequence to configure a RIP interface to advertise a default route:
interface interface-type interface-number
rip default-route { { only | originate } [ cost cost-value ] | no-originate }
By default, a RIP interface can advertise a default route if the RIP process is enabled to advertise a default route.
Configuring received/redistributed route filtering
About this task
This task allows you to create a policy to filter received or redistributed routes that match specific criteria such as an ACL or IP prefix list.
Procedure
1. Enter system view.
system-view
2. Enter RIP view.
rip [ process-id ]
3. Configure the filtering of received routes.
filter-policy { ipv4-acl-number | gateway prefix-list-name | prefix-list prefix-list-name [ gateway prefix-list-name ] } import [ interface-type interface-number ]
By default, the filtering of received routes is not configured.
This command filters received routes. Filtered routes are not installed into the routing table or advertised to neighbors.
4. Configure the filtering of redistributed routes.
filter-policy { ipv4-acl-number | prefix-list prefix-list-name } export [ interface-type interface-number | direct | rip [ process-id ] | static ]
By default, the filtering of redistributed routes is not configured.
This command filters redistributed routes, including routes redistributed with the import-route command.
Setting a preference for RIP
About this task
If multiple IGPs find routes to the same destination, the route found by the IGP that has the highest priority is selected as the optimal route. Perform this task to assign a preference to RIP. The smaller the preference value, the higher the priority.
Procedure
1. Enter system view.
system-view
2. Enter RIP view.
rip [ process-id ]
3. Set a preference for RIP.
preference { preference }
The default preference for RIP is 100.
Configuring RIP route redistribution
About this task
Perform this task to configure RIP to redistribute static and direct routes and routes from other routing protocols.
Procedure
1. Enter system view.
system-view
2. Enter RIP view.
rip [ process-id ]
3. Configure route redistribution.
¡ Redistribute direct or static routes.
import-route { direct | static } [ cost cost-value | tag tag ] *
¡ Redistribute routes from other RIP processes.
import-route rip [ process-id | all-processes ] [ allow-direct | cost cost-value | tag tag ] *
By default, RIP does not redistribute routes.
This command can redistribute only active routes. To view active routes, use the display ip routing-table protocol command.
4. (Optional.) Set a default cost for redistributed routes.
default cost cost-value
The default cost for redistributed routes is 0.
Tuning and optimizing RIP networks
Setting RIP timers
About this task
You can change the RIP network convergence speed by adjusting the following RIP timers:
· Update timer—Specifies the interval between route updates.
· Timeout timer—Specifies the route aging time. If no update for a route is received within the aging time, the metric of the route is set to 16.
· Suppress timer—Specifies how long a RIP route stays in suppressed state. When the metric of a route is 16, the route enters the suppressed state. A suppressed route can be replaced by an updated route that is received from the same neighbor before the suppress timer expires and has a metric less than 16.
· Garbage-collect timer—Specifies the interval from when the metric of a route becomes 16 to when it is deleted from the routing table. RIP advertises the route with a metric of 16. If no update is announced for that route before the garbage-collect timer expires, the route is deleted from the routing table.
Restrictions and guidelines
To avoid unnecessary traffic or route flapping, configure identical RIP timer settings on RIP routers.
Procedure
1. Enter system view.
system-view
2. Enter RIP view.
rip [ process-id ]
3. Set RIP timers.
timers { garbage-collect garbage-collect-value | suppress suppress-value | timeout timeout-value | update update-value } *
The default settings are as follows:
¡ The garbage-collect timer is 120 seconds.
¡ The suppress timer is 120 seconds.
¡ The timeout timer is 180 seconds.
¡ The update timer is 30 seconds.
Enabling split horizon and poison reverse
About this task
The split horizon and poison reverse features can prevent routing loops.
· Split horizon disables RIP from sending routes through the interface where the routes were learned to prevent routing loops between adjacent routers.
· Poison reverse allows RIP to send routes through the interface where the routes were learned. The metric of these routes is always set to 16 (unreachable) to avoid routing loops between neighbors.
Restrictions and guidelines
If both split horizon and poison reverse are configured, only the poison reverse feature takes effect.
Enabling split horizon
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable split horizon.
rip split-horizon
By default, split horizon is enabled.
Enabling poison reverse
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable poison reverse.
rip poison-reverse
By default, poison reverse is disabled.
Setting the maximum number of RIP ECMP routes
About this task
Perform this task to use ECMP routes to share the load of the RIP network.
Procedure
1. Enter system view.
system-view
2. Enter RIP view.
rip [ process-id ]
3. Set the maximum number of RIP ECMP routes.
maximum load-balancing number
By default, the maximum number of RIP ECMP routes equals the maximum number of ECMP routes supported by the system.
Setting the RIP triggered update interval
About this task
Perform this task to avoid network overhead and reduce system resource consumption caused by frequent RIP triggered updates.
You can use the timer triggered command to set the maximum interval, minimum interval, and incremental interval for sending RIP triggered updates.
· For a stable network, the minimum-interval is used.
· If network changes become frequent, the incremental interval incremental-interval is used to extend the triggered update sending interval until the maximum-interval is reached.
Procedure
1. Enter system view.
system-view
2. Enter RIP view.
rip [ process-id ]
3. Set the RIP triggered update interval.
timer triggered maximum-interval [ minimum-interval [ incremental-interval ] ]
The default settings are as follows:
¡ The maximum interval is 5 seconds.
¡ The minimum interval is 50 milliseconds.
¡ The incremental interval is 200 milliseconds.
Configuring the RIP packet sending rate
About this task
Perform this task to set the interval for sending RIP packets and the maximum number of RIP packets that can be sent at each interval. This feature can avoid excessive RIP packets from affecting system performance and consuming too much bandwidth.
Procedure
1. Enter system view.
system-view
2. Configure the RIP packet sending rate.
¡ Execute the following commands in sequence to configure the RIP packet sending rate for all interfaces:
rip [ process-id ]
output-delay time count count
By default, an interface sends up to three RIP packets every 20 milliseconds.
¡ Execute the following commands in sequence to configure the RIP packet sending rate for an interface:
interface interface-type interface-number
rip output-delay time count count
By default, the interface uses the RIP packet sending rate configured for the RIP process that the interface runs.
Setting the maximum length of RIP packets
About this task
The packet length of RIP packets determines how many routes can be carried in a RIP packet. Set the maximum length of RIP packets to make good use of link bandwidth.
When authentication is enabled, follow these guidelines to ensure packet forwarding:
· For simple authentication, the maximum length of RIP packets must be no less than 52 bytes.
· For MD5 authentication (with packet format defined in RFC 2453), the maximum length of RIP packets must be no less than 56 bytes.
· For MD5 authentication (with packet format defined in RFC 2082), the maximum length of RIP packets must be no less than 72 bytes.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Set the maximum length of RIP packets.
rip max-packet-length value
By default, the maximum length of RIP packets is 512 bytes.
Configuring RIP network management
About this task
You can use network management software to manage the RIP process to which MIB is bound.
Procedure
1. Enter system view.
system-view
2. Bind MIB to a RIP process.
rip mib-binding process-id
By default, MIB is bound to the RIP process with the smallest process ID.
Configuring RIP GR
About this task
GR ensures forwarding continuity when a routing protocol restarts or an active/standby switchover occurs.
Two routers are required to complete a GR process. The following are router roles in a GR process:
· GR restarter—Graceful restarting router. It must have GR capability.
· GR helper—A neighbor of the GR restarter. It helps the GR restarter to complete the GR process.
After RIP restarts on a router, the router must learn RIP routes again and update its FIB table, which causes network disconnections and route reconvergence.
With the GR feature, the restarting router (known as the GR restarter) can notify the event to its GR capable neighbors. GR capable neighbors (known as GR helpers) maintain their adjacencies with the router within a GR interval. During this process, the FIB table of the router does not change. After the restart, the router contacts its neighbors to retrieve its FIB.
By default, a RIP-enabled device acts as the GR helper. Perform this task on the GR restarter.
Procedure
1. Enter system view.
system-view
2. Enter RIP view.
rip [ process-id ]
3. Enable GR for RIP.
graceful-restart
By default, RIP GR is disabled.
4. (Optional.) Set the GR interval.
graceful-restart interval interval
By default, the GR interval is 60 seconds.
Enhancing RIP security
Enabling zero field check for incoming RIPv1 messages
About this task
Some fields in the RIPv1 message must be set to zero. These fields are called "zero fields." You can enable zero field check for incoming RIPv1 messages. If a zero field of a message contains a non-zero value, RIP does not process the message. If you are certain that all messages are trustworthy, disable zero field check to save CPU resources.
This feature does not apply to RIPv2 packets, because they have no zero fields.
Procedure
1. Enter system view.
system-view
2. Enter RIP view.
rip [ process-id ]
3. Enable zero field check for incoming RIPv1 messages.
checkzero
By default, zero field check is disabled for incoming RIPv1 messages.
Enabling source IP address check for incoming RIP updates
About this task
Perform this task to enable source IP address check for incoming RIP updates.
· Upon receiving a message on an Ethernet interface, RIP compares the source IP address of the message with the IP address of the interface. If they are not in the same network segment, RIP discards the message.
· Upon receiving a message on a PPP interface, RIP checks whether the source address of the message is the IP address of the peer interface. If not, RIP discards the message.
Procedure
1. Enter system view.
system-view
2. Enter RIP view.
rip [ process-id ]
3. Enable source IP address check for incoming RIP messages.
validate-source-address
By default, source IP address check is disabled for incoming RIP updates.
Configuring RIPv2 message authentication
About this task
Perform this task to enable authentication on RIPv2 messages.
RIPv2 supports simple authentication and MD5 authentication.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Configure RIPv2 authentication.
rip authentication-mode { md5 { rfc2082 { cipher | plain } string key-id | rfc2453 { cipher | plain } string } | simple { cipher | plain } string }
By default, RIPv2 authentication is not configured.
RIPv1 does not support authentication. Although you can specify an authentication mode for RIPv1 in interface view, the configuration does not take effect.
Display and maintenance commands for RIP
Execute display commands in any view and execute reset commands in user view.
|
Command |
|
|
Display RIP current status and configuration information. |
display rip [ process-id ] |
|
Display RIP GR information. |
display rip [ process-id ] graceful-restart |
|
Display active routes in the RIP database. |
display rip process-id database [ ip-address { mask-length | mask } ] |
|
Display RIP interface information. |
display rip process-id interface [ interface-type interface-number ] |
|
Display neighbor information for a RIP process. |
display rip process-id neighbor [ interface-type interface-number ] |
|
Display routing information for a RIP process. |
display rip process-id route [ ip-address { mask-length | mask } [ verbose ] | peer ip-address | statistics ] |
|
Reset a RIP process. |
reset rip process-id process |
|
Clear the statistics for a RIP process. |
reset rip process-id statistics |
RIP configuration examples
Example: Configuring basic RIP
Network configuration
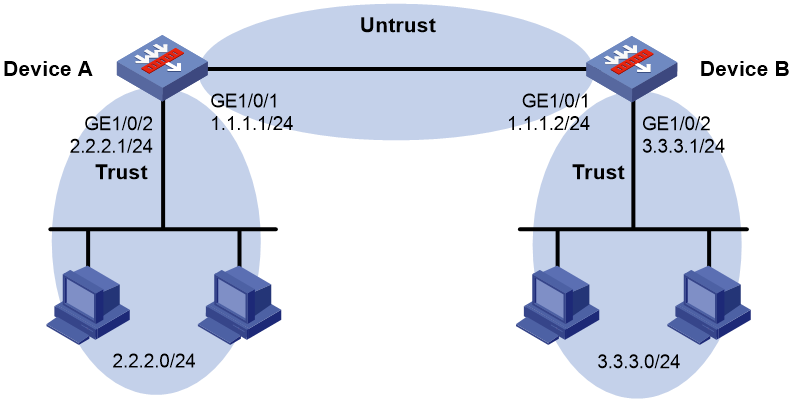
As shown in Figure 1, Device A and Device B are attached to networks 2.2.2.0/24 and 3.3.3.0/24, respectively. Configure RIPv2 on Device A and Device B to enable communication between the two networks.
Configuring Device A
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<DeviceA> system-view
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] ip address 1.1.1.1 255.255.255.0
[DeviceA-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Add interfaces to security zones.
[DeviceA] security-zone name untrust
[DeviceA-security-zone-Untrust] import interface gigabitethernet 1/0/1
[DeviceA-security-zone-Untrust] quit
[DeviceA] security-zone name trust
[DeviceA-security-zone-Trust] import interface gigabitethernet 1/0/2
[DeviceA-security-zone-Trust] quit
3. Configure security policies:
a. Configure a security policy to permit traffic between the Untrust and Local security zones, and enable the devices to establish RIP neighbor relationship with each other.
# Configure a rule named riplocalin to allow Device A to receive RIP packets from Device B.
[DeviceA] security-policy ip
[DeviceA-security-policy-ip] rule name riplocalin
[DeviceA-security-policy-ip-0-riplocalin] source-zone untrust
[DeviceA-security-policy-ip-0-riplocalin] destination-zone local
[DeviceA-security-policy-ip-0-riplocalin] service rip
[DeviceA-security-policy-ip-0-riplocalin] action pass
[DeviceA-security-policy-ip-0-riplocalin] quit
# Configure a rule named riplocalout to allow Device A to send RIP packets to Device B.
[DeviceA-security-policy-ip] rule name riplocalout
[DeviceA-security-policy-ip-1-riplocalout] source-zone local
[DeviceA-security-policy-ip-1-riplocalout] destination-zone untrust
[DeviceA-security-policy-ip-1-riplocalout] service rip
[DeviceA-security-policy-ip-1-riplocalout] action pass
[DeviceA-security-policy-ip-1-riplocalout] quit
b. Configure a security policy to permit traffic between the Trust and Untrust security zones, and enable communication between network 2.2.2.0/24 and network 3.3.3.0/24.
# Configure a rule named trust-untrust to permit packets from network 2.2.2.0/24 to network 3.3.3.0/24.
[DeviceA-security-policy-ip] rule name trust-untrust
[DeviceA-security-policy-ip-2-trust-untrust] source-zone trust
[DeviceA-security-policy-ip-2-trust-untrust] destination-zone untrust
[DeviceA-security-policy-ip-2-trust-untrust] source-ip-subnet 2.2.2.0 24
[DeviceA-security-policy-ip-2-trust-untrust] destination-ip-subnet 3.3.3.0 24
[DeviceA-security-policy-ip-2-trust-untrust] action pass
[DeviceA-security-policy-ip-2-trust-untrust] quit
# Configure a rule named untrust-trust to permit packets from network 3.3.3.0/24 to network 2.2.2.0/24.
[DeviceA-security-policy-ip] rule name untrust-trust
[DeviceA-security-policy-ip-3-untrust-trust] source-zone untrust
[DeviceA-security-policy-ip-3-untrust-trust] destination-zone trust
[DeviceA-security-policy-ip-3-untrust-trust] source-ip-subnet 3.3.3.0 24
[DeviceA-security-policy-ip-3-trust-untrust] destination-ip-subnet 2.2.2.0 24
[DeviceA-security-policy-ip-3-untrust-trust] action pass
[DeviceA-security-policy-ip-3-untrust-trust] quit
[DeviceA-security-policy-ip-3] quit
4. Configure basic RIP functions.
[DeviceA] rip
[DeviceA-rip-1] network 1.1.1.0
[DeviceA-rip-1] network 2.2.2.0
[DeviceA-rip-1] version 2
[DeviceA-rip-1] undo summary
[DeviceA-rip-1] quit
Configuring Device B
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<DeviceB> system-view
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ip address 1.1.1.2 255.255.255.0
[DeviceB-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Add interfaces to security zones.
[DeviceB] security-zone name untrust
[DeviceB-security-zone-Untrust] import interface gigabitethernet 1/0/1
[DeviceB-security-zone-Untrust] quit
[DeviceB] security-zone name trust
[DeviceB-security-zone-Trust] import interface gigabitethernet 1/0/2
[DeviceB-security-zone-Trust] quit
3. Configure security policies:
a. Configure a security policy to permit traffic between the Untrust and Local security zones, and enable the devices to establish RIP neighbor relationship with each other.
# Configure a rule named riplocalin to allow Device B to receive RIP packets from Device A.
[DeviceB] security-policy ip
[DeviceB-security-policy-ip] rule name riplocalin
[DeviceB-security-policy-ip-0-riplocalin] source-zone untrust
[DeviceB-security-policy-ip-0-riplocalin] destination-zone local
[DeviceB-security-policy-ip-0-riplocalin] service rip
[DeviceB-security-policy-ip-0-riplocalin] action pass
[DeviceB-security-policy-ip-0-riplocalin] quit
# Configure a rule named riplocalout to allow Device B to send RIP packets to Device A.
[DeviceB-security-policy-ip] rule name riplocalout
[DeviceB-security-policy-ip-1-riplocalout] source-zone local
[DeviceB-security-policy-ip-1-riplocalout] destination-zone untrust
[DeviceB-security-policy-ip-1-riplocalout] service rip
[DeviceB-security-policy-ip-1-riplocalout] action pass
[DeviceB-security-policy-ip-1-riplocalout] quit
b. Configure a security policy to permit traffic between the Trust and Untrust security zones, and enable communication between network 3.3.3.0/24 and network 2.2.2.0/24.
# Configure a rule named trust-untrust to permit packets from network 3.3.3.0/24 to network 2.2.2.0/24.
[DeviceB-security-policy-ip] rule name trust-untrust
[DeviceB-security-policy-ip-2-trust-untrust] source-zone trust
[DeviceB-security-policy-ip-2-trust-untrust] destination-zone untrust
[DeviceB-security-policy-ip-2-trust-untrust] source-ip-subnet 3.3.3.0 24
[DeviceB-security-policy-ip-2-trust-untrust] destination-ip-subnet 2.2.2.0 24
[DeviceB-security-policy-ip-2-trust-untrust] quit
# Configure a rule named untrust-trust to permit packets from network 2.2.2.0/24 to network 3.3.3.0/24.
[DeviceB-security-policy-ip] rule name untrust-trust
[DeviceB-security-policy-ip-3-untrust-trust] source-zone untrust
[DeviceB-security-policy-ip-3-untrust-trust] destination-zone trust
[DeviceB-security-policy-ip-3-untrust-trust] source-ip-subnet 2.2.2.0 24
[DeviceB-security-policy-ip-3-untrust-trust] destination-ip-subnet 3.3.3.0 24
[DeviceB-security-policy-ip-3-untrust-trust] action pass
[DeviceB-security-policy-ip-3-untrust-trust] quit
[DeviceB-security-policy-ip-3] quit
4. Configure basic RIP functions.
[DeviceB] rip
[DeviceB-rip-1] version 2
[DeviceB-rip-1] undo summary
[DeviceB-rip-1] quit
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] rip 1 enable
[DeviceB-GigabitEthernet1/0/1] quit
[DeviceB] interface gigabitethernet 1/0/2
[DeviceB-GigabitEthernet1/0/2] rip 1 enable
[DeviceB-GigabitEthernet1/0/2] quit
Verifying the configuration
# Display the RIP routing table of Device A.
[Device A] display rip 1 route
Route Flags: R - RIP, T - TRIP
P - Permanent, A - Aging, S - Suppressed, G - Garbage-collect
D - Direct, O - Optimal, F - Flush to RIB
----------------------------------------------------------------------------
Peer 1.1.1.2 on GigabitEthernet1/0/1
Destination/Mask Nexthop Cost Tag Flags Sec
3.3.3.0/24 1.1.1.1 1 0 RAOF 10
Local route
Destination/Mask Nexthop Cost Tag Flags Sec
2.2.2.0/24 0.0.0.0 0 0 RDOF -
1.1.1.0/24 0.0.0.0 0 0 RDOF -
The output shows that the hosts in network 2.2.2.0/24 can communicate with the hosts in network 3.3.3.0/24.