- Table of Contents
-
- 02-WLAN Configuration Guide
- 00-Preface
- 01-WLAN Interface Configuration
- 02-WLAN Access Configuration
- 03-WLAN Security Configuration
- 04-IACTP Tunnel and WLAN Roaming Configuration
- 05-WLAN RRM Configuration
- 06-WLAN IDS Configuration
- 07-WLAN QoS Configuration
- 08-WLAN Mesh Link Configuration
- 09-Advanced WLAN Configuration
- 10-WLAN High Availability Configuration
- 11-WLAN IPS Configuration
- 12-WLAN Optimization Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 11-WLAN IPS Configuration | 483.19 KB |
Wireless device classification
WLAN IPS configuration task list
Enabling WIPS for a hybrid sensor that provides access services
Importing and exporting OUI information
Configuring an AP classification rule
Configuring an attack detection policy
Configuring a malformed packet detection policy
Configuring a signature policy
Adding a MAC address to the permitted or prohibited device list
Configuring a permitted channel list
Configuring a virtual security domain
Disabling rogue wireless devices from accessing the WLAN
Adding the MAC address of a wireless device to the static countermeasures address list
Configuring a countermeasures policy
Configuring an alarm-ignored device list
Configuring the aging time for a wireless device
Configuring the information update interval for wireless devices
Configuring the wireless packet statistics sending interval
Configuring the interval to re-classify wireless devices
Configuring the aging time for WLAN mesh links
Enabling automatic WIPS log saving
Configuring the maximum size of WIPS logs
Enabling anti-denial-of-service
Configuring the WIPS device type for an AP
Enabling random MAC address filtering
Configuring the channel scanning list
Displaying and maintaining WLAN IPS
WLAN IPS configuration examples
Malformed packet detection configuration example
Signature configuration example
Configuring WIPS
Support for this feature depends on the device model. For more information, see About the H3C Access Controllers Configuration Guides.
Only the WA2600 series, WA3600 series, and WA2110-GN support this feature.
Overview
802.11 networks are susceptible to a wide array of threats such as interferences, attackers, rogue clients, and ambient wireless devices. Wireless intrusion prevention system (WIPS) protects enterprise networks and users against unauthorized wireless access according to user-defined security policies.
Terminology
Virtual security domain
You can divide a WLAN into multiple domains called virtual security domains. WIPS applies different security detection and protection policies for each virtual security domain.
Sensor
A sensor is an AP enabled with WIPS. It monitors WLAN channels and takes countermeasures against rogue devices.
A sensor can operate in the following modes:
· Monitor mode
One or more radios on a sensor provide WIPS services but do not provide access services.
· Hybrid mode
One or more radios on a sensor provide both WIPS and access services. A sensor operating in hybrid mode adopts one of the following policies:
¡ Access first—Long access duration, short WIPS monitoring duration, less packet loss, and good access efficiency. Poor detection and protection capabilities.
¡ Scanning first—Short access duration, long WIPS monitoring duration, more packet loss, and poor access efficiency. Good detection and protection capabilities.
¡ Balanced—Balanced between the access first and scanning first policies.
Permitted device list
A permitted device list contains MAC addresses of permitted APs or clients. The MAC address of a wireless device can be manually or dynamically added to the permitted device list. The dynamic mode is applicable to clients. When WIPS detects that a client is associated with an authorized AP through an encrypted authentication method, it adds the client to the permitted device list.
Static trusted OUI list
A static trusted OUI list contains the OUIs or vendors of trusted wireless devices. It is a supplementary to the permitted device list.
Prohibited device list
A prohibited device list contains the MAC addresses of prohibited APs or clients. WIPS prohibits APs or clients in the list from accessing the WLAN.
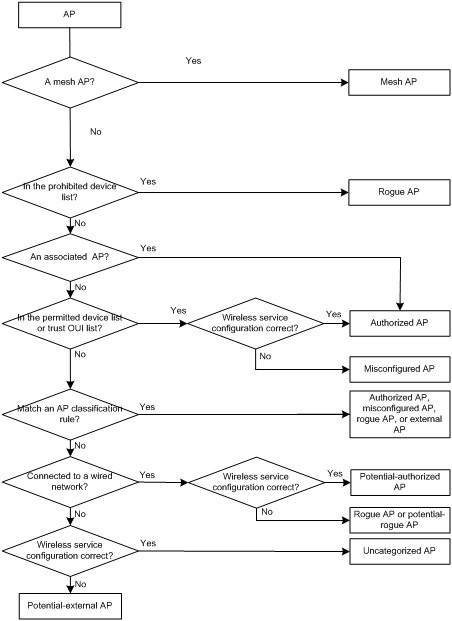
Misconfigured AP
WIPS uses wireless service information, such as SSID, cipher suite, security IE, and authentication method, configured on the AC as wireless service information. APs matching these policies are considered as correctly configured APs. Otherwise, they are considered as misconfigured APs.
Wireless device classification
WIPS identifies wireless devices by monitoring wireless packets and classifies them into different categories.
AP classification
WIPS classifies detected APs into the following types:
· Authorized AP—APs permitted in the WLAN. They can be APs that have been connected to the AC, APs in the permitted device list or static trusted OUI list that have correct wireless configuration, and APs manually specified through a user-defined AP classification rule.
· Rogue AP—APs that cannot be used in a wireless network. They can be APs in the prohibited device list, APs detected by WIPS that bring security threats to the network, manually specified rogue APs, or APs matching an AP classification rule.
· Misconfigured AP—APs that can be used in a wireless network but has wrong configurations. For example, an AP in the permitted device list but with a wrong SSID.
· External AP—APs in adjacent wireless networks. They do not bring any security problems to your network.
· Ad hoc—Wireless devices operating in Ad hoc mode. Ad hoc wireless devices can directly communicate with each other, which brings security problems to the network.
· Mesh AP—APs operating in a mesh network. Mesh APs can communicate with each other through wireless bridges. This might bring security problems to the WLAN.
· Potential-authorized AP—APs that are possibly authorized. If an AP is neither in the permitted device list, prohibited device list, or static trusted OUI list, but its wireless service configuration is correct and its wired port has been connected to the network, the AP is possibly an authorized AP, for example, a remote AP.
· Potential-rogue AP—APs that are possibly rogue APs. When an AP is neither in the permitted device list, prohibited device list, or trusted OUI list, and its wireless service configuration is incorrect:
¡ If its wired port might be connected to the network, the AP is a potential rogue AP.
¡ If its wired port has been connected to the network, the AP is a rogue AP, for example, an attacker AP.
· Potential-external AP—APs that are possibly external APs. If an AP is neither in the permitted device list, prohibited device list, or static trusted OUI list, and its wireless service configuration is correct and its wired port has not been connected to the network, the AP is possibly an external AP.
· Uncategorized AP—APs whose category cannot be determined.
WIPS classifies detected APs by following the procedure shown in Figure 1.
Figure 1 AP classification flow
Client classification
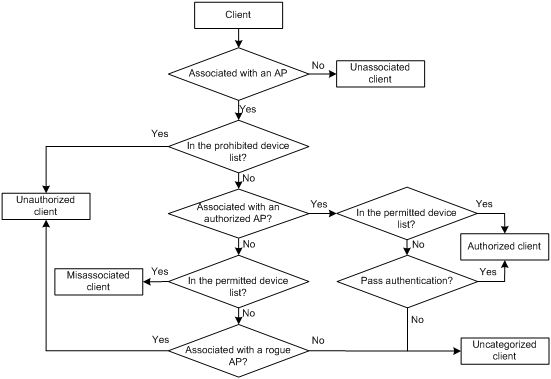
WIPS classifies detected clients into the following types:
· Authorized client—Clients permitted in the WLAN. For example, a client in the permitted device list associated with an authorized AP or a client associated with an authorized AP through an encrypted authentication method. The latter is also added to the permitted device list if authentication is enabled on the AP and non-WEP encryption mode is used.
· Unauthorized client—Clients that cannot be used in the WLAN. For example, a client in the prohibited device list or a client associated with a rogue AP.
· Misassociated client—A client that is in the permitted list but associated with an unauthorized AP. A permitted client can only associate with an authorized AP. A client associated with an unauthorized AP brings security threats to the network.
· Uncategorized client—A client whose category cannot be determined.
· Unassociated client—Clients not associated with any AP.
WIPS classifies detected clients by following the procedure shown in Figure 2.
Figure 2 Client classification flow
Wireless attack detection
WIPS detects attacks on a wireless network by listening to 802.11 frames and generates alarms to notify the administrator. WIPS supports detection of spoofing, Ad hoc network, prohibited channel, DoS attack, flood attack, and attacks to the WIPS system.
Spoofing attack detection
In a spoofing attack, the attacker sends frames on behalf of another device. For example, when a client in a WLAN has been associated with an AP and is operating correctly, a spoofed de-authentication frame can cause the client to get de-authenticated and affect the normal operation of the WLAN, a spoofed association frame can cause an authorized client to get associated or an authorized AP to associate with a spoofed client, resulting in account information leakage.
WIPS supports detection of AP spoofing and client spoofing attacks.
Ad hoc network detection
An Ad hoc network comprises clients that can directly communicate, so it is easy to be attacked. For example, if no data encryption method is applied to the clients in the network, client information will be leaked to attackers.
Prohibited channel detection
This function enables you to configure a permitted channel list so that WIPS can detect any prohibited channels not in the list.
DoS attack detection
WIPS considers attacks to the association tables of the wireless devices as DoS attacks. DoS attacks disable APs from processing client requests by taking advantage of vulnerabilities of WLAN protocols.
· Authentication DoS attacks
An authentication DoS attack floods the association table of an AP by imitating many clients sending authentication requests to the AP. When the number of entries in the table reaches the upper limit, the AP cannot process authentication requests from legitimate clients.
· Association/Reassociation DoS attacks
An association/reassociation DoS attack exhausts the client association table of an AP by flooding the AP with a large number of spoofed client associations so the AP cannot accept legitimate clients.
· EAPOL-Start DoS attacks
The IEEE 802.1X standard defines the authentication protocol using EAP over LANs (EAPOL). The 802.1X protocol starts with an EAPOL-Start frame sent by a client. Upon receiving the frame, the AP sends an EAP-Identity-Request and some internal resource allocation. An attacker can exhaust the AP's internal resources by flooding it with EAPOL-start frames.
Flooding attack detection
A flood attack refers to the case where WLAN devices receive large volumes of frames of the same kind within a short span of time. When this occurs, the WLAN devices get overwhelmed and are unable to service normal clients.
· Broadcast/unicast deauthentication flood
A broadcast/unicast deauthentication flood attack spoofs deauthentication frames from the AP to the associated clients to diassociate the clients from the AP. This form of attack is very effective and immediate in disrupting wireless services against multiple clients.
· Broadcast/unicast diassociation flood
A broadcast/unicast diassociation flood attack spoofs diassociation frames from the AP to the associated clients to diassociate the clients from the AP. This form of attack is very effective and immediate in disrupting wireless services against multiple clients.
· EAPOL-Logoff flood
The IEEE 802.1X standard defines the authentication protocol using Extensible Authentication Protocol (EAP) over LANs or EAPOL. When a client wants to logs off, the client sends an 802.1X EAPOL-logoff frame to terminate the session with the AP. The EAPOL-logoff frame is not authenticated, so an attacker can spoof this frame and log off the client. The attacker can continuously send the spoofed EAPOL-logoff frames to keep the client logged-off.
· EAP-Success/Failure flood
For an 802.1X-authenticated client, the AP sends an EAP-success frame to the client to indicate a successful authentication and sends an EAP-failure frame to indicate a failed authentication. An attacker continuously spoof EAP-success or EAP-failure frames to the client to disrupt the authentication state.
· PS-Poll flood
Power management is probably one of the most critical features of wireless LAN devices. During the sleep period of a client, the AP buffers data frames for the sleeping client and notifies the client that it has buffered the data. After the sleeping period, the client sends PS-Poll frames to the AP. For every PS-Poll frame, the AP sends a response. An attacker can flood PS-Poll frames to the AP. The AP then sends the buffered data frames to the client. If the client is in power save mode, the data frames will be discarded and the client cannot receive any data frames.
· AP flood
The Fake AP tool is a commonly used tool to protect your WLAN. The tool generates beacon frames imitating a large number of counterfeit APs to protect legitimate APs. However, this tool can cause problems such as bandwidth consumption, misleading legitimate clients, and interference with WIPS.
· RTS/CTS flood
An RTS/CTS attack takes advantage of vulnerabilities of the virtual carrier mechanism. Wireless denial of service (DoS) attacker may take advantage of the privilege granted to the CTS frame to reserve the RF medium for transmission. By transmitting back-to-back RTS frames with a large transmission duration text box, an attacker reserves the wireless medium and force other wireless devices sharing the RF medium to hold back their transmissions.
· BA flood
In a BA flood attack, the attacker sends an Add Block Acknowledgement (ADDBA) to the AP as a client. The sequence number and the size of the block in the ADDBA are changed. The AP will then drop any frames that fall outside of the range. Therefore, the sender cannot receive the data frames sent from the AP.
User-defined attack detection
This function allows you to configure signatures as needed to detect attacks.
Detection on attacks to WIPS
Attackers can send invalid packets to WIPS to increase processing costs or attack the internal tables of WIPS. WIPS can detect these attacks and reduce their impact by packet filtering and rate limit.
Invalid OUI detection
The OUI library of WIPS contains information about devices that have valid OUIs. Invalid OUI detection discovers devices whose OUIs are not in the library. You can classify these devices as rogue APs or unauthorized clients.
Weak IV detection
When the RC4 encryption algorithm, used by the WEP security protocol, uses an insecure IV, the WEP key is more likely to be cracked. Such an insecure IV is called a weak IV. WIPS prevents this kind of attack by detecting the IV of each WEP packet. When a weak IV is detected, WIPS generates an alarm to notify the administrator. You can configure a quiet time to avoid excessive weak IV alarms in a short period.
Hotspot attack detection
In a hotspot attack, a malicious AP attempts to lure a client to associate with it. Many enterprise employees use laptops in Wi-Fi area hotspots at airports and cafes to connect to their enterprise networks. The attacker sets up a rogue AP to lure the clients to associate with it. As long as the clients associate with the malicious AP, the attacker initiates a number of security attacks to the client. To detect this type of attacks, you can configure a hotspot list in WIPS. WIPS performs hotspot attack detection on the APs and trusted clients. When detecting a hotspot attack, WIPS generates an alarm. In addition, you can configure the quiet time after an alarm is generated to avoid generating power saving attack alarms.
Unencrypted device detection
An authorized AP or client that is transmitting unencrypted frames is a security risk. When detecting unencrypted frames from an authorized AP or a client associated with an authorized AP, WIPS generates alarms. In addition, you can configure the quiet time after an alarm is generated to avoid generating power saving attack alarms.
Power saving attack detection
In this attack, an attacker sends a NULL probe response to an AP. As a result, the AP considers that the client is in power saving mode, and caches the frame for the client. The client cannot obtain the frame because it is in power saving mode. The frame will be discarded after the aging time. WIPS identifies whether a power saving attack exists by determining the ratio of power-saving mode enabling frames to power-saving mode disabling frames. When detecting such an attack, WIPS generates an alarm. In addition, you can configure the quiet time after an alarm is generated to avoid generating power-saving attack alarms.
Windows bridging detection
When a wireless client establishes a Windows bridge connection with a wired NIC, the client can bridge an external AP with the internal network. This might bring security problems to the internal network. WIPS can detect whether a Windows bridge connection exists by analyzing data frames sent by associated clients. When detecting a Windows bridge, WIPS generates an alarm.
AP impersonation attack detection
An attacker installs a malicious AP that has the same BSSID and ESSID as a legitimate AP. Then this impersonating AP initiates man-in-the-middle and hotspot attacks, or fools the detection system. WIPS identifies whether such an attack occurs by detecting whether the number of Beacon frames sent by an AP in a specific period exceeds the upper limit. When detecting such an attack, WIPS generates an alarm. In addition, you can configure the quiet time after an alarm is generated to avoid generating power saving attack alarms.
Soft AP detection
A soft AP-enabled device can act as an AP to provide wireless services. Attackers can attack an internal network through soft AP-enabled devices. WIPS detects soft APs by determining the duration that a MAC address acts as a client and an AP. When detecting a soft AP, WIPS generates an alarm.
HT-greenfield AP detection
An AP operating in HT-greenfield mode might cause collisions, errors, and retransmissions because it cannot communicate with 802.11a/b/g devices. This feature enables WIPS to detect HT-greenfield APs and notify 802.11a/b/g devices to prevent these problems.
Honeypot AP detection
In a honeypot AP attack, the attacker sets up a malicious AP to lure clients to associate with it. The SSID of the malicious AP is similar to the SSID of a legitimate AP. After a client associates with a honeypot AP, the honeypot AP initiates further attacks such as port scanning or fake authentication to obtain client information.
WIPS detects honeypot APs by detecting SSIDs of external APs. If the similarity between the SSID of an external AP and the SSID of a legitimate AP reaches the specified threshold, WIPS generates an alarm.
Spoofed deauthentication frame attack detection
In a spoofed deauthentication frame attack, the attacker spoofs deauthentication frames to disassociate the clients from the legitimate AP.
WIPS detects spoofed deauthentication frame attacks by maintaining an association table for clients and legitimate APs. When detecting a spoofed deauthentication frame attack, WIPS generates an alarm.
MITM attack detection
In a Man In the Middle (MITM) attack, the attacker sets up a honeypot AP and initiates a spoofed deauthentication frame attack to make the client associate with it. Then it spoofs the client to associate with the authorized AP. When the client and the authorized AP communicate, the honeypot AP can sniff the exchanged packets.
WIPS detects MITM attacks by detecting honeypot APs and spoofed deauthentication frame attacks. When detecting an MITM attack, WIPS generates an alarm.
Detection on clients with the 40 MHz bandwidth mode disabled
802.11n devices support both the 20 MHz and 40 MHz bandwidth modes. If the 40 MHz bandwidth mode is disabled on a client, other clients associated with the same AP as the client must also use the 20 MHz bandwidth. This affects network throughput and efficiency.
WIPS detects such clients by detecting probe request frames sent by the clients. WIPS generates an alarm when it detects a client with the 40 MHz bandwidth mode disabled.
Wireless bridge detection
Attackers might intrude on the internal networks through a wireless bridge. When detecting a wireless bridge, WIPS generates an alarm. If the wireless bridge is in a mesh network, WIPS records the mesh link.
Malformed packet detection
With malformed packet detection, WIPS monitors wireless channels and obtains wireless packets through sensors, determines malformed packets, and classifies the detection results for generating alarms and logs. WIPS can detect 16 kinds of malformed packets.
Invalid IE length detection
This function is applicable to all management frames. An information element (IE) is a part of management frames and variable in length. An IE usually contains an Element ID bit, a Length bit, and a variable-length bit. Each type of management frame contains several specific IEs, and the value ranges for the IE lengths conform to the most recent 802.11 protocol. During the packet resolution process, when an IE with invalid length is detected, the packet is determined as a malformed packet.
Duplicate IE detection
This function is applicable to all management frames. During the packet resolution process, if a duplicate IE is detected, the packet is determined as a malformed packet. This detection is not applicable to vendor-defined IEs.
Redundant IE detection
This function is applicable to all management frames. During the packet resolution process, if an IE is neither a necessary IE to the packet nor a reserved IE, the packet is determined as a malformed packet.
Invalid packet length detection
This function is applicable to all management frames. After the packet payload is resolved, if the remaining length of the IE is not zero, the packet is determined as a malformed packet.
Abnormal IBSS and ESS setting detection
This function is applicable to beacon frames and probe response frames. If both the IBSS and ESS are set to 1, which is not defined in the 802.11 protocol, the packet is determined as a malformed packet.
Malformed authentication frame detection
This function is applicable to authentication frames. A packet is determined as a malformed packet when the following authentication failures occur:
· The authentication algorithm number does not conform to the 802.11 protocol and is larger than 3.
· The authentication transaction sequence number, indicating the authentication process between the client and the AP, is 1 and the status code is not 0.
· The authentication transaction sequence number is larger than 4.
Malformed association request frame detection
This function is applicable to association request frames. When the length of the SSID of an association request frame is 0, indicating that there is no SSID information for the AP to which the wireless client tries to associate, the access request fails, and the packet is determined as a malformed packet.
Malformed HT IE detection
This function is applicable to beacon, probe response, association response, and reassociation request frames. A packet is determined as a malformed packet when the following cases occur:
· The SM power save value of the HT capabilities IE is 2, which is a reserved value in the protocol and is meaningless.
· The secondary channel offset value of the HT operation IE is 2, which is a reserved value in the protocol and is meaningless.
Oversized duration detection
This function is applicable to unicast management frames, unicast data frames, RTS, CTS, and ACK frames. It is related to the malformed packet detection policy applied in a virtual security domain. You can configure a duration threshold, which is automatically sent to the sensor. If the value of the packet duration is larger than the threshold, the packet is determined as a malformed packet. The default value of the threshold is 5000 μs.
Malformed probe response frame detection
This function is applicable to probe response frames. If the frame is not a mesh frame and its SSID length is 0 (the protocol defines that a frame with an SSID value of 0 is a mesh frame), the packet is determined as a malformed packet.
Invalid deauthentication code detection
This function is applicable to deauthentication frames. When the reason code of a deauthentication frame is 0 or is in the range of 67 to 65535, which is a reserved value and meaningless, the packet is determined as a malformed packet.
Invalid disassociation code detection
This function is applicable to disassociation frames. When the reason code of a disassociation frame is 0 or is in the range of 67 to 65535, which is a reserved value and meaningless, the packet is determined as a malformed packet.
Oversized SSID detection
This function is applicable to beacon, probe request, probe response, and association request frames. When the length of the SSID of a packet is larger than 32, the packet is determined as a malformed packet.
Fata-jack detection
This function is applicable to authentication frames. When the value of the authentication algorithm number is 2, the packet is determined as a malformed packet. Though the 802.11 protocol (2012) defines that the value 2 refers to fast BSS transition, WIPS conforms to the former definition of fata-jack packets.
Invalid source address detection
This function is applicable to all management frames. When the TO DS of a frame is 1, indicating that the frame is sent to the AP by a client, but the source MAC address is a multicast or broadcast address, the packet is determined as a malformed packet.
Oversized eapol key detection
This function is applicable to EAPOL frames. When the TO DS of a frame is 1, and the length of the key is larger than 0, the packet is determined as a malformed packet. A malicious EAPOL frame with abnormal key length might result in DOS attacks.
Invalid channel detection
This function is applicable to beacon frames. When the channel ID in a beacon frame is not in the channel ID range available for the current radio mode, the beacon frame is determined as a malformed packet.
WIPS networking
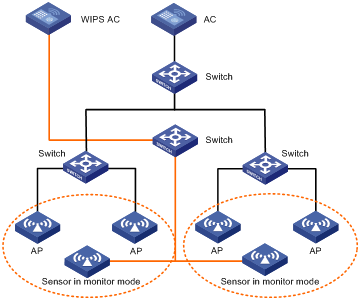
WIPS can operate independently or in an existing WLAN.
As an overlay (Independent operation)
ACs and sensors operating in hybrid mode form a WIPS network, as shown in Figure 3. The WIPS network is independent of the wireless network to be protected.
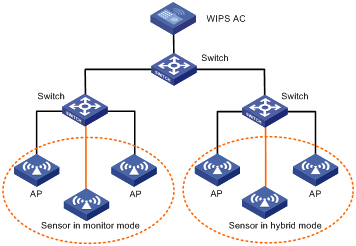
Integrated (Operating in an existing WLAN)
You can deploy WIPS in an existing WLAN by adding sensors operating in monitor mode, or by configuring APs as sensors operating in hybrid mode, as shown in Figure 4.
WLAN IPS configuration task list
|
Task |
Remarks |
|
Required. |
|
|
Required. |
|
|
Enabling WIPS for a hybrid sensor that provides access services |
Optional. |
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Adding a MAC address to the permitted or prohibited device list |
Optional. |
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Configuring the information update interval for wireless devices |
Optional. |
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Optional. |
|
|
Optional. |
Enabling WIPS
If you only enable WIPS, but do not configure WIPS functions, the system can only detect devices about their basic information such as statistics and classification in the WLAN.
WIPS cannot operate correctly if 802.11w management frame protection is enabled on clients.
To enable WIPS:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Enable WIPS. |
wips enable |
By default, WIPS is disabled. |
Configuring a sensor
To configure the operating mode for a sensor:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter AP template view. |
wlan ap ap-name model model-name |
N/A |
|
3. Enter radio view. |
radio radio-number [ type { dot11a | dot11an | dot11b | dot11g | dot11gn } ] |
The default setting of this command varies by AP model. |
|
4. Configure the operating mode of the sensor. |
wips detect mode { access-first | access-only [ scan-time time-value ] | detect-first | detect-only | middle } |
By default, no operating mode is configured for the sensor. If a radio is configured as a sensor in monitor mode, you cannot bind a wireless service or mesh service to the radio. You must bind a hybrid sensor to a service template. Otherwise, WIPS does not function. If you specify the access-only keyword for this command, the AP provides access services and scans only the working channel. When the AP is working on hybrid mode, it can only countermeasure at the same channel where it provides the wireless access service. For example, if the AP is configured to broadcast the SSID at channel 6, then it can only countermeasure the suspicious devices at channel 6. |
To configure the scanning mode for a sensor:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RRM view. |
wlan rrm |
N/A |
|
3. Configure the scanning mode of the sensor. |
scan channel { auto | all } |
Optional. By default, the scanning mode of the sensor is auto. WIPS only scans channels supported by the country code of the sensor. For more information about this command, see WLAN RRM Command Reference. |
Enabling WIPS for a hybrid sensor that provides access services
This feature improves WIPS detection and attack prevention performance, but decreases access performance of the sensor.
To enable WIPS for a hybrid sensor that provides access services:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Enable WIPS for a hybrid sensor that provides access services. |
detect access-flow-scan enable |
Optional. By default, a hybrid sensor does not perform WIPS scanning when it is providing access services. |
Importing and exporting OUI information
An Organizational Unique Identifier (OUI) is the first three bytes of the MAC address of a device. It is the vendor identification of the device.
An AC automatically imports a standard OUI file to the OUI library of WIPS after bootup. You can also write the OUI information in standard OUI file format to a configuration file, and execute the import wips-cfg-file oui command to import the configuration file to the OUI library of WIPS.
After you successfully import the configuration file, the system displays the numbers of imported, updated, and existing configuration files, and the number of configuration files failed to be imported.
In addition, you can execute the export wips-cfg-file oui command to export the OUI information in the OUI library to a configuration file. The system displays the numbers of successful and failed export operations.
To import/export OUI information from/to a configuration file or clear OUI configuration information:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Import OUI information from a configuration file. |
import wips-cfg-file oui [ file-name ] |
By default, WIPS automatically imports OUI information to the OUI library of WIPS. |
|
4. Export OUI information to a configuration file. |
export wips-cfg-file oui file-name |
By default, no OUI information will be exported from the OUI library of WIPS. |
|
5. Clear OUI information in the OUI library. |
undo wips-cfg-file oui |
Optional. By default, OUI information in the OUI library is not cleared. |
Configuring a hotspot list
You can add hotspot SSIDs to a hotspot list to enable WIPS to detect attacks to the hotspots.
To configure a hotspot list:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Add a hotspot list. |
hotspot ssid-name |
By default, no hotspot list exists. |
Configuring an AP classification rule
Perform this task to configure AP classification rules. You can specify a type or severity level for APs matching a classification rule.
AP severity levels indicate the impact of potential-authorized APs, potential-rogue APs, potential-external APs, or unrecognized APs to the WLAN. A higher severity level indicates more serious impact to the WLAN.
If multiple AP classification rules exist, you can specify their precedence. WIPS matches the rules in the order of their precedence. When a match is found, WIPS takes one of the following actions:
· If you have configured the AP type in the rule, WIPS assigns the detected AP to this type.
· If you have not configured the AP type in the rule, WIPS assigns the severity level to the detected AP.
To configure an AP classification rule:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Create an AP classification rule. |
ap-classification-rule rule-name |
By default, no AP classification rule exists. |
|
4. Specify the type of the AP that matches the classification rule. |
classify-type { authorized-ap | external-ap | misconfigured-ap | rogue-ap } |
Use either command. By default, neither AP type nor severity level is specified for an AP classification rule. The severity level is configurable only when no AP type is specified for the AP classification rule. |
|
5. Configure the severity level for the AP that matches the classification rule. |
severity-level level-value |
|
|
6. Match all the criteria in the classification rule. |
match all |
Optional. By default, an AP is considered as matching an AP classification rule as long as it matches any match criterion of the rule. |
|
7. Match a specified SSID. |
sub-rule ssid [ case-sensitive ] [ not ] { equal | include } string |
Optional. By default, no ssid subsignature is configured. |
|
8. Match an authentication method. |
sub-rule authentication { equal | include } { 802.1x | psk | other | none } |
Optional. By default, no match criterion is configured. |
|
9. Match a security method. |
sub-rule security { equal | include } { clear | wep | wpa | wpa2 }* |
Optional. By default, no match criterion is configured. |
|
10. Match an RSSI value. |
sub-rule rssi { greater-than min-value | less-than max-value | between min-value max-value } |
Optional. By default, no match criterion is configured. |
|
11. Match the AP duration. |
sub-rule duration { greater-than min-value | less-than max-value | between min-value max-value } |
Optional. By default, no match criterion is configured. |
|
12. Match number of associated clients. |
sub-rule client-on-ap { greater-than min-value | less-than max-value | between min-value max-value } |
Optional. By default, no match criterion is configured. |
|
13. Match number of detected APs by the current sensor. |
sub-rule discovered-ap { greater-than min-value | less-than max-value | between min-value max-value } |
Optional. By default, no match criterion is configured. |
|
14. Match OUIs or vendors. |
sub-rule oui { oui-info | vendor vendor-name } |
Optional. By default, no match criterion is configured. |
Configuring an attack detection policy
You can apply different attack detection policies to different virtual security domains as needed.
To configure an attack detection policy:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Configure an attack detection policy. |
attack-detect-policy policy-name |
By default, an attack detection policy named default exists in the system. You cannot create or delete a default attack detection policy. |
|
4. Enable Ad hoc network detection. |
detect adhoc-network |
Optional. By default, Ad hoc network detection is disabled. |
|
5. Enable AP MAC address spoofing detection. |
detect ap-spoofing [ quiet-time time-value ] |
Optional. By default, AP MAC address spoofing detection is disabled. |
|
6. Enable client MAC address spoofing detection. |
detect client-spoofing [ quiet-time time-value ] |
Optional. By default, client MAC address spoofing detection is disabled. |
|
7. Enable prohibited channel detection. |
detect prohibited-channel [ action classify rogue ] |
Optional. By default, prohibited channel detection is disabled. |
|
8. Enable association DoS attack detection. |
detect dos-association [ quiet-time time-value ] |
Optional. By default, association DoS attack detection is disabled. |
|
9. Enable reassociation DoS attack detection. |
detect dos-reassociation [ quiet-time time-value ] |
Optional. By default, reassociation DoS attack detection is disabled. |
|
10. Enable authentication DoS attack detection. |
detect dos-authentication [ quiet-time time-value ] |
Optional. By default, authentication DoS attack detection is disabled. |
|
11. Enable EAPOL-Start DoS attack detection. |
detect dos-eapol-start [ quiet-time time-value ] |
Optional. By default, EAPOL-Start DoS attack detection is disabled. |
|
12. Enable AP flooding detection. |
detect ap-flood [ quiet-time time-value ] |
Optional. By default, AP flooding detection is disabled. |
|
13. Enable weak IV detection. |
detect weak-iv [ quiet-time time-value ] |
Optional. By default, weak IV detection is disabled. |
|
14. Enable invalid OUI detection, and classify the detected devices. |
detect invalid-oui [ action classify rogue ] |
Optional. By default, invalid OUI detection is disabled. |
|
15. Enable hotspot attack detection. |
detect hotspot-attack [ action classify rogue ] |
Optional. By default, hotspot attack detection is disabled. |
|
16. Enable unencrypted AP detection. |
detect unencrypted-authorized-ap [ quiet-time quiet-time-value ] |
Optional. By default, unencrypted AP detection is disabled. |
|
17. Enable power saving attack detection. |
detect ps-attack [ quiet-time quiet-time-value | threshold { minoffpacket minoffpacket-value | onoffpercent onoffpercent-value }* ]* |
Optional. By default, power saving attack detection is disabled. |
|
18. Enable Windows bridge detection. |
detect windows-bridge |
Optional. By default, Windows bridge detection is disabled. |
|
19. Enable AP impersonation detection. |
detect ap-impersonation [ quiet-time time-value | beacon-inc-threshold beacon-inc-threshold-value | beacon-inc-wait-time beacon-inc-wait-time-value ]* |
Optional. By default, AP impersonation detection is disabled. |
|
20. Enable soft AP detection. |
detect soft-ap [ convert-time convert-time-value ]* |
Optional. By default, soft AP detection is disabled. |
|
21. Enable unencrypted client detection. |
detect unencrypted-trust-client [ quiet-time quiet-time-value ] |
Optional. By default, unencrypted client detection is disabled. |
|
22. Enable HT-greenfield AP detection. |
detect ht-greenfield [ quiet-time quiet-time-value ] |
Optional. By default, HT-greenfield AP detection is disabled. |
|
23. Enable honeypot AP detection. |
detect honeypot-ap [ quiet-time time-value | similarity similarity-value ]* [ action classify rogue ] |
Optional. By default, honeypot AP detection is disabled. |
|
24. Enable spoofed deauthentication frame detection. |
detect deauth-spoofing |
Optional. By default, spoofed deauthentication frame detection is disabled. |
|
25. Enable detection on clients with the 40 MHz bandwidth mode disabled. |
detect ht-40mhz-intolerance [ quiet-time time-value ] |
Optional. By default, detection on clients with the 40 MHz bandwidth mode disabled is disabled. |
|
26. Enable wireless bridge detection. |
detect wireless-bridge [ quiet-time time-value ] |
Optional. By default, wireless bridge detection is disabled. |
|
27. Enable all detections in the current attack detection policy. |
detect all |
Optional. By default, all-detection is disabled. |
Configuring a malformed packet detection policy
This task allows you to configure different malformed packet detection policies for different virtual security domains as needed.
To configure a malformed packet detection policy:
|
Step |
Command |
Remarks |
|
|
1. Enter system view. |
system-view |
N/A |
|
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
|
3. Configure a malformed packet detection policy. |
malformed-detect-policy policy-name |
By default, a malformed packet detection policy named default exists in the system. You cannot create or delete the default malformed packet detection policy. |
|
|
4. Configure the quiet time before WIPS can detect the next malformed packet. |
quiet-time time-value |
Optional. By default, the quiet time is 600 seconds. |
|
|
5. Configure the sensor to send a log or alarm to the AC when it detects invalid IE length. |
detect invalid-ie-length action { log | trap }* |
Optional. By default, the sensor does not send a log or alarm when it detects invalid IE length. |
|
|
6. Configure the sensor to send a log or alarm to the AC when it detects a duplicate IE. |
detect duplicated-ie action { log | trap }* |
Optional. By default, the sensor does not send a log or alarm when it detects a duplicate IE. |
|
|
7. Configure the sensor to send a log or alarm to the AC when it detects a redundant IE. |
detect redundant-ie action { log | trap }* |
Optional. By default, the sensor does not send a log or alarm when it detects a redundant IE. |
|
|
8. Configure the sensor to send a log or alarm to the AC when it detects invalid packet length. |
detect invalid-pkt-length action { log | trap }* |
Optional. By default, the sensor does not send a log or alarm when it detects invalid packet length. |
|
|
9. Configure the sensor to send a log or alarm to the AC when it detects abnormal IBSS or ESS setting. |
detect illegal-ibss-ess action { log | trap }* |
Optional. By default, the sensor does not send a log or alarm when it detects abnormal IBSS or ESS setting. |
|
|
10. Configure the sensor to send a log or alarm to the AC when it detects an oversized key in an EAPOL frame. |
detect overflow-eapol-key action { log | trap }* |
Optional. By default, the sensor does not send a log or alarm when it detects an oversized key in an EAPOL frame. |
|
|
11. Configure the sensor to send a log or alarm to the AC when it detects a malformed authentication frame. |
detect malformed-auth action { log | trap }* |
Optional. By default, the sensor does not send a log or alarm when it detects a malformed authentication frame. |
|
|
12. Configure the sensor to send a log or alarm to the AC when it detects a malformed association request frame. |
detect malformed-assoc-req action { log | trap }* |
Optional. By default, the sensor does not send a log or alarm when it detects a malformed association request frame. |
|
|
13. Configure the sensor to send a log or alarm to the AC when it detects a malformed HT IE. |
detect malformed-ht-ie action { log | trap }* |
Optional. By default, the sensor does not send a log or alarm when it detects a malformed HT IE. |
|
|
14. Configure the sensor to send a log or alarm to the AC when it detects an oversized duration. |
detect large-duration { threshold time| action { log | trap }*}* |
Optional. By default, the sensor does not send a log or alarm when it detects an oversized duration. |
|
|
15. Configure the sensor to send a log or alarm when it detects a null SSID in a probe response frame. |
detect null-probe-resp action { log | trap }* |
Optional. By default, the sensor does not send a log or alarm when it detects a null SSID in a probe response frame. |
|
|
16. Configure the sensor to send a log or alarm when it detects an invalid deauthentication reason code. |
detect invalid-deauth-code action { log | trap }* |
Optional. By default, the sensor does not send a log or alarm when it detects an invalid deauthentication reason code. |
|
|
17. Configure the sensor to send a log or alarm when it detects an invalid disassociation reason code. |
detect invalid-disassoc-code action { log | trap }* |
Optional. By default, the sensor does not send a log or alarm when it detects an invalid disassociation reason code. |
|
|
18. Configure the sensor to send a log or alarm when it detects an oversized SSID. |
detect overflow-ssid action { log | trap }* |
Optional. By default, the sensor does not send a log or alarm when it detects an oversized SSID. |
|
|
19. Configure the sensor to send a log or alarm when it detects a FATA Jack attack. |
detect fata-jack action { log | trap }* |
Optional. By default, the sensor does not send a log or alarm when it detects a FATA Jack attack. |
|
|
20. Configure the sensor to send a log or alarm when it detects an authentication/association request frame with a broadcast or multicast source address. |
detect invalid-source-address action { log | trap }* |
Optional. By default, the sensor does not send a log or alarm when it detects an authentication/association request frame with a broadcast or multicast source address. |
|
|
21. Configure the sensor to send a log or alarm when it detects an invalid channel ID. |
detect invalid-channel action { log | trap }* |
Optional. By default, the sensor does not send a log or alarm when it detects an invalid channel ID. |
|
|
22. Configure the sensor to send a log or alarm when it detects a malformed packet of any type specified in the policy. |
detect all action { log | trap }* |
Optional. By default, the sensor does not send a log or alarm when it detects a malformed packet of some types. |
|
Configuring a signature
A signature contains a packet identification method and actions to take on the matching packets. WIPS applies signatures in a signature policy to virtual security domains. The sensors in the virtual security domains match the detected packets against the signatures in descending order of precedence. If a match is found, a sensor takes actions defined in the signature and stops matching other signatures.
Signatures include system-defined and user-defined signatures.
System-defined signatures
WIPS has predefined signatures to detect flood attacks shown in Table 1. All system-defined signatures, including subsignatures, subsignature matching methods, tracking and handling methods cannot be configured. An AP is considered as matching a system-defined signature when it matches all the match criteria of the signature and WIPS generates alarms when a match is found.
When WIPS detects a flood attack from a MAC address, it adds the MAC address to the dynamic blacklist if the MAC address is a client.
You can only configure the statistics collection period, maximum matching times within a statistics collection period, quiet time, and alarm level for system-defined signatures, including subsignatures, subsignature matching methods, tracking and handling methods cannot be configured.
Table 1 System-defined signatures
|
Signature ID |
Signature name |
Description |
Remarks |
|
1 |
deauth_flood |
Detects unicast deauthentication flood. |
By default, the tracking method is per-mac, statistics collection period is 10 seconds, the maximum matching times within the statistics collection period is 10, and the quiet time is 900 seconds. |
|
2 |
broadcast_deauth_flood |
Detects broadcast deauthentication flood. |
By default, the track method is per-mac, statistics collection period is 10 seconds, the maximum matching times is 5, and the quiet time is 900 seconds. |
|
3 |
disassoc_flood |
Detects unicast diassociation flood. |
By default, the track method is per-mac, statistics collection period is 10 seconds, the maximum matching times is 10, and the quiet time is 900 seconds. |
|
4 |
broadcast_disassoc_flood |
Detects broadcast diassociation flood. |
By default, the track method is per-mac, statistics collection period is 10 seconds, the maximum matching times is 5, and the quiet time is 900 seconds. |
|
5 |
eapol_logoff_flood |
Detects EAPOL-Logoff flood. |
By default, the track method is per-mac, statistics collection period is 3 seconds, the maximum matching times is 60, and the quiet time is 900 seconds. |
|
6 |
eap_success_flood |
Detects EAP-Success flood. |
By default, the track method is per-mac, statistics collection period is 3 seconds, the maximum matching times is 60, and the quiet time is 900 seconds. |
|
7 |
eap_failure_flood |
Detects EAP-Failure flood. |
By default, the track method is per-mac, statistics collection period is 3 seconds, the maximum matching times is 60, and the quiet time is 900 seconds. |
|
8 |
pspoll_flood |
Detects PS-Poll flood. |
By default, the track method is per-mac, statistics collection period is 5 seconds, the maximum matching times is 1000, and the quiet time is 900 seconds. |
|
9 |
cts_flood |
Detects CTS flood. |
By default, the track method is per-mac, statistics collection period is 5 seconds, the maximum matching times is 5000, and the quiet time is 900 seconds. |
|
10 |
rts_flood |
Detects RTS flood. |
By default, the track method is per-mac, statistics collection period is 5 seconds, the maximum matching times is 5000, and the quiet time is 900 seconds. |
Configuring a signature
To configure a signature:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Create a signature. |
signature { rts flood | cts flood | pspoll flood | eap failure flood | eap success flood | eapol logoff flood | broadcast disassoc flood | disassoc flood | broadcast deauth flood | deauth flood | addba req flood | signature-name } [ signature-id id-value ] |
By default, system-defined signatures exist. |
|
4. Configure a track method for the signature. |
track-method { both | per-mac | per-signature } |
Optional. By default, the track method for user-defined signatures is both and the track method for system-defined signatures depends on specific signature. |
|
5. Configure the statistics collection period for the signature. |
detect-period period-time |
Optional. By default, the statistics collection period for a user-defined signature is 60 seconds and the statistics collection period for a system-defined signature depends on the specific system-defined signature. |
|
6. Configure the maximum matching times for the signature within the specified statistics collection period. |
detect-threshold { per-mac number | per-signature number } |
Optional. By default, the maximum matching times for a user-defined signature is 1000 and that for a system-defined signature depends on the specific system-defined signature. |
|
7. Specify the action for the signature. |
action { none | report event-level level-value } |
Optional. By default, the action for a user-defined signature is none, the action for a system-defined signature is report, and the alarm level depends on the signature. |
|
8. Configure the quiet time for the signature. |
quiet-time time |
Optional. By default, the quiet time for a user-defined signature is 900 seconds and that for a system-defined signature depends on the specific system-defined signature. |
|
9. Match all the criteria in the signature. |
match all |
Optional. By default, a packet is considered as matching a user-defined signature as long as it matches any match criterion of the signature. A packet is considered as matching a system-defined signature when it matches all match criteria of the signature. |
|
10. Match a frame type. |
sub-rule frame-type { data | management [ frame-subtype { association-request | association-response | authentication | beacon | deauthentication | disassociation | probe-request } ] | control } |
Optional. By default, no match criterion is configured. |
|
11. Match a MAC address. |
sub-rule mac { source-mac mac-address | dest-mac mac- address | bssid mac-address } |
Optional. By default, no match criterion is configured. |
|
12. Match an SSID. |
sub-rule ssid { [ case-sensitive ] [ not ] { equal | include } string } |
Optional. By default, no match criterion is configured. |
|
13. Match the SSID length. |
sub-rule ssid-length { equal length-value | greater-than min-value | less-than max-value | between min-value max-value } |
Optional. By default, no match criterion is configured. |
|
14. Match sequence numbers. |
sub-rule seq-number { equal seq-value | greater-than min-value | less-than max-value | between min-value max-value } |
Optional. By default, no match criterion is configured. |
|
15. Match a pattern subsignature for the signature. |
sub-rule pattern pattern-id id [ pattern-name name ] offset offset-value mask hex-value { equal value | greater-than min-value | less-than max-value | between min-value max-value } [ from-payload ] |
Optional. By default, no match criterion is configured. |
Configuring a signature policy
A signature policy contains a set of signatures. You can configure signature policies and apply them to different virtual security domains as needed.
To configure a signature policy:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Configure a signature policy. |
signature-policy policy-name |
By default, a virtual security domain uses the signature policy named default. You cannot create or delete the default signature policy. |
|
4. Add a configured signature. |
signature { signature-name name-string | signature-id signature-list } [ precedence level ] |
Optional. By default, no signature exists in a signature policy. |
Adding a MAC address to the permitted or prohibited device list
You can add the MAC addresses of APs or clients to a permitted or prohibited device list, or add OUI or vendor information of APs to the static trusted OUI list to control wireless access.
To add a MAC address to the permitted or prohibited device list:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Add a MAC address to the permitted device list. |
static-trustlist mac-address |
By default, no device is added to the permitted device list. |
|
4. Add OUI or vendor information to the static trusted OUI list. |
static-trustoui { oui-info | vendor vendor-name } |
Optional. By default, no OUI or vendor information is added to the static trusted OUI list. |
|
5. Add a MAC address to the prohibited device list. |
static-blocklist mac-address |
By default, no device is added to the prohibited device list. |
|
6. Set the aging time for the wireless devices dynamically added to the trusted device list. |
timer dynamic-trustlist-aging time |
Optional. By default, the aging time is 300 seconds. |
Configuring a permitted channel list
You can configure a permitted channel list in a WLAN, so WIPS will generate alarms when detecting packet transmission on any channel not in the permitted channel list.
To configure a permitted channel list:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Configure a permitted channel list. |
permit-channel channel-list |
By default, channels allowed by the current country code are permitted channels. Use the permit-channel command in combination with the detect prohibited-channel command. The permit-channel command takes effect only after prohibited channel detection is enabled. |
Configuring a virtual security domain
You can configure multiple virtual security domains in a WLAN and apply different attack detection policies, AP classification rules, and signature policy to each domain.
To configure a virtual security domain:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Configure a virtual security domain. |
virtual-security-domain vsd-name |
By default, the virtual security domain default is used as the default virtual security domain. You cannot create or remove it. |
|
4. Specify sensors for the virtual security domain. |
sensor ap-name-list |
By default, all sensors are in the default virtual security domain. |
|
5. Configure an attack detection policy for the virtual security domain. |
attack-detect-policy policy-name |
Optional. By default, a virtual security domain uses the attack detection policy named default. |
|
6. Configure a malformed packet detection policy for the virtual security domain. |
malformed-detect-policy policy-name |
Optional. By default, a virtual security domain uses the malformed packet detection policy named default. |
|
7. Configure an AP classification rule for the virtual security domain. |
ap-classification-rule rule-name [ precedence number ] |
Optional. By default, no AP classification rule exists in a virtual security domain. |
|
8. Configure a signature policy for the virtual security domain. |
signature-policy policy-name |
Optional. By default, a virtual security domain uses the attack detection policy named default. |
|
9. Configure a countermeasures policy for the virtual security domain. |
countermeasure-policy policy-name |
Optional. By default, a virtual security domain uses the countermeasures policy named default. |
Configuring countermeasures
WIPS can take the following countermeasures against rogue APs or clients.
· Preventing rogue clients.
· Informing sensors to diassociate rogue wireless devices.
· Disable wireless devices in the prohibited device list from accessing the WLAN.
WIPS supports the first two ways.
Disabling rogue wireless devices from accessing the WLAN
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Disable wireless devices in the prohibited device list from accessing the WLAN. |
blocklist-action block |
By default, wireless devices in the blacklist are allowed to access the WLAN. |
Adding the MAC address of a wireless device to the static countermeasures address list
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Add the MAC address of a wireless device to the static countermeasures address list. |
countermeasure static mac-address |
By default, no countermeasures are taken against wireless devices. When you add a wireless device to the static countermeasures address list, all virtual security domains take countermeasures against the device. |
Configuring a countermeasures policy
A countermeasures policy applied to a virtual security domain takes countermeasures against the wireless devices in the static countermeasures list defined by the policy.
To configure a countermeasures policy:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Configure a countermeasures policy. |
countermeasure-policy policy-name |
By default, a countermeasures policy named default list exists. The default policy cannot be manually created or deleted. |
|
4. Take countermeasures against wireless devices on a fixed channel. |
countermeasure fixed-channel enable |
By default, no countermeasures are taken against wireless devices on a fixed channel. The sensor stops scanning on other channels when it is taking countermeasures on a fixed channel. |
|
5. Take countermeasures against rogue APs. |
countermeasure rogue-ap [ precedence number ] |
By default, no countermeasures are taken against rogue APs. |
|
6. Take countermeasures against potential-rogue APs. |
countermeasure potential-rogue-ap [ precedence number ] |
By default, no countermeasures are taken against potential-rogue APs. |
|
7. Take countermeasures against misconfigured APs. |
countermeasure misconfigured-ap [ precedence number ] |
By default, no countermeasures are taken against misconfigured APs. |
|
8. Take countermeasures against external APs. |
countermeasure external-ap [ precedence number ] |
By default, no countermeasures are taken against external APs. |
|
9. Take countermeasures against potential-external APs. |
countermeasure potential-external-ap [ precedence number ] |
By default, no countermeasures are taken against potential-external APs. |
|
10. Take countermeasures against uncategorized APs. |
countermeasure uncategorized-ap [ precedence number ] |
By default, no countermeasures are taken against uncategorized APs. |
|
11. Take countermeasures against potential-authorized APs. |
countermeasure potential-authorized-ap [ precedence number ] |
By default, no countermeasures are taken against potential-authorized APs. |
|
12. Take countermeasures against misassociated clients. |
countermeasure misassociation-client [ precedence number ] |
By default, no countermeasures are taken against misassociated clients. |
|
13. Take countermeasures against uncategorized clients. |
countermeasure uncategorized-client [ precedence number ] |
By default, no countermeasures are taken against uncategorized clients. |
|
14. Take countermeasures against unauthorized clients. |
countermeasure unauthorized-client [ precedence number ] |
By default, no countermeasures are taken against unauthorized clients. |
|
15. Add the MAC address of a wireless device to the static countermeasures address list. |
countermeasure static mac-address |
By default, no countermeasures are taken on wireless devices. |
Configuring an alarm-ignored device list
For wireless devices in an alarm-ignored device list, WIPS only monitors them but does not generate any alarms for them.
To configure an alarm-ignored device list:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Add a MAC address to the alarm-ignored device list. |
ignorelist mac-address |
By default, no alarm-ignored device list exists. |
Configuring the aging time for a wireless device
This task configures an AP inactivity timer, a client inactivity timer, and an aging timer.
For a detected AP or an associated client, if WIPS detects that a wireless device does not transmit any packet when a timer is expired, it switches the state of the device from active to inactive. If the wireless device keeps in inactive state before the specified aging time expires, WIPS automatically removes the wireless device.
For an unassociated client, if WIPS detects that the client does not transmit any packet when a timer is expired, WIPS automatically removes the wireless device.
To configure the aging time for a wireless device:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Configure the AP inactivity timer for associated clients. |
timer ap-inactivity time |
By default, the AP inactivity timer for associated clients is 300 seconds. |
|
4. Configure the client inactivity timer. |
timer client-inactivity time |
By default, the client inactivity timer is 600 seconds. |
|
5. Configure the aging timer. |
timer device-aging time |
By default, the aging timer for a wireless device is 86400 seconds. |
Configuring the information update interval for wireless devices
If you do not configure the information update interval for wireless devices, a sensor notifies the AC to update the wireless device information only when it detects any information change such as working channel, authentication mode, and security method.
If you configure this interval, a sensor notifies the AC of the current state of the wireless devices at the specified interval when their information does not change so that the AC can get the wireless device status in time.
To configure the information update interval for wireless devices:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Configure the information update interval for wireless devices. |
timer device-update time |
By default, the information update interval is 20 seconds. |
Configuring the wireless packet statistics sending interval
Perform this task to configure the interval at which a sensor sends wireless packet statistics to the AC.
To configure the interval at which a sensor sends wireless packet statistics:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Configure the interval at which a sensor sends wireless packet statistics. |
timer statistic-period time |
By default, the wireless packet statistics sending interval is 900 seconds. |
Configuring the interval to re-classify wireless devices
WIPS periodically re-classifies detected APs and clients to adapt to attack detection policy changes. You can configure the interval for WIPS to re-classify these wireless devices. Configure an appropriate interval because a too long interval can cause incorrect classification of wireless devices and a too short interval can affect the device performance.
To configure the interval to re-classify wireless devices:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Configure the interval to re-classify wireless devices. |
timer reclassification time |
By default, the interval for WIPS to re-classify the detected APs and clients is 600 seconds. |
Configuring the aging time for WLAN mesh links
If a WLAN mesh link does not transmit any traffic within the aging time, WIPS deletes the mesh link.
To configure the aging time for WLAN mesh links:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Configure the aging time for WLAN mesh links. |
timer mesh-link-aging time-value |
By default, the aging time for WLAN mesh links is 600 seconds. |
Enabling automatic WIPS log saving
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Enable automatic WIPS log saving. |
wipslogfile enable |
By default, automatic WIPS log saving is disabled. |
Configuring the maximum size of WIPS logs
WIPS logs include system event logs and error packet logs. Perform this task to specify the maximum sizes for the two types of logs.
When the size of system event logs or error packet logs reaches the upper limit, WIPS removes the earliest logs.
To configure the maximum size of WIPS logs:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Configure the maximum size of system event logs. |
wipslogfile event size value |
By default, the size of system event logs depends on the device model. For more information, see About the H3C Access Controllers Command References. |
|
4. Configure the maximum size of error packet logs. |
wipslogfile malformed-packet size value |
By default, the size of error packet logs depends on the device model. For more information, see About the H3C Access Controllers Command References. |
Enabling anti-denial-of-service
Anti-denial-of-service (ADoS), the attack detection capability of WIPS, enables WIPS to detect attacks to the system, and reduces the impact by packet rate limitation and packet filtering.
To enable the anti-denial-of-service function:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Enable the anti-denial-of-service function. |
ados enable |
By default, the anti-denial-of-service function is disabled. |
Configuring the WIPS device type for an AP
You can only configure the WIPS device type for authorized APs, external APs, misconfigured APs, and rogue APs.
To configure the WIPS device type for an AP in WIPS view:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Configure the WIPS device type for an AP. |
manual-classify ap { authorized-ap | external-ap | misconfigured-ap | rogue-ap } mac-address &<1-2> |
By default, no WIPS device type is configured for an AP. |
To configure the WIPS device type for an AP in virtual security domain view:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Configure a virtual security domain. |
virtual-security-domain vsd-name |
N/A |
|
4. Configure the WIPS device type for an AP. |
manual-classify ap { authorized-ap | external-ap | misconfigured-ap | rogue-ap } mac-address &<1-2> |
By default, no WIPS device type is configured for an AP. |
Configuring client probing
Perform this task to configure an AP to collect client information and maintain client entries and send the collected client information to the specified server. The AC also generates logs based on the received client information. You can analyze the client data in the network based on the collected client information and logs.
To configure client probing:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Specify a server to receive the wireless device information. |
wireless-probe server ip ip-address port port-number [ interval interval ] preshared-key [ cipher | simple ] key-string |
Optional. By default, no server is specified. |
|
4. Configure APs to ignore the specified devices. |
wireless-probe ignore { ap | rssi rssi-value } |
Optional. By default, APs do not ignore wireless devices. |
|
5. Set the client entry aging timer. |
wireless-probe client-aging time-value |
Optional. By default, the client entry aging timer is 300 seconds. |
|
6. Disable wireless device detection for WIPS. |
detect wireless-device disable |
Optional. By default, wireless device detection for WIPS is enabled. |
|
7. Exit WIPS view. |
quit |
N/A |
|
8. Enter AP template view. |
wlan ap ap-name model model-name |
N/A |
|
9. Specify a server to receive the wireless device information. |
wireless-probe server ip ip-address port port-number [ interval interval ] preshared-key [ cipher | simple ] key-string |
Optional. By default, no server is specified. The configuration in AP template view takes precedence over the configuration in WIPS view. |
|
10. Enable client probing. |
wireless-probe enable |
By default, client probing is disabled. |
|
wireless-probe location longitude longitude-value latitude latitude-value |
Optional. By default, the longitude and latitude are not set for the AP. |
|
|
12. Configure the time difference between the AC and the AP. |
wireless-probe timezone { add | minus } timevalue |
Optional. By default, the time difference between the AC and the AP is not configured. |
Enabling random MAC address filtering
An Apple terminal might send probe requests by using a random MAC address. To prevent WIPS from triggering a false alarm for discovering unassociated or non-existent clients, enable this feature. Disable this feature when an Apple terminal works as a hotspot to avoid affecting hotspot detection, because Apple terminals use a random MAC address as the BSSID.
To enable random MAC address filtering:
|
Step |
Command |
Remarks |
|
system-view |
N/A |
|
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Enable random MAC address filtering. |
detect admin-mac-scan enable |
By default, random MAC address filtering is disabled. |
Configuring the channel scanning list
By default, an AP scans channels supported by its country code or all channels in turn. As a result, the interval at which a channel is scanned might be long and some important wireless network information might not be detected.
To resolve the problem, you can perform this task to configure the APs operating in monitor mode to detect the specified channels.
To configure the channel scanning list:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter WIPS view. |
wlan ips |
N/A |
|
3. Add one or multiple channels to the channel scanning list. |
detect scan-channel channel-list |
By default, the channel scanning list is not configured. |
Displaying and maintaining WLAN IPS
|
Task |
Command |
Remarks |
|
Display AP classification rule information. |
display wlan ips ap-classification-rule [ rule-name ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display attack detection policy information. |
display wlan ips attack-detect-policy [ policy-name ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display prohibited device list information. |
display wlan ips blocklist [ static | dynamic | mac-address mac-addr ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display channel information. |
display wlan ips channel [ permit | prohibit ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display malformed packet detection policy information. |
display wlan ips malformed-detect-policy [ policy-name ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display statistics about the specified or all entries in the countermeasures list of the specified or all virtual security domains. |
display wlan ips [ vsd vsd-name ] countermeasure-devices [ static [ countermeasure | pending | idle ] | dynamic [ countermeasure | pending ] | mac-address mac-addr ] [ verbose ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display information about the devices in the specified or all virtual security domains. |
display wlan ips [ vsd vsd-name ] devices [ ap [ adhoc | authorized | external | misconfigured | potential-authorized | potential-external | potential-rogue | rogue | uncategorized | mesh-ap ] | client [ authorized | misassociation | unauthorized | uncategorized | unassociated ] | mac-address mac-addr ] [ verbose ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display information about wireless services detected in the specified or all virtual security domains. |
display wlan ips [ vsd vsd-name ] network bss [ verbose ] [ name network-name | hotspot ] [ | { begin | exclude | include } regular-expression ] display wlan ips [ vsd vsd-name ] network [ mesh ] [ verbose ] [ name network-name ] [ | { begin | exclude | include } regular-expression ] ] |
Available in any view. |
|
Display the specified or all alarm events generated by WIPS. |
display wlan ips event [ source-mac source-mac | causer-mac causer-mac | id event-id | level event-level | type event-type | vsd vsd-name ] [ verbose ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display the hotspot list. |
display wlan ips hotspotlist [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display authorized SSID list information. |
display wlan ips authssidlist [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display the alarm-ignored device list. |
display wlan ips ignorelist [ mac-address mac-addr ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display information about the wireless services detected in the specified or all virtual security domains. |
display wlan ips [ vsd vsd-name ] network [ verbose ] [ ssid ssid-name ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display sensor information for the specified or all virtual security domains. |
display wlan ips sensor [ vsd vsd-name ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display packet statistics for a wireless device or channel. |
display wlan ips statistics { sensor sensor-name } { device [ mac-address mac-address ] | channel [ channel-num ] } { total | recent } [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display malformed packet statistics for a specific sensor. |
display wlan ips statistics sensor sensor-name malformed-counter |
Available in any view. |
|
Clear malformed packet statistics for a specific sensor. |
reset wlan ips statistics sensor [ sensor-name ] malformed-counter |
Available in any view. |
|
Display the WIPS status of the network or the specified virtual security domain. |
display wlan ips summary [ vsd vsd-name ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display permitted device list information. |
display wlan ips trustlist [ static | dynamic | mac-address mac-addr ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display policy information for the specified or all virtual security domains. |
display wlan ips vsd-policy [ vsd vsd-name ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Delete the specified or all alarm events generated by WIPS. |
reset wlan ips event { all | causer-mac causer-mac | id event-id | level event-level | source-mac source-mac | type event-type } |
Available in any view. |
|
Display signature information. |
display wlan ips signature { all | custom | signature-id id-value | signature-name name-string | standard } [ verbose ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display signature policy information. |
display wlan ips signature-policy { policy-name | all } [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display countermeasures policy information. |
display wlan ips countermeasure-policy [ policy-name ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display information about the specified OUI or all OUIs in the static trusted OUI list. |
display wlan ips static-trustoui [ oui-info | vendor ] |
Available in any view. |
|
Display all OUI information for the specified vendor in the OUI library of WIPS. |
display wlan ips oui vendor-name |
Available in any view. |
WLAN IPS configuration examples
WIPS policy application
Network requirements
In an internal wireless network using 802.11g, APs use permitted channels 1, 6, and 11. The network is divided into a lab area and an office area, each of which adopts its own WIPS policies. AP 1, AP 2, AP 3, and AP 4 use permitted channels as their working channels.
· In the lab area:
¡ Client 1 accesses the wireless network through AP 1.
¡ AP 5 spoofs the MAC address 000f-e203-332 of AP 1 to communicate with Client 1.
¡ AP 6 uses an invalid OUI 1111 to communicate with Client 1.
Deploy a monitor sensor Sensor 1 in the lab area, and enable MAC spoofing detection and invalid OUI detection.
· In the office area:
¡ Client 2 and Client 3 communicate over channel 3 through an Ad hoc connection.
¡ Coffee_AP is an external AP. Client 4 is in the static trusted device list, and accesses the wireless network with the SSID coffee_wlan through Coffee_AP.
Deploy a hybrid sensor Sensor 2 in the office area, and enable Ad hoc detection and prohibited channel detection.
Figure 5 Network diagram
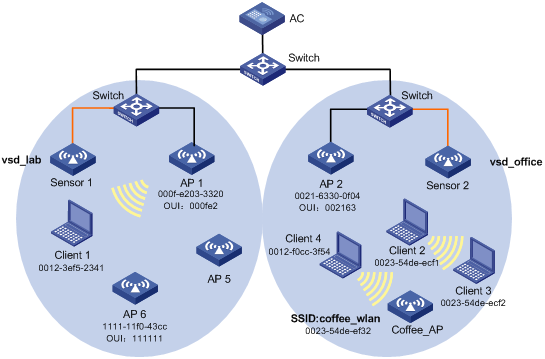
Configuration procedure
1. Configure permitted channel list and enable WIPS:
# Add channels 1, 6, and 11 to the permitted channel list.
<AC> system-view
[AC]wlan ips
[AC-wlan-ips]permit-channel 1 6 11
# Enable WIPS globally.
[AC-wlan-ips]wips enable
[AC-wlan-ips]quit
2. Configure WIPS policies for the lab area:
# Configure sensor 1 to operate in detect-only mode and use 802.11gn.
[AC] wlan ap sensor1 model WA2610E-AGN
[AC-wlan-ap-sensor1] serial-id 210235A29G007C000020
[AC-wlan-ap-sensor1]radio 2 type dot11gn
[AC-wlan-ap-sensor1-radio-2] wips detect mode detect-only
[AC-wlan-ap-sensor1-radio-2] radio enable
[AC-wlan-ap-sensor1-radio-2] quit
[AC-wlan-ap-sensor1] quit
# Configure attack detection policy lab to enable MAC spoofing detection and invalid OUI detection, and classify the invalid OUI device as a rogue device.
[AC] wlan ips
[AC-wlan-ips] attack-detect-policy lab
[AC-wlan-ips-dctp-lab] detect ap-spoofing
[AC-wlan-ips-dctp-lab] detect invalid-oui action classify rogue
[AC-wlan-ips-dctp-lab] quit
# Configure virtual security domain vsd_lab, apply attack detection policy lab to the domain, and add sensor 1 to the domain.
[AC-wlan-ips] virtual-security-domain vsd_lab
[AC-wlan-ips-vsd-vsd_lab] attack-detect-policy lab
[AC-wlan-ips-vsd-vsd_lab] sensor sensor1
[AC-wlan-ips-vsd-vsd_lab] quit
[AC-wlan-ips] quit
3. Configure WIPS policies for the office area:
# Create a WLAN-ESS interface, configure a clear-type service template service, and bind the WLAN-ESS interface to the service template.
[AC] interface wlan-ess 1
[AC-WLAN-ESS1] quit
[AC] wlan service-template 1 clear
[AC-wlan-st-1] ssid service
[AC-wlan-st-1] bind wlan-ess 1
[AC-wlan-st-1] authentication-method open-system
[AC-wlan-st-1] service-template enable
[AC-wlan-st-1] quit
# Configure sensor 2 to operate in hybrid mode, use 802.11gn, bind sensor 2 to the service template, and adopt the detect-first policy.
[AC] wlan ap sensor2 model WA2610E-AGN
[AC-wlan-ap-sensor2] serial-id 210235A29G007C000021
[AC-wlan-ap-sensor2] radio 2 type dot11gn
[AC-wlan-ap-sensor2-radio-2] wips detect mode detect-first
[AC-wlan-ap-sensor2-radio-2] service-template 1
[AC-wlan-ap-sensor2-radio-2] channel 1
[AC-wlan-ap-sensor2-radio-2] radio enable
[AC-wlan-ap-sensor2-radio-2] quit
[AC-wlan-ap-sensor2] quit
# Configure attack detection policy office to enable Ad hoc detection and prohibited channel detection.
[AC] wlan ips
[AC-wlan-ips] attack-detect-policy office
[AC-wlan-ips-dctp-office] detect adhoc-network
[AC-wlan-ips-dctp-office] detect prohibited-channel
[AC-wlan-ips-dctp-office] quit
# Configure AP classification rule ex_ap to classify Coffee_AP with the SSID coffee_wlan as an external AP.
[AC-wlan-ips] ap-classification-rule ex_ap
[AC-wlan-ips-class-ex_ap] classify-type external-ap
[AC-wlan-ips-class-ex_ap] sub-rule ssid equal coffee_wlan
[AC-wlan-ips-class-ex_ap] quit
# Configure countermeasures policy officecmp to take countermeasures against misassociated clients.
[AC-wlan-ips] countermeasure-policy officecmp
[AC-wlan-ips-cmep-officecmp] countermeasure misassociation-client
[AC-wlan-ips-cmep-officecmp] quit
# Configure virtual security domain vsd_office, apply attack detection policy office and countermeasures policy officecmp to the domain, apply the AP classification rule ex_ap, and add sensor 2 to the domain.
[AC-wlan-ips] virtual-security-domain vsd_office
[AC-wlan-ips-vsd-vsd_office] attack-detect-policy office
[AC-wlan-ips-vsd-vsd_office] countermeasure-policy officecmp
[AC-wlan-ips-vsd-vsd_office] ap-classification-rule ex_ap
[AC-wlan-ips-vsd-vsd_office] sensor sensor2
[AC-wlan-ips-vsd-vsd_office] quit
# Add the MAC address of Client 4 to the trusted device list.
[AC-wlan-ips]static-trustlist 0012-f0cc-3f54
Verifying the configuration
1. Execute the display wlan ips event type invalid-oui verbose command to display invalid OUI alarm information:
[AC] display wlan ips event type invalid-oui verbose
Total Number of Events: 1
WIPS Events
---------------------------------------------------------------------------------
ID: 289 Event Level: 2
Event Type : invalid-oui
Reported Time : 2013-08-06/17:53:45 - 2013-08-06/17:53:45
Aggregate times : 1
Causer : 1111-11f0-43cc
Source:
Source 1 : c4ca-d9f0-8ba0 VSD: -NA-
Detail Information:
In the VSD vsd_lab, detect AP invalid OUI 11-11-11, MAC 1111-11f0-43cc.
---------------------------------------------------------------------------------
The output shows that Sensor 1 detects AP 6 that uses invalid OUI 111111 in virtual security domain vsd_lab.
2. Execute the display wlan ips vsd vsd_lab devices verbose command to display information about the wireless devices in the virtual security domain vsd_lab.
[AC] display wlan ips vsd vsd_lab devices verbose
Detected Wireless Devices
--------------------------------------------------------------------------------
VSD: vsd_lab
BSSID : 1111-11F0-43CC
Vendor: -NA-
SSID : InvalidOUI_test
Hotspot : No
Status : Active
Classification : Rogue
Severity Level : 0
Security : Clear
Encrypt Method : -NA-
Authentication Method : None
Radio Type : 802.11gn
Channel : 6
In Countermeasure List : No
Up Time : 2013-07-30/11:33:08
First Reported Time : 2013-08-06/14:41:01
Last Reported Time : 2013-08-06/14:51:19
Reporting Sensor : 1
Sensor 1 : Sensor1
RadioId : 2
RSSI : 34
Last Reported Time : 2013-08-06/14:51:19
Attached Clients : 0
--------------------------------------------------------------------------------
The output shows that AP 6 with the MAC address 1111-11f0-43cc in the virtual security domain vsd_lab is detected to be using an invalid OUI, and AP 6 is classified as a rogue AP.
3. Execute the display wlan ips event type ap-mac-spoof verbose command to display MAC spoofing alarm information.
[AC] display wlan ips event type ap-mac-spoof verbose
Total Number of Events: 1
WIPS Events
---------------------------------------------------------------------------------
ID: 204 Event Level: 2
Event Type : ap-mac-spoof
Reported Time : 2013-08-06/16:08:49 - 2013-08-06/16:08:49
Aggregate times : 1
Causer : 000f-e203-3320
Source:
Source 1 : c4ca-d9f0-8ba0 VSD: vsd_lab
Detail Information:
In the VSD vsd_lab, detect AP spoofing, MAC 000f-e203-3320.
---------------------------------------------------------------------------------
The output shows that MAC spoofing is performed on AP 1 with the MAC address 000f-e203-3320 in the virtual security domain vsd_lab.
4. Execute the display wlan ips event type prohibited-chl verbose command to display prohibited channel alarm information.
[AC] display wlan ips event type prohibited-chl verbose
Total Number of Events: 1
WIPS Events
--------------------------------------------------------------------------------
ID: 429 Event Level: 2
Event Type : prohibited-chl
Reported Time : 2013-08-07/19:40:31 - 2013-08-07/19:40:31
Aggregate times : 1
Causer : -NA-
Source:
Source 1 : c4ca-d9f0-70cc VSD: vsd_office
Detail Information:
In the VSD vsd_office, inhibitory channel 3 is active.
--------------------------------------------------------------------------------
The output shows that an alarm is generated by the virtual security domain vsd_office, displaying that wireless communication exists on the prohibited channel 3.
5. Execute the display wlan ips event type adhoc-ap verbose command to display Ad hoc alarm information.
[AC] display wlan ips event type adhoc-ap verbose
Total Number of Events: 1
WIPS Events
---------------------------------------------------------------------------------
ID: 382 Event Level: 4
Event Type : adhoc-ap
Reported Time : 2013-08-07/18:55:10 - 2013-08-07/18:55:10
Aggregate times : 1
Causer : 0023-54de-ecf1
Source:
Source 1 : c4ca-d9f0-70cc VSD: vsd_office
Detail Information:
In the VSD vsd_office, AP 0023-54de-ecf1 is classified as Adhoc AP.
---------------------------------------------------------------------------------
The output shows that Client 2 in the virtual security domain vsd_office operates in ad hoc mode.
6. Execute the display wlan ips vsd vsd_office devices verbose command to display information about devices in the virtual security domain vsd_office.
[AC] display wlan ips vsd vsd_office devices verbose
Detected Wireless Devices
--------------------------------------------------------------------------------
VSD: vsd_office
Total Number of APs: 4
--------------------------------------------------------------------------------
BSSID : 0023-54de-ef32
Vendor: New H3C Technologies Co., Ltd.
SSID : coffee_wlan
Hotspot : No
Status : Active
Classification : External
Severity Level : 0
Security : Clear
Encrypt Method : -NA-
Authentication Method : None
Radio Type : 802.11gn
Channel : 1
In Countermeasure List : No
Up Time : 2013-08-01/16:42:04
First Reported Time : 2013-08-06/14:40:59
Last Reported Time : 2013-08-06/16:42:40
Reporting Sensor : 1
Sensor 1 : Sensor2
RadioId : 1
RSSI : 12
Last Reported Time : 2013-08-06/16:43:18
Attached Clients : 1
Client 1 : 0012-f0cc-3f54
--------------------------------------------------------------------------------
BSSID : 0023-54de-ecf1
Vendor: New H3C Technologies Co., Ltd.
SSID : h3c_adhoc
Hotspot : No
Status : Inactive
Classification : Adhoc
Severity Level : 0
Security : Clear
Encrypt Method : -NA-
Authentication Method : None
Radio Type : 802.11g
Channel : 10
In Countermeasure List : No
Up Time : 2013-08-06/16:38:18
First Reported Time : 2013-08-06/16:38:21
Last Reported Time : 2013-08-06/16:38:21
Reporting Sensor : 1
Sensor 1 : Sensor2
RadioId : 1
RSSI : 14
Last Reported Time : 2013-08-06/16:38:21
Attached Clients : 1
Client 1 : 0023-54de-ecf2
--------------------------------------------------------------------------------
Total Number of Clients: 2
--------------------------------------------------------------------------------
MAC Address: 0012-f0cc-3f54
Vendor: Intel Corporate
BSSID : 0023-54de-ef32
Status : Active
State : Association
Classification : misassociation
RadioType : 802.11gn
Channel : 1
In Countermeasure List : Yes
First Reported Time : 2013-08-06/17:10:07
Last Reported Time : 2013-08-06/17:10:51
Reporting Sensor : 1
Sensor 1 : Sensor2
RadioId : 1
RSSI : 50
Last Reported Time : 2013-08-06/17:10:51
--------------------------------------------------------------------------------
The output shows that in the virtual security domain vsd_office, Client 2 is classified as an ad hoc device, Coffee_AP with the MAC address 0023-54de-ef32 is classified as an external AP, and Client 4 is classified as a misassociated client because it is in the trusted device list and associated with an external AP, and it is being taken countermeasures.
7. Execute the display wlan ips vsd vsd_office countermeasure-devices verbose command to display countermeasures list information.
[AC] display wlan ips vsd vsd_office countermeasure-devices verbose
VSD = virtual security domain
Countermeasure Devices
---------------------------------------------------------------------------------
VSD: vsd_office
Device: 0012-f0cc-3f54
Type : Dynamic
Classification : misassociation-client
Precedence : 6
State : Countermeasure
Channel : 1
Sensor : Sensor2
Start-Time : 2013-08-06/18:59:42
Global Countermeasure : NO
Applied to Countermeasure-policies : officecmp
Countermeasure records :
2013-08-06/18:59:42 - 2013-08-06/18:59:42 Pending
---------------------------------------------------------------------------------
The output shows that in the virtual security domain vsd_office, Client 4 with the MAC address 0012-f0cc-3f54 is classified as a misassociated client, and it is dynamically added to the countermeasures list. The device that takes countermeasures against the client is Sensor 2.
Malformed packet detection configuration example
Network requirements
Configure Sensor 1 and Sensor 2 to operate in monitor mode and hybrid mode, respectively. Attacker 1 and Attacker 2 constantly send malformed packets to the sensors. Configure two virtual security domains VSD_1 and VSD_2, and assign Sensor 1 and Sensor 2 to VSD_1 and VSD_2, respectively.
Figure 6 Network diagram
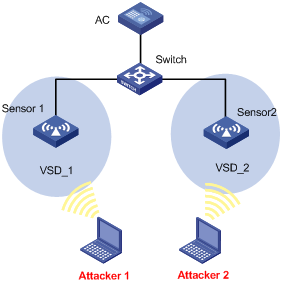
Configuration procedure
1. Configure wireless services. For more information, see "Configuring WLAN access."
2. Configure malformed packet detection:
# Enable WIPS.
<AC>system-view
[AC] wlan ips
[AC-wlan-ips]wips enable
[AC-wlan-ips]quit
# Create an AP named sensor 1 and configure it to operate in monitor mode.
[AC]wlan ap sensor1 model WA2620i-AGN
[AC-wlan-ap-sensor1] 210235A29G007C000020
[AC-wlan-ap-sensor1]radio 1
[AC-wlan-ap-sensor1-radio-1]wips detect mode detect-only
[AC-wlan-ap-sensor1-radio-1]radio enable
[AC-wlan-ap-sensor1-radio-1]quit
[AC-wlan-ap-sensor1]quit
# Create an AP named sensor 2 and configure it to operate in hybrid mode.
[AC] wlan ap sensor2 model WA3628i-AGN
[AC-wlan-ap-sensor2] serial-id 210235A29G007C000020
[AC-wlan-ap-sensor2] radio 2 type dot11gn
[AC-wlan-ap-sensor2-radio-2] service-template 1
[AC-wlan-ap-sensor2-radio-2] wips detect mode middle
[AC-wlan-ap-sensor2-radio-2] radio enable
[AC-wlan-ap-sensor2-radio-2] return
# Create malformed packet detection policies malf 1 and malf 2, and virtual security domains VSD_1 and VSD_2. Configure the sensor to send logs or alarms to the AC when malformed packets are detected.
<AC>system-view
[AC ]wlan ips
[AC-wlan-ips] malformed-detect-policy malf1
[AC-wlan-ips-mfdp-malf1] detect all action log
[AC-wlan-ips-mfdp-malf1] quiet-time 50
[AC-wlan-ips-mfdp-malf1] detect large-duration threshold 200 action log trap
[AC-wlan-ips-mfdp-malf1] quit
[AC-wlan-ips] virtual-security-domain VSD_1
[AC-wlan-ips-vsd-vsd_1] malformed-detect-policy malf1
[AC-wlan-ips-vsd-vsd_1] quit
[AC-wlan-ips] malformed-detect-policy malf2
[AC-wlan-ips-mfdp-malf2] detect all action log
[AC-wlan-ips-mfdp-malf2] quiet-time 50
[AC-wlan-ips-mfdp-malf2] detect large-duration threshold 200 action log trap
[AC-wlan-ips-mfdp-malf2]quit
[AC-wlan-ips] virtual-security-domain VSD_2
[AC-wlan-ips-vsd-vsd_2] malformed-detect-policy malf2
[AC-wlan-ips-vsd-vsd_2] quit
[AC-wlan-ips]quit
# Enable the information center.
[AC]info-center enable
Verifying the configuration
1. Enable sensor 1 and sensor 2 when there is no attacker on the network. The output from the display wlan ips event command on the AC shows that the AC does not receive any malformed packet detection alarms.
2. Execute the display wlan ips statistics sensor sensor-name malformed-counter command. The output shows that the number of malformed packets is 0.
[AC] display wlan ips statistics sensor sensor1 malformed-counter
Sensor name: sensor1
In the VSD: VSD_1
Malformation-Specify Count
------------------------------------------------------------------------
invalid-ie-length : 0
duplicated-ie : 0
redundant-ie : 0
invalid-pkt-length : 0
illegal-ibss-ess : 0
invalid-source-address : 0
overflow-eapol-key : 0
malformed-auth : 0
malformed-assoc-req : 0
malformed-ht-ie : 0
large-duration : 0
null-probe-resp : 0
invalid-deauth-code : 0
invalid-disassoc-code : 0
overflow-ssid : 0
fata-jack : 0
[AC] display wlan ips statistics sensor sensor2 malformed-counter
Sensor name: sensor2
In the VSD: VSD_2
Malformation-Specify Count
------------------------------------------------------------------------
invalid-ie-length : 0
duplicated-ie : 0
redundant-ie : 0
invalid-pkt-length : 0
illegal-ibss-ess : 0
invalid-source-address : 0
overflow-eapol-key : 0
malformed-auth : 0
malformed-assoc-req : 0
malformed-ht-ie : 0
large-duration : 0
null-probe-resp : 0
invalid-deauth-code : 0
invalid-disassoc-code : 0
overflow-ssid : 0
fata-jack : 0
------------------------------------------------------------------------
3. Enable only sensor 1. The output on the AC shows that the AC has received alarms for malformed packets with invalid-source-address, FATA-JACK, malformed-auth, illegal-ibss-ess, redundant-ie, malformed-ht-ie, duplicated-ie, invalid-pkt-length, and overflow-eapol-key.
4. Execute the display wlan ips statistics sensor sensor-name malformed-counter command to display malformed packet statistics.
[AC] display wlan ips statistics sensor sensor1 malformed-counter
Sensor name: sensor1
In the VSD: VSD_1
Malformation-Specify Count
------------------------------------------------------------------------
invalid-ie-length : 0
duplicated-ie : 566
redundant-ie : 1255
invalid-pkt-length : 488
illegal-ibss-ess : 154
invalid-source-address : 889
overflow-eapol-key : 463
malformed-auth : 445
malformed-assoc-req : 0
malformed-ht-ie : 789
large-duration : 0
null-probe-resp : 0
invalid-deauth-code : 0
invalid-disassoc-code : 0
overflow-ssid : 0
fata-jack : 878
------------------------------------------------------------------------
5. Execute the display wlan ips event type event-type command. The output shows that the AC has received nine types of events, including invalid-source-address, FATA-JACK, malformed-auth, illegal-ibss-ess, redundant-ie, malformed-ht-ie, duplicated-ie, invalid-pkt-length, and overflow-eapol-key.
[AC] display wlan ips event type redundant-ie verbose
Total Number of Events: 2
WIPS Events
---------------------------------------------------------------------------
ID: 437 Event Level: 5
Event Type : redundant-ie
Reported Time : 2013-05-25/23:55:31 - 2013-05-26/00:14:58
Aggregate times : 170
Causer : 1666-6699-3d44
Source:
Source 1 : 000f-e2a1-bf80 VSD: VSD_1
Detail Information:
In the VSD default, detect the device 1666-6699-3d44 launching a redundant
-ie malformed packet.
---------------------------------------------------------------------------
ID: 407 Event Level: 5
Event Type : redundant-ie
Reported Time : 2013-05-25/23:55:23 - 2013-05-26/00:14:58
Aggregate times : 424
Causer : 1666-6699-3cfc
Source:
Source 1 : 000f-e2a1-bf80 VSD: VSD_1
Detail Information:
In the VSD han, detect the device 1666-6699-3cfc launching a redundant-ie m
alformed packet.
---------------------------------------------------------------------------
You can view the log information for the malformed packets through the information center.
6. Enable only sensor 2. The output on the AC shows that the AC has received alarms for malformed packets at specified intervals.
7. Execute the display wlan ips statistics sensor sensor-name malformed-counter command to display malformed packet statistics.
[AC] display wlan ips statistics sensor sensor2 malformed-counter
Sensor name: sensor2
In the VSD: VSD_2
Malformation-Specify Count
------------------------------------------------------------------------
invalid-ie-length : 0
duplicated-ie : 100
redundant-ie : 162
invalid-pkt-length : 45
illegal-ibss-ess : 71
invalid-source-address : 254
overflow-eapol-key : 156
malformed-auth : 120
malformed-assoc-req : 0
malformed-ht-ie : 312
large-duration : 0
null-probe-resp : 0
invalid-deauth-code : 0
invalid-disassoc-code : 0
overflow-ssid : 0
fata-jack : 263
------------------------------------------------------------------------
8. Execute the display wlan ips event type event-type command. The output shows that the AC has received nine types of events, including invalid-source-address, FATA-JACK, malformed-auth, illegal-ibss-ess, redundant-ie, malformed-ht-ie, duplicated-ie, invalid-pkt-length, and overflow-eapol-key.
[AC] display wlan ips event type redundant-ie verbose
Total Number of Events: 2
WIPS Events
---------------------------------------------------------------------------
ID: 589 Event Level: 5
Event Type : redundant-ie
Reported Time : 2013-05-25/23:55:31 - 2013-05-26/00:14:58
Aggregate times : 170
Causer : 000e-ff00-0f04
Source:
Source 1 : 000f-e3a1-a050 VSD: VSD_2
Detail Information:
In the VSD default, detect the device 000e-ff00-0f04 launching a redundant
-ie malformed packet.
---------------------------------------------------------------------------
ID: 407 Event Level: 5
Event Type : redundant-ie
Reported Time : 2013-05-25/23:55:23 - 2013-05-26/00:14:58
Aggregate times : 424
Causer : 000e-ff00-0f04
Source:
Source 1 : 000f-e3a1-a050 VSD: VSD_2
Detail Information:
In the VSD han, detect the device 000e-ff00-0f04 launching a redundant-ie m
alformed packet.
---------------------------------------------------------------------------
You can view the log information for the malformed packets through the information center.
Signature configuration example
Network requirements
Client 1 with the MAC address 3ce5-a644-1c50 is associated with AP 2 and both are operating correctly. Client 2 with the MAC address 0012-f0cc-f77d spoofs AP 2 to continuously send deassociation uncast to Client 1, and Client 2 sends probe requests at high speed to the SSID coffee_wlan. Configure the sensor to operate in detect-only mode. Configure a user-defined signature on the AC to detect unicast diassociation flood. When WIPS detects that the number of probe responses with the SSID coffee_wlan exceeds 50 within 10 seconds, it sends signature alarms. A system-defined signature is available to detect deassociation floods and sends deassociation attack alarms.
Figure 7 Network diagram

Configuration procedure
# Enable WIPS.
<AC> system-view
[AC] wlan ips
[AC-wlan-ips] wips enable
[AC-wlan-ips] quit
# Create an AP named sensor and configure the sensor to operate in detect-only mode.
[AC] wlan ap sensor model WA2610E-AGN
[AC-wlan-ap-sensor] serial-id 210235A29G007C000022
[AC-wlan-ap-sensor] radio 1
[AC-wlan-ap-sensor-radio-1] wips detect mode detect-only
[AC-wlan-ap-sensor-radio-1] radio enable
[AC-wlan-ap-sensor-radio-1] quit
[AC-wlan-ap-sensor] quit
# Configure signature sig1 to detect attacks and collect statistics by MAC address. When WIPS detects that the number of probe responses with the SSID coffee_wlan exceeds 5 within 10 seconds, it sends signature alarms with the level 6.
[AC] wlan ips
[AC-wlan-ips] signature sig1
[AC-wlan-ips-sig-sig1] track-method per-mac
[AC-wlan-ips-sig-sig1] detect-period 10
[AC-wlan-ips-sig-sig1] detect-threshold per-mac 50
[AC-wlan-ips-sig-sig1] action report event-level 6
[AC-wlan-ips-sig-sig1] sub-rule frame-type management frame-subtype probe-request
[AC-wlan-ips-sig-sig1] sub-rule ssid equal coffee_wlan
[AC-wlan-ips-sig-sig1] match all
[AC-wlan-ips-sig-sig1] quit
# Configure signature policy floor.
[AC-wlan-ips] signature-policy floor
# Bind the system-defined signature disassoc_flood for detecting unicast diassociation flood and user-defined signature sig1 to the signature policy flood.
[AC-wlan-ips-sig-policy-floor] signature signature-name disassoc_flood
[AC-wlan-ips-sig-policy-floor] signature signature-name sig1
[AC-wlan-ips-sig-policy-floor] quit
# Configure virtual security domain vsd_1.
[AC-wlan-ips] virtual-security-domain vsd_1
# Apply signature policy floor in virtual security domain vsd_1 and add sensor to the virtual security domain.
[AC-wlan-ips-vsd-vsd_1] signature-policy floor
[AC-wlan-ips-vsd-vsd_1] sensor sensor
[AC-wlan-ips-vsd-vsd_1] quit
Verifying the configuration
1. Execute the display wlan ips event type flood-disassoc verbose command to display alarm information.
[AC] display wlan ips event type flood-disassoc verbose
Total Number of Events: 1
WIPS Events
---------------------------------------------------------------------------------
ID: 115 Event Level: 2
Event Type : flood-disassoc
Reported Time : 2013-08-07/16:06:17 - 2013-08-07/16:06:17
Aggregate times : 1
Causer : 3ce5-a644-1c50
Source:
Source 1 : c4ca-d9f0-8ba0 VSD: vsd_1
Detail Information:
In the VSD vsd_1, detect a disassociation-flood attack to the device 3ce5-a644-1c50. Related channel: 11
----------------------------------------------------------------------------------------
The output shows that an alarm has been generated in virtual security domain vsd_1 and the sensor has detected unicast diassociation flood attacks.
2. Execute the display wlan ips event type flood-custom command to display alarm information.
[AC] display wlan ips event type flood-custom verbose
Total Number of Events: 1
WIPS Events
----------------------------------------------------------------------------------------
ID: 68 Event Level: 6
Event Type : flood-custom
Reported Time : 2013-08-07/15:56:27 - 2013-08-07/15:56:35
Aggregate times : 2
Causer : 0012-f0cc-f77d
Source:
Source 1 : c4ca-d9f0-8ba0 VSD: vsd_1
Detail Information:
In the VSD vsd_1, detect the device 0012-f0cc-f77d launching a custom-flood-sig1 attack. Related channel: 11
---------------------------------------------------------------------------------
The output shows that an alarm is generated in virtual security domain vsd_1 and the sensor has detected that the number of probe requests sent by Client 2 to the AP with the SSID coffee_wlan exceeds 50 within 10 seconds.

