- Table of Contents
-
- 11-Security Configuration Guide
- 00-Preface
- 01-AAA Configuration
- 02-802.1X_Configuration
- 03-MAC Authentication Configuration
- 04-Portal Configuration
- 05-Password Control Configuration
- 06-Public Key Configuration
- 07-IPsec Configuration
- 08-SSH Configuration
- 09-Blacklist Configuration
- 10-TCP and ICMP Attack Protection Configuration
- 11-IP Source Guard Configuration
- 12-ARP Attack Protection Configuration
- 13-ND Attack Defense Configuration
- 14-URPF Configuration
- 15-PKI Configuration
- 16-SSL Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 16-SSL Configuration | 141.59 KB |
Contents
Configuring an SSL server policy
SSL server policy configuration example
Configuring an SSL client policy
SSL overview
Secure Sockets Layer (SSL) is a security protocol that provides secure connection services for TCP-based application layer protocols such as HTTP. It is widely used in e-business and online bank fields to ensure secure data transmission over the Internet.
SSL security mechanism
Secure connections provided by SSL have these features:
· Confidentiality—SSL uses a symmetric encryption algorithm to encrypt data and uses the asymmetric key algorithm of Rivest, Shamir, and Adelman (RSA) to encrypt the key to be used by the symmetric encryption algorithm.
· Authentication—SSL supports certificate-based identity authentication of the server and client by using the digital signatures. The SSL server and client obtain certificates from a certificate authority (CA) through the Public Key Infrastructure (PKI).
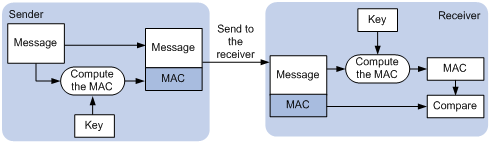
· Reliability—SSL uses the key-based message authentication code (MAC) to verify message integrity. A MAC algorithm transforms a message of any length to a fixed-length message. Figure 1 illustrates how SSL uses a MAC algorithm to verify message integrity. With the key, the sender uses the MAC algorithm to compute the MAC value of a message. Then, the sender suffixes the MAC value to the message and sends the result to the receiver. The receiver uses the same key and MAC algorithm to compute the MAC value of the received message, and compares the locally computed MAC value with that received. If the two match, the receiver considers the message intact; otherwise, the receiver considers that the message has been tampered with in transit and discards the message.
Figure 1 Message integrity verification by a MAC algorithm
|
|
NOTE: · For more information about symmetric key algorithms, asymmetric key algorithm RSA and digital signature, see the chapter “Configuring public key.” · For more information about PKI, certificate, and CA, see the chapter “Configuring PKI.” |
SSL protocol stack
As shown in Figure 2, the SSL protocol consists of two layers of protocols: the SSL record protocol at the lower layer and the SSL handshake protocol, change cipher spec protocol, and alert protocol at the upper layer.

· SSL record protocol—Fragments data to be transmitted, computes and adds MAC to the data, and encrypts the data before transmitting it to the peer end.
· SSL handshake protocol—Negotiates the cipher suite to be used for secure communication (including the symmetric encryption algorithm, key exchange algorithm, and MAC algorithm), securely exchanges the key between the server and client, and implements identity authentication of the server and client. Through the SSL handshake protocol, a session is established between a client and the server. A session consists of a set of parameters, including the session ID, peer certificate, cipher suite, and master secret.
· SSL change cipher spec protocol—Used for notification between the client and the server that the subsequent packets are to be protected and transmitted based on the newly negotiated cipher suite and key.
· SSL alert protocol—Enables the SSL client and server to send alert messages to each other. An alert message contains the alert severity level and a description.
SSL configuration task list
Complete the following tasks to configure SSL:
|
Task |
Remarks |
|
Required |
|
|
Optional |
Configuring an SSL server policy
An SSL server policy is a set of SSL parameters for a server to use when booting up. An SSL server policy takes effect only after it is associated with an application layer protocol such as HTTP.
Configuration prerequisites
Configure the PKI domain for the SSL server policy to use to obtain a certificate for the SSL server. For more information about PKI domain configuration, see the chapter “Configuring PKI.”
Configuration procedure
To configure an SSL server policy:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an SSL server policy and enter its view. |
ssl server-policy policy-name |
N/A |
|
3. Specify a PKI domain for the SSL server policy. |
pki-domain domain-name |
By default, no PKI domain is specified for an SSL server policy. |
|
4. Specify the cipher suite(s) for the SSL server policy to support. |
ciphersuite [ rsa_3des_ede_cbc_sha | rsa_aes_128_cbc_sha | rsa_aes_256_cbc_sha | rsa_des_cbc_sha | rsa_rc4_128_md5 | rsa_rc4_128_sha ] * |
Optional. By default, an SSL server policy supports all cipher suites. |
|
5. Set the handshake timeout time for the SSL server. |
handshake timeout time |
Optional. 3,600 seconds by default |
|
6. Set the SSL connection close mode. |
close-mode wait |
Optional. Not wait by default |
|
7. Set the maximum number of cached sessions and the caching timeout time. |
session { cachesize size | timeout time } * |
Optional. The defaults are as follows: · 500 for the maximum number of cached sessions, · 3600 seconds for the caching timeout time. |
|
8. Configure the server to require certificate-based SSL client authentication. |
client-verify enable |
Optional. By default, the SSL server does not require the client to be authenticated. |
|
9. Enable SSL client weak authentication. |
client-verify weaken |
Optional. Disabled by default. This command takes effect only when the client-verify enable command is configured. |
|
|
NOTE: · If you enable client authentication here, you must request a local certificate for the client. · SSL mainly comes in these versions: SSL 2.0, SSL 3.0, and TLS 1.0, where TLS 1.0 corresponds to SSL 3.1. When the switch acts as an SSL server, it can communicate with clients running SSL 3.0 or TLS 1.0, and can identify Hello packets from clients running SSL 2.0. If a client running SSL 2.0 also supports SSL 3.0 or TLS 1.0 (information about supported versions is carried in the packet that the client sends to the server), the server will notify the client to use SSL 3.0 or TLS 1.0 to communicate with the server. |
SSL server policy configuration example
Network requirements
As shown in Figure 3, users can need to access and control the device through web pages.
For security of the device and to protect data from being eavesdropped or tampered with, perform the following configuration tasks so that the users must use HTTPS (HTTP Secure, which uses SSL) to log in to the web interface of the device and use SSL for identity authentication:
· Configure Switch to work as the HTTPS server and request a certificate for Switch.
· Request a certificate for Host so that Switch can authenticate the identity of Host.
· Configure a CA server to issue certificates to Switch and Host.
|
|
NOTE: · This example assumes that the CA server runs Windows Server and has the Simple Certificate Enrollment Protocol (SCEP) plug-in installed. · Before performing the following configurations, make sure that the switch, the host, and the CA server can reach each other. |
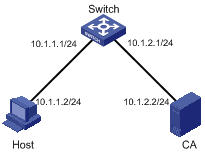
Configuration procedure
1. Configure the HTTPS server (Switch)
# Create a PKI entity named en, and configure the common name as http-server1 and the FQDN as ssl.security.com.
< Switch> system-view
[Switch] pki entity en
[Switch-pki-entity-en] common-name http-server1
[Switch-pki-entity-en] fqdn ssl.security.com
[Switch-pki-entity-en] quit
# Create PKI domain 1, specify the trusted CA as ca server, the URL of the registration server as http://10.1.2.2/certsrv/mscep/mscep.dll, the authority for certificate request as RA, and the entity for certificate request as en.
[Switch] pki domain 1
[Switch-pki-domain-1] ca identifier ca server
[Switch-pki-domain-1] certificate request url http://10.1.2.2/certsrv/mscep/mscep.dll
[Switch-pki-domain-1] certificate request from ra
[Switch-pki-domain-1] certificate request entity en
[Switch-pki-domain-1] quit
# Create the local RSA key pairs.
[Switch] public-key local create rsa
# Retrieve the CA certificate.
[Switch] pki retrieval-certificate ca domain 1
# Request a local certificate for Switch.
[Switch] pki request-certificate domain 1
# Create an SSL server policy named myssl.
[Switch] ssl server-policy myssl
# Specify the PKI domain for the SSL server policy as 1.
[Switch-ssl-server-policy-myssl] pki-domain 1
# Enable client authentication.
[Switch-ssl-server-policy-myssl] client-verify enable
[Switch-ssl-server-policy-myssl] quit
# Configure HTTPS service to use SSL server policy myssl.
[Switch] ip https ssl-server-policy myssl
# Enable HTTPS service.
[Switch] ip https enable
# Create a local user named usera, and set the password to 123 and service type to web.
[Switch] local-user usera
[Switch-luser-usera] password simple 123
[Switch-luser-usera] service-type web
2. Configure the HTTPS client (Host)
On Host, launch IE, enter http://10.1.2.2/certsrv in the address bar and request a certificate for Host as prompted.
3. Verify the configuration
Launch IE on the host, enter https://10.1.1.1 in the address bar, and select the certificate issued by the CA server. The web interface of the switch should appear. After entering username usera and password 123, you should be able to log in to the web interface to access and manage the switch.
|
|
NOTE: · For more information about PKI configuration commands and the public-key local create rsa command, see Security Command Reference. · For more information about HTTPS, see Fundamentals Configuration Guide. |
Configuring an SSL client policy
An SSL client policy is a set of SSL parameters for a client to use when connecting to the server. An SSL client policy takes effect only after it is associated with an application layer protocol.
Configuration prerequisites
If the SSL server is configured to authenticate the SSL client, you must configure the PKI domain for the SSL client policy to use to obtain the certificate of the client. For more information about PKI domain configuration, see the chapter “Configuring PKI.”
Configuration procedure
To configure an SSL client policy:
|
Command |
Remarks |
|
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an SSL client policy and enter its view. |
ssl client-policy policy-name |
N/A |
|
3. Specify a PKI domain for the SSL client policy. |
pki-domain domain-name |
Optional. No PKI domain is configured by default. |
|
4. Specify the preferred cipher suite for the SSL client policy. |
prefer-cipher { rsa_3des_ede_cbc_sha | rsa_aes_128_cbc_sha | rsa_aes_256_cbc_sha | rsa_des_cbc_sha | rsa_rc4_128_md5 | rsa_rc4_128_sha } |
Optional. rsa_rc4_128_md5 by default |
|
5. Specify the SSL protocol version for the SSL client policy. |
version { ssl3.0 | tls1.0 } |
Optional. TLS 1.0 by default. |
|
6. Enable certificate-based SSL server authentication. |
server-verify enable |
Optional. Enabled by default. |
|
|
NOTE: If you enable client authentication on the server, you must request a local certificate for the client. |
Displaying and maintaining SSL
|
Task |
Command |
Remarks |
|
Display SSL server policy information. |
display ssl server-policy { policy-name | all } [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display SSL client policy information. |
display ssl client-policy { policy-name | all } [ | { begin | exclude | include } regular-expression ] |
Available in any view |
Troubleshooting SSL
SSL handshake failure
Symptom
As the SSL server, the device fails to handshake with the SSL client.
Analysis
SSL handshake failure may result from the following causes:
· The SSL client is configured to authenticate the SSL server, but the SSL server has no certificate or the certificate is not trusted.
· The SSL server is configured to authenticate the SSL client, but the SSL client has no certificate or the certificate is not trusted.
· The server and the client have no matching cipher suite.
Solution
1. Issue the debugging ssl command and view the debugging information to locate the problem:
? If the SSL client is configured to authenticate the SSL server but the SSL server has no certificate, request one for it.
? If the server’s certificate cannot be trusted, install the root certificate of the CA that issues the local certificate to the SSL server on the SSL client, or let the server request a certificate from the CA that the SSL client trusts.
? If the SSL server is configured to authenticate the client, but the SSL client has no certificate or the certificate cannot be trusted, request and install a certificate for the client.
2. Use the display ssl server-policy command to view the cipher suites that the SSL server policy supports. If the server and the client have no matching cipher suite, use the ciphersuite command to modify the cipher suite configuration of the SSL server.

