- Table of Contents
-
- 03-Security Configuration Guide
- 00-Preface
- 01-Security zone configuration
- 02-Security policy configuration
- 03-ASPF configuration
- 04-Session management
- 05-Object group configuration
- 06-Object policy configuration
- 07-IP source guard configuration
- 08-AAA configuration
- 09-User identification configuration
- 10-Password control configuration
- 11-Portal configuration
- 12-MAC authentication configuration
- 13-IPoE configuration
- 14-Public key management
- 15-PKI configuration
- 16-SSH configuration
- 17-SSL configuration
- 18-Connection limit configuration
- 19-Attack detection and prevention configuration
- 20-Server connection detection configuration
- 21-ARP attack protection configuration
- 22-ND attack defense configuration
- 23-uRPF configuration
- 24-IP-MAC binding configuration
- 25-IP reputation configuration
- 26-APR configuration
- 27-Keychain configuration
- 28-Crypto engine configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 07-IP source guard configuration | 119.81 KB |
Contents
Restrictions and guidelines: IPSG configuration
Configuring the IPv4SG feature
Enabling IPv4SG on an interface
Configuring a static IPv4SG binding
Configuring the IPv6SG feature
Enabling IPv6SG on an interface
Configuring a static IPv6SG binding
Display and maintenance commands for IPSG
Configuring IP source guard
About IPSG
IP source guard (IPSG) prevents spoofing attacks by using an IPSG binding table to filter out illegitimate packets. This feature is typically configured on user-side interfaces.
IPSG operating mechanism
The IPSG binding table contains bindings that bind IP address, MAC address, VLAN, or any combinations. IPSG uses the bindings to match an incoming packet. If a match is found, the packet is forwarded. If no match is found, the packet is discarded.
IPSG is a per-interface packet filter. Configuring this feature on one interface does not affect packet forwarding on another interface.
IPSG bindings can be static or dynamic.
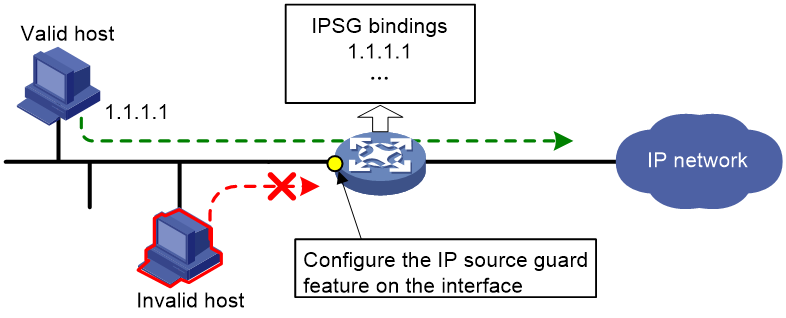
As shown in Figure 1, IPSG forwards only the packets that match an IPSG binding.
Figure 1 IPSG application
Static IPSG bindings
Static IPSG bindings are configured manually. They are suitable for scenarios where few hosts exist on a LAN and their IP addresses are manually configured. For example, you can configure a static IPSG binding on an interface that connects to a server. This binding allows the interface to receive packets only from the server.
Static IPSG bindings on an interface implement the following functions:
· Filter incoming IPv4 or IPv6 packets on the interface.
· Cooperate with ARP attack detection in IPv4 for user validity checking. For information about ARP attack detection, see "Configuring ARP attack protection."
Static IPSG bindings can be global or interface-specific.
· Global static binding—Binds the IP address and MAC address in system view. The binding takes effect on all interfaces to filter packets for user spoofing attack prevention.
· Interface-specific static binding—Binds the IP address, MAC address, VLAN, or any combination of the items in interface view. The binding takes effect only on the interface to check the validity of users who are attempting to access the interface.
Dynamic IPSG bindings
IPSG automatically obtains user information from other modules to generate dynamic bindings. A dynamic IPSG binding can contain MAC address, IPv4 or IPv6 address, VLAN tag, ingress interface, and binding type. The binding type identifies the source module for the binding, such as DHCP relay agent or DHCPv6 relay agent.
For example, DHCP-based IPSG bindings are suitable for scenarios where hosts on a LAN obtain IP addresses through DHCP. When a host obtains an IP address through DHCP, each of the following modules generates an entry:
· The DHCP server generates a DHCP binding.
· The DHCP relay agent generates a DHCP relay entry.
IPSG generates a dynamic IPSG binding based on each of the above entries. IPSG allows only packets from the DHCP clients to pass through.
Dynamic IPv4SG
Dynamic bindings generated based on different source modules are for different usages:
|
Interface types |
Source modules |
Binding usage |
|
Layer 2 Ethernet interface |
ARP snooping |
For cooperation with modules (such as the ARP attack detection module) to provide security services. |
|
Layer 3 Ethernet interface Layer 3 aggregate interface VLAN interface Reth interface Reth subinterface |
DHCP relay agent |
Packet filtering. |
|
DHCP server |
For cooperation with modules (such as the authorized ARP module) to provide security services. |
For information about ARP snooping DHCP relay, and DHCP server, see Layer 3—IP Services Configuration Guide.
Dynamic IPv6SG
Dynamic IPv6SG bindings generated based on different source modules are for different usages:
|
Interface types |
Source modules |
Binding usage |
|
Layer 3 Ethernet interface Layer 3 aggregate interface VLAN interface Reth interface Reth subinterface |
DHCPv6 relay agent |
Packet filtering. |
For more information about DHCPv6 relay agent, see Layer 3—IP Services Configuration Guide.
Restrictions and guidelines: IPSG configuration
You cannot configure the IPSG feature on a service loopback interface. If IPSG is enabled on an interface, you cannot assign the interface to a service loopback group.
IPSG tasks at a glance
To configure IPv4SG, perform the following tasks:
1. Enabling IPv4SG on an interface
2. (Optional.) Configuring a static IPv4SG binding
To configure IPv6SG, perform the following tasks:
1. Enabling IPv6SG on an interface
2. (Optional.) Configuring a static IPv6SG binding
Configuring the IPv4SG feature
Enabling IPv4SG on an interface
About this task
When you enable IPSG on an interface, the static and dynamic IPSG are both enabled.
· Static IPv4SG uses static bindings configured by using the ip source binding command. For more information, see "Configuring a static IPv4SG binding."
· Dynamic IPv4SG generates dynamic bindings from related source modules. IPv4SG uses the bindings to filter incoming IPv4 packets based on the matching criteria specified in the ip verify source command.
Restrictions and guidelines
To implement dynamic IPv4SG, make sure ARP snooping, DHCP relay agent, or DHCP server operates correctly on the network.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
The following interface types are supported:
¡ Layer 2 Ethernet interface.
¡ Layer 3 Ethernet interface.
¡ Layer 3 Ethernet subinterface.
¡ Layer 3 aggregate interface.
¡ Layer 3 aggregate subinterface.
¡ VLAN interface.
¡ Reth interface.
¡ Reth subinterface.
3. Enable the IPv4SG feature.
ip verify source { ip-address | ip-address mac-address | mac-address }
By default, the IPv4SG feature is disabled on an interface.
Configuring a static IPv4SG binding
About this task
You can configure global static and interface-specific static IPv4SG bindings. Interface-specific static and dynamic bindings take priority over global static bindings. An interface first uses the static and dynamic bindings on the interface to match packets. If no match is found, the interface uses the global bindings.
Restrictions and guidelines
Global static bindings take effect on all interfaces on the device.
To configure a static IPv4SG binding for the ARP attack detection feature, make sure the following conditions are met:
· The ip-address ip-address option, the mac-address mac-address option, and the vlan vlan-id option must be specified.
· ARP attack detection must be enabled for the specified VLAN.
Configuring a global static IPv4SG binding
1. Enter system view.
system-view
2. Configure a global static IPv4SG binding.
ip source binding ip-address ip-address mac-address mac-address
Configuring a static IPv4SG binding on an interface
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
The following interface types are supported:
¡ Layer 2 Ethernet interface.
¡ Layer 3 Ethernet interface.
¡ Layer 3 Ethernet subinterface.
¡ Layer 3 aggregate interface.
¡ Layer 3 aggregate subinterface.
¡ VLAN interface.
¡ Reth interface.
¡ Reth subinterface.
3. Configure a static IPv4SG binding.
ip source binding { ip-address ip-address | ip-address ip-address mac-address mac-address | mac-address mac-address }
You can configure the same static IPv4SG binding on different interfaces.
Configuring the IPv6SG feature
Enabling IPv6SG on an interface
About this task
When you enable IPv6SG on an interface, the static and dynamic IPv6SG are both enabled.
· Static IPv6SG uses static bindings configured by using the ipv6 source binding command. For more information, see "Configuring a static IPv6SG binding."
· Dynamic IPv6SG generates dynamic bindings from related source modules. IPv6SG uses the bindings to filter incoming IPv6 packets based on the matching criteria specified in the ipv6 verify source command.
Restrictions and guidelines
To implement dynamic IPv6SG, make sure DHCPv6 relay agent operates correctly on the network.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
The following interface types are supported:
¡ Layer 2 Ethernet interface.
¡ Layer 3 Ethernet interface.
¡ Layer 3 Ethernet subinterface.
¡ Layer 3 aggregate interface.
¡ Layer 3 aggregate subinterface.
¡ VLAN interface.
¡ Reth interface.
¡ Reth subinterface.
3. Enable the IPv6SG feature.
ipv6 verify source { ip-address | ip-address mac-address | mac-address }
By default, the IPv6SG feature is disabled on an interface.
Configuring a static IPv6SG binding
About this task
You can configure global static and interface-specific static IPv6SG bindings. Interface-specific static and dynamic bindings take priority over global static bindings. An interface first uses the static and dynamic bindings on the interface to match packets. If no match is found, the interface uses the global bindings.
Restrictions and guidelines
Global static bindings take effect on all interfaces on the device.
Configuring a global static IPv6SG binding
1. Enter system view.
system-view
2. Configure a global static IPv6SG binding.
ipv6 source binding ip-address ipv6-address mac-address mac-address
Configuring a static IPv6SG binding on an interface
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
The following interface types are supported:
¡ Layer 2 Ethernet interface.
¡ Layer 3 Ethernet interface.
¡ Layer 3 Ethernet subinterface.
¡ Layer 3 aggregate interface.
¡ Layer 3 aggregate subinterface.
¡ VLAN interface.
¡ Reth interface.
¡ Reth subinterface.
3. Configure a static IPv6SG binding.
ipv6 source binding { ip-address ipv6-address | ip-address ipv6-address mac-address mac-address | mac-address mac-address }
You can configure the same static IPv6SG binding on different interfaces.
Display and maintenance commands for IPSG
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display IPv4SG bindings. |
display ip source binding [ static | [ vpn-instance vpn-instance-name ] [ dhcp-relay | dhcp-server ip-mac-vlan | ip-mac-vpn ] ] [ ip-address ip-address ] [ mac-address mac-address ] [ vlan vlan-id ] [ interface interface-type interface-number ] [ chassis chassis-number slot slot-number ] |
|
Display IPv6SG bindings. |
display ipv6 source binding [ static | [ vpn-instance vpn-instance-name ] [ ipv6-mac-vlan | ipv6-mac-vpn ] ] [ ip-address ipv6-address ] [ mac-address mac-address ] [ vlan vlan-id ] [ interface interface-type interface-number ] [ chassis chassis-number slot slot-number ] |