- Table of Contents
-
- 07-Security Configuration Guide
- 00-Preface
- 01-Security Overview
- 02-AAA Configuration
- 03-802.1X Configuration
- 04-MAC Authentication Configuration
- 05-Portal Configuration
- 06-Port Security Configuration
- 07-User Profile Configuration
- 08-Password Control Configuration
- 09-Public Key Configuration
- 10-PKI Configuration
- 11-SSH Configuration
- 12-SSL Configuration
- 13-SSL VPN Configuration
- 14-TCP Attack Protection Configuration
- 15-ARP Attack Protection Configuration
- 16-IPsec Configuration
- 17-ALG Configuration
- 18-Firewall Configuration
- 19-Session Management Configuration
- 20-Web Filtering Configuration
- 21-User Isolation Configuration
- 22-Source IP Address Verification Configuration
- 23-FIPS Configuration
- 24-Protocol Packet Rate Limit Configuration
- 25-Attack detection and protection configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 09-Public Key Configuration | 107.68 KB |
Creating a local asymmetric key pair
Distributing a local host public key
Destroying a local asymmetric key pair
Configuring a peer host public key
Importing a peer host public key from a public key file
Entering a peer host public key
Public key configuration examples
Manually specifying the peer host public key on the local device
Importing a public key from a public key file
Managing public keys
To protect data confidentiality during transmission, the data sender uses an algorithm and a key to encrypt the plain text data before sending the data out. The receiver uses the same algorithm with the help of a key to decrypt the data, as shown in Figure 1.
Figure 1 Encryption and decryption
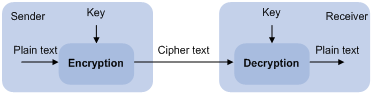
The keys that participate in the conversion between plain text and cipher text can be the same or different, dividing the encryption and decryption algorithms into the following types:
· Symmetric key algorithm—The keys for encryption and decryption are the same.
· Asymmetric key algorithm—The keys for encryption and decryption are different. One is the public key, and the other is the private key. The information encrypted with the public key can only be decrypted with the corresponding private key, and vice versa. The private key is kept secret, and the public key may be distributed widely. The private key cannot be practically derived from the public key. The device supports RSA and DSA asymmetric key algorithms.
The asymmetric key algorithms can be used for the following purposes:
· To encrypt and decrypt data—Any public key receiver can use the public key to encrypt information, but only the private key owner can decrypt the information. This mechanism ensures confidentiality.
· To authenticate a sender—Also called "digital signature." The key owner uses the private key to "sign" information to be sent, and the receiver decrypts the information with the sender's public key to verify information authenticity.
Asymmetric key algorithms are widely used in various applications. For example, SSH, SSL, and PKI use the algorithms for digital signature. For information about SSH, SSL, and PKI, see "Configuring SSH," "Configuring SSL," and "Configuring PKI."
Configuration task list
Public key configuration tasks enable you to manage the local asymmetric key pairs and configure the peer host public keys on the local device. By completing these tasks, the local device is ready to work with applications such as SSH and SSL to implement data encryption/decryption, or digital signature.
Complete these tasks to configure public keys:
|
Task |
Remarks |
|
|
Configuring a local asymmetric key pair on the local device |
Choose one or more tasks. |
|
Creating a local asymmetric key pair
When you create a local key pair, follow these guidelines:
· The key algorithm must be the same as required by the security application.
· Enter an appropriate key modulus length at prompt (see Table 1).
· The created key pairs are automatically saved and can survive system reboots.
Table 1 A comparison of different types of asymmetric key algorithms
|
Type |
Number of key pairs |
Modulus length |
|
RSA |
One server key pair and one host key pair. NOTE: Only SSH 1.5 uses the RSA server key pair. |
· In non-FIPS mode: 512 to 2048 bits and defaults to 1024 bits. · In FIPS mode: 2048 bits. |
|
DSA |
One host key pair. |
· In non-FIPS mode: 512 to 2048 bits and defaults to 1024 bits. · In FIPS mode: 2048 bits. |
To create a local asymmetric key pair:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a local asymmetric key pair. |
public-key local create { dsa | rsa } |
By default, no asymmetric key pairs exist. If the type of key pair to be created already exists, the system asks you whether you want to overwrite the existing key pair. |
Distributing a local host public key
You must distribute a local host public key to a peer device so the peer device can perform the following operations:
· Use the public key to encrypt information sent to the local device.
· Authenticate the digital signature signed by the local device.
To distribute a local host public key, you must first export or display the key.
· Export a host public key:
¡ Export a host public to a file.
¡ Export a host public key to the monitor screen, and then save it to a file.
After the key is exported to a file, transfer the file to the peer device. On the peer device, import the key from the file.
· Display a host public key.
After the key is displayed, record the key, for example, copy it to an unformatted file. On the peer device, you must literally enter the key.
Displaying a host public key
|
Task |
Command |
Remarks |
|
Display the local RSA public keys. |
display public-key local rsa public [ | { begin | exclude | include } regular-expression ] |
Available in any view. Use at least one command. |
|
Display the local DSA public keys. |
display public-key local dsa public [ | { begin | exclude | include } regular-expression ] |
|
|
NOTE: Do not distribute the RSA server public key serverkey (default) to a peer device. |
Exporting a host public key
When you export a host public key, follow these restrictions and guidelines:
· If you specify a file name in the command, the command exports the key to the specified file.
· If you do not specify a file name, the command exports the key to the monitor screen. You must manually save the exported key to a file.
To export a local host public key:
|
Step |
Command |
|
1. Enter system view. |
system-view |
|
2. Export a local host public key. |
· Export an RSA host public key: ¡ In non-FIPS mode: ¡ In FIPS mode: · Export a DSA host public key: |
Destroying a local asymmetric key pair
To avoid key compromise, destroy the local key pair and generate a new pair after any of the following conditions occurs:
· An intrusion event has occurred.
· The storage media of the device is replaced.
· The local certificate has expired.
For more information about local certificates, see "Configuring PKI."
To destroy a local asymmetric key pair:
|
Step |
Command |
|
1. Enter system view. |
system-view |
|
2. Destroy a local asymmetric key pair. |
public-key local destroy { dsa| rsa } |
Configuring a peer host public key
To encrypt information sent to a peer device or authenticate the digital signature of the peer device, you must configure the peer device's public key on the local device.
You can configure the peer host public key by using the following methods:
· Import the peer host public key form a public key file (recommended).
· Manually enter (type or copy) the peer host public key.
Importing a peer host public key from a public key file
Before you perform this task, make sure you have exported the host public key to a file on the peer device and obtained the file from the peer device. For information about exporting a host public key, see "Exporting a host public key."
After you import the key, the system automatically converts the imported public key to a string in the Public Key Cryptography Standards (PKCS) format.
To import a peer host public key from a public key file:
|
Step |
Command |
|
1. Enter system view. |
system-view |
|
2. Import the host public key from the public key file. |
public-key peer keyname import sshkey filename |
Entering a peer host public key
Before you perform this task, make sure you have displayed the key on the peer device and recorded the key. For information about displaying a host public key, see "Displaying a host public key."
Use the display public-key local public command to display the public key on the peer device. The format of the public key displayed in any other way might be incorrect. If the key is not in the correct format, the system discards the key and displays an error message. If the key is valid, the system saves the key.
Always import rather than enter the peer host public key if you are not sure that the device supports the format of the recorded peer host public key.
To enter a peer host public key:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Specify a name for the public key and enter public key view. |
public-key peer keyname |
N/A |
|
3. Enter public key code view. |
public-key-code begin |
N/A |
|
4. Configure the peer host public key. |
Type or copy the key |
Spaces and carriage returns are allowed between characters. |
|
5. Return to public key view. |
public-key-code end |
When you exit public key code view, the system automatically saves the public key. |
|
6. Return to system view. |
peer-public-key end |
N/A |
Displaying public keys
|
Task |
Command |
Remarks |
|
Display local public keys |
display public-key local { dsa| rsa } public [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display peer host public keys. |
display public-key peer [ brief | name publickey-name ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
Public key configuration examples
Manually specifying the peer host public key on the local device
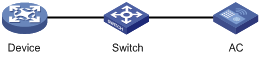
Network requirements
As shown in Figure 2, to prevent illegal access, the AC authenticates the device (the peer device) through a digital signature. Before configuring authentication parameters on the device, configure the public key of the device on the AC.
· Configure the AC to use the asymmetric key algorithm of RSA to authenticate the device.
· Manually specify the host public key of the device's public key pair on the AC.
Configuration procedure
1. Configure the device:
# Create local RSA key pairs on the device, setting the modulus length to the default, 1024 bits.
<Device> system-view
[Device] public-key local create rsa
The range of public key size is (512 ~ 2048).
NOTES: If the key modulus is greater than 512,
It will take a few minutes.
Press CTRL+C to abort.
Input the bits of the modulus[default = 1024]:
Generating Keys...
++++++
++++++
++++++++
++++++++
# Display the public keys of the local RSA key pairs.
[Device] display public-key local rsa public
=====================================================
Time of Key pair created: 09:50:06 2007/08/07
Key name: HOST_KEY
Key type: RSA Encryption Key
=====================================================
Key code:
30819F300D06092A864886F70D010101050003818D0030818902818100D90003FA95F5A44A2A2CD3F814F9854C4421B57CAC64CFFE4782A87B0360B600497D87162D1F398E6E5E51E5E353B3A9AB16C9E766BD995C669A784AD597D0FB3AA9F7202C507072B19C3C50A0D7AD3994E14ABC62DB125035EA326470034DC078B2BAA3BC3BCA80AAB5EE01986BD1EF64B42F17CCAE4A77F1EF999B2BF9C4A10203010001
=====================================================
Time of Key pair created: 09:50:07 2007/08/07
Key name: SERVER_KEY
Key type: RSA Encryption Key
=====================================================
Key code:
307C300D06092A864886F70D0101010500036B003068026100999089E7AEE9802002D9EB2D0433B87BB6158E35000AFB3FF310E42F109829D65BF70F7712507BE1A3E0BC5C2C03FAAF00DFDDC63D004B4490DACBA3CFA9E84B9151BDC7EECE1C8770D961557D192DE2B36CAF9974B7B293363BB372771C2C1F0203010001
2. Configure the AC:
# Configure the host public key of the device's RSA key pairs on the AC. In public key code view, enter the host public key of the device. The host public key is the content of HOST_KEY displayed on the device by using the display public-key local rsa public command.
<AC> system-view
[AC] public-key peer device
Public key view: return to System View with "peer-public-key end".
[AC-pkey-public-key] public-key-code begin
Public key code view: return to last view with "public-key-code end".
[AC-pkey-key-code]30819F300D06092A864886F70D010101050003818D0030818902818100D90003FA95F5A44A2A2CD3F814F9854C4421B57CAC64CFFE4782A87B0360B600497D87162D1F398E6E5E51E5E353B3A9AB16C9E766BD995C669A784AD597D0FB3AA9F7202C507072B19C3C50A0D7AD3994E14ABC62DB125035EA326470034DC078B2BAA3BC3BCA80AAB5EE01986BD1EF64B42F17CCAE4A77F1EF999B2BF9C4A10203010001
[AC-pkey-key-code] public-key-code end
[AC-pkey-public-key] peer-public-key end
# Display the host public key of the device saved on the AC.
[AC] display public-key peer name device
=====================================
Key Name : device
Key Type : RSA
Key Module: 1024
=====================================
Key Code:
30819F300D06092A864886F70D010101050003818D0030818902818100D90003FA95F5A44A2A2CD3F814F9854C4421B57CAC64CFFE4782A87B0360B600497D87162D1F398E6E5E51E5E353B3A9AB16C9E766BD995C669A784AD597D0FB3AA9F7202C507072B19C3C50A0D7AD3994E14ABC62DB125035EA326470034DC078B2BAA3BC3BCA80AAB5EE01986BD1EF64B42F17CCAE4A77F1EF999B2BF9C4A10203010001
The output shows that the host public key of the device saved on the AC is consistent with the one created on the device.
Importing a public key from a public key file
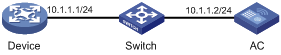
Network requirements
As shown in Figure 3, to prevent illegal access, the AC (the local device) authenticates the device (the peer device) through a digital signature. Before configuring authentication parameters on the device, configure the public key of the device on the AC
· Configure the AC to use the asymmetric key algorithm of RSA to authenticate Device A.
· Import the host public key of the device from the public key file to the AC.
Configuration procedure
1. Create key pairs on the device and export the host public key:
# Create local RSA key pairs on the device, setting the modulus length to the default, 1024 bits.
<Device> system-view
[Device] public-key local create rsa
The range of public key size is (512 ~ 2048).
NOTES: If the key modulus is greater than 512,
It will take a few minutes.
Press CTRL+C to abort.
Input the bits of the modulus[default = 1024]:
Generating Keys...
++++++
++++++
++++++++
++++++++
# Display the public keys of the local RSA key pairs.
[Device] display public-key local rsa public
=====================================================
Time of Key pair created: 09:50:06 2007/08/07
Key name: HOST_KEY
Key type: RSA Encryption Key
=====================================================
Key code:
30819F300D06092A864886F70D010101050003818D0030818902818100D90003FA95F5A44A2A2CD3F814F9854C4421B57CAC64CFFE4782A87B0360B600497D87162D1F398E6E5E51E5E353B3A9AB16C9E766BD995C669A784AD597D0FB3AA9F7202C507072B19C3C50A0D7AD3994E14ABC62DB125035EA326470034DC078B2BAA3BC3BCA80AAB5EE01986BD1EF64B42F17CCAE4A77F1EF999B2BF9C4A10203010001
=====================================================
Time of Key pair created: 09:50:07 2007/08/07
Key name: SERVER_KEY
Key type: RSA Encryption Key
=====================================================
Key code:
307C300D06092A864886F70D0101010500036B003068026100999089E7AEE9802002D9EB2D0433B87BB6158E35000AFB3FF310E42F109829D65BF70F7712507BE1A3E0BC5C2C03FAAF00DFDDC63D004B4490DACBA3CFA9E84B9151BDC7EECE1C8770D961557D192DE2B36CAF9974B7B293363BB372771C2C1F0203010001
# Export the RSA host public key HOST_KEY to a file named device.pub.
[Device] public-key local export rsa ssh2 device.pub
2. Enable the FTP server function on the device:
# Enable the FTP server function, and create an FTP user with the username ftp, password 123, and user level 3. This user level makes sure the user has the permission to perform FTP operations.
[Device] ftp server enable
[Device] local-user ftp
[Device-luser-ftp] password simple 123
[Device-luser-ftp] service-type ftp
[Device-luser-ftp] authorization-attribute level 3
[Device-luser-ftp] quit
3. On the AC, get the public key file of the device:
# From the AC, use FTP to log in to the device, and get the public key file device.pub with the file transfer mode of binary.
<AC> ftp 10.1.1.1
Trying 10.1.1.1 ...
Press CTRL+K to abort
Connected to 10.1.1.1.
220 FTP service ready.
User(10.1.1.1:(none)):ftp
331 Password required for ftp.
Password:
230 User logged in.
[ftp] binary
200 Type set to I.
[ftp] get device.pub
227 Entering Passive Mode (10,1,1,1,5,148).
125 BINARY mode data connection already open, transfer starting for /device.pub.
226 Transfer complete.
FTP: 299 byte(s) received in 0.189 second(s), 1.00Kbyte(s)/sec.
[ftp] quit
221 Server closing.
4. Import the host public key of the device to the AC:
# Import the host public key of the device from the key file device.pub to the AC.
<AC> system-view
[AC] public-key peer device import sshkey device.pub
# Display the host public key of the device on the AC.
[AC] display public-key peer name device
=====================================
Key Name : device
Key Type : RSA
Key Module: 1024
=====================================
Key Code:
30819F300D06092A864886F70D010101050003818D0030818902818100D90003FA95F5A44A2A2CD3F814F9854C4421B57CAC64CFFE4782A87B0360B600497D87162D1F398E6E5E51E5E353B3A9AB16C9E766BD995C669A784AD597D0FB3AA9F7202C507072B19C3C50A0D7AD3994E14ABC62DB125035EA326470034DC078B2BAA3BC3BCA80AAB5EE01986BD1EF64B42F17CCAE4A77F1EF999B2BF9C4A10203010001
The output shows that the host public key of the device saved on the AC is consistent with the one created on the device.

