- Table of Contents
-
- 01-Fundamentals Configuration Guide
- 00-Preface
- 01-CLI Configuration
- 02-Login Management Configuration
- 03-FTP and TFTP Configuration
- 04-File System Management
- 05-Configuration File Management Configuration
- 06-Software Upgrade Configuration
- 07-ISSU Configuration
- 08-Device Management Configuration
- 09-Automatic Configuration
- 10-Management with BootWare
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-CLI Configuration | 221.79 KB |
Contents
Using the undo form of a command
Returning to the upper-level view
Returning to user view from any view
Entering a STRING type value for an argument
Configuring and using command keyword aliases
Enabling redisplaying entered-but-not-submitted commands
Understanding command-line errors
Using the command history function
Setting the command history buffer size for user interfaces
Pausing between screens of output
Filtering the output from a display command
Configuring user privilege and command levels
Configuring a user privilege level
Switching the user privilege level
Changing the level of a command
Saving the running configuration
Displaying and maintaining CLI
At the command-line interface (CLI), you can enter text commands to configure, manage, and monitor your switch.
Figure 1 CLI example
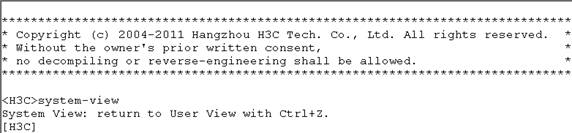
The output depends on the switch model.
Logging in to the CLI
You can log in to the CLI in a variety of ways. For example, you can log in through the console port, or by using Telnet or SSH. For more information about login methods, see "Logging in to the CLI."
Command conventions
Command conventions help you understand the syntax of commands. Commands in product manuals comply with the conventions listed in Table 1.
|
Convention |
Description |
|
Boldface |
Bold text represents commands and keywords that you enter literally as shown. |
|
Italic |
Italic text represents arguments that you replace with actual values. |
|
[ ] |
Square brackets enclose syntax choices (keywords or arguments) that are optional. |
|
{ x | y | ... } |
Braces enclose a set of required syntax choices separated by vertical bars, from which you select one. |
|
[ x | y | ... ] |
Square brackets enclose a set of optional syntax choices separated by vertical bars, from which you select one or none. |
|
{ x | y | ... } * |
Asterisk marked braces enclose a set of required syntax choices separated by vertical bars, from which you select at least one. |
|
[ x | y | ... ] * |
Asterisk marked square brackets enclose optional syntax choices separated by vertical bars, from which you select one choice, multiple choices, or none. |
|
&<1-n> |
The argument or keyword and argument combination before the ampersand (&) sign can be entered 1 to n times. |
|
# |
A line that starts with a pound (#) sign is comments. |
|
|
NOTE: Command keywords are case insensitive. |
The following example analyzes the syntax of the clock datetime time date command according to Table 1.
Figure 2 Understanding command-line parameters
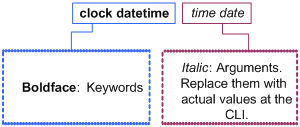
For example, to set the system time to 10:30:20, February 23, 2010, enter the following command line at the CLI and press Enter:
<Sysname> clock datetime 10:30:20 2/23/2010
Using the undo form of a command
Most configuration commands have an undo form for canceling a configuration, restoring the default, or disabling a feature. For example, the info-center enable command enables the information center, and the undo info-center enable command disables the information center.
CLI views
Commands are grouped in different views by function. To use a command, you must enter the view of the command.
CLI views are organized in a hierarchical structure, as shown in Figure 3. Each view has a unique prompt, from which you can identify where you are and what you can do. For example, the prompt [Sysname-vlan100] shows that you are in the view of VLAN 100 and can configure attributes for the VLAN.
You are placed in user view immediately after you are logged in to the CLI. The user view prompt is <Device-name>, where the Device-name argument can be changed by using the sysname command. In user view, you can perform displaying, debugging, file management, FTP, and Telnet operations, set the system time, and restart your switch. For more information about the sysname command, see Fundamentals Command Reference.
From user view, you can enter system view to configure global settings, including the daylight saving time, banners, and short-cut keys. The system view prompt is [Device-name].
From system view, you can enter different function views. For example, you can enter interface view to configure interface parameters, enter VLAN view to add ports to the specific VLAN, enter user interface view to configure login user attributes, or create a local user and enter local user view to configure attributes for the local user.
To display all commands available in a view, enter a question mark (?) at the view prompt.
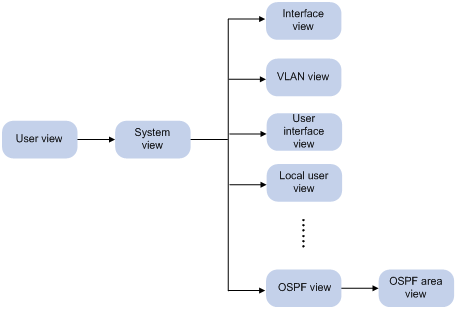
Entering system view
|
Command |
Remarks |
|
|
Enter system view from user view. |
system-view |
Available in user view. |
Returning to the upper-level view
|
Task |
Command |
Remarks |
|
Return to the upper-level view from any view. |
quit |
Available in any view. |
Executing the quit command in user view terminates your connection to the switch.
|
|
NOTE: In public key code view, use the public-key-code end command to return to the upper-level view (public key view). In public key view, use the peer-public-key end command to return to system view. |
Returning to user view from any view
You can return to user view from any other view by using the return command or pressing Ctrl+Z, instead of using the quit command multiple times.
To return to user view from any view:
|
Task |
Command |
|
Return to user view from any view. |
return |
Accessing the CLI online help
To access the CLI online help, use one of the following methods:
· Enter a question mark at a view prompt to display the first keywords of all commands available in the view. For example:
<Sysname> ?
User view commands:
cfd Connectivity fault detection (IEEE 802.1ag)
display Display current system information
ping Ping function
quit Exit from current command view
ssh2 Establish a secure shell client connection
super Set the current user priority level
telnet Establish one TELNET connection
tracert Trace route function
…
· Enter some keywords of a command and a question mark separated by a space to display available keywords and arguments.
¡ Example 1: The question mark is in the place of a keyword, and the CLI displays all possible keywords with a brief description for each keyword.
<Sysname> terminal ?
debugging Send debug information to terminal
logging Send log information to terminal
monitor Send information output to current terminal
trapping Send trap information to terminal
¡ Example 2: The question mark is in the place of an argument, and the CLI displays the description of the argument.
<Sysname> system-view
[Sysname] interface vlan-interface ?
<1-4094> VLAN interface number
[Sysname] interface vlan-interface 1 ?
<cr>
[Sysname] interface vlan-interface 1
The string <cr> indicates that the command is complete, and you can press Enter to execute the command.
· Enter an incomplete keyword string followed by a question mark to display all keywords starting with the string. For example:
<Sysname> f?
fdisk
fixdisk
format
free
ftp
<Sysname> display ftp?
ftp
ftp-server
ftp-user
Entering a command
Editing a command line
You can use the keys listed in Table 2 or the hotkeys listed in Table 3 to edit a command line.
Table 2 Keys for editing a command line
|
Key |
Function |
|
Common keys |
If the edit buffer is not full, pressing a common key inserts the character at the position of the cursor and moves the cursor to the right. |
|
Backspace |
Deletes the character to the left of the cursor and moves the cursor back one character. |
|
Left arrow key or Ctrl+B |
Moves the cursor one character to the left. |
|
Right arrow key or Ctrl+F |
Moves the cursor one character to the right. |
|
Tab |
If you press Tab after entering part of a keyword, the system automatically completes the keyword: · If a unique match is found, the system substitutes the complete keyword for the incomplete one and displays what you entered in the next line. · If there is more than one match, you can press Tab multiple times to choose the keyword you want to enter. · If there is no match, the system does not modify what you entered but displays it again in the next line. |
Entering a STRING type value for an argument
A STRING type argument value can contain any printable character (ASCII code in the range of 32 to 126) except the question mark (?).
For example, the job name is of the STRING type. You can give it a value such as saveconfiguration.
<Sysname> system-view
[Sysname]job ?
STRING<1-32> Name of the task
To enter a STRING type argument value that contains one or more spaces, put the value in a pair of quotation marks (for example, "a b"). The quotation marks are not counted in the value length.
Requirements for a STRING type value vary by command. See the parameter descriptions in the command reference.
Abbreviating commands
You can enter a command line quickly by entering incomplete keywords that can uniquely identify the complete command. In user view, for example, commands starting with an s include startup saved-configuration and system-view. To enter system view, you only need to enter sy. To set the configuration file to be used at the next startup, you can enter st s.
You can also press Tab to have an incomplete keyword automatically completed.
Configuring and using command keyword aliases
The command keyword alias function allows you to replace the first keyword of a non-undo command or the second keyword of an undo command with your preferred keyword when you execute the command. For example, if you configure show as the alias for the display keyword, you can enter show to execute a display command.
Usage guidelines
· After you successfully execute a command by using a keyword alias, the system saves the keyword, instead of its alias, to the running configuration.
· If you press Tab after entering part of an alias, the keyword is displayed.
· If a string you entered partially matches a keyword and an alias, the command indicated by the alias is executed. To execute the command indicated by the keyword, enter the complete keyword.
· If you enter a string that partially matches multiple aliases, the system gives you a prompt.
Configuration procedure
To configure a command keyword alias:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the command keyword alias function. |
command-alias enable |
By default, the command keyword alias function is disabled. |
|
3. Configure a command keyword alias. |
command-alias mapping cmdkey alias |
By default, no command keyword alias is configured. You must enter the cmdkey and alias arguments in their complete form. |
Configuring and using hotkeys
To facilitate CLI operation, the system defines some hotkeys and provides five configurable command hotkeys. Pressing a command hotkey equals entering a command. For system-reserved hotkeys, see Table 3.
To configure hotkeys:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure hotkeys. |
hotkey { CTRL_G | CTRL_L | CTRL_O | CTRL_T | CTRL_U } command |
By default: · Ctrl+G is assigned the display current-configuration command. · Ctrl+L is assigned the display ip routing-table command. · Ctrl+O is assigned the undo debugging all command. · No command is assigned to Ctrl+T or Ctrl+U. |
|
3. Display hotkeys. |
display hotkey [ | { begin | exclude | include } regular-expression ] |
Optional. Available in any view. See Table 3 for hotkeys reserved by the system. |
The hotkeys in Table 1 are defined by the device. If a hotkey is also defined by the terminal software that you are using to interact with the device, the definition of the terminal software takes effect.
Table 3 Hotkeys reserved by the system
|
Hotkey |
Function |
|
Ctrl+A |
Moves the cursor to the beginning of the line. |
|
Ctrl+B |
Moves the cursor one character to the left. |
|
Ctrl+C |
Stops the current command. |
|
Ctrl+D |
Deletes the character at the cursor. |
|
Ctrl+E |
Moves the cursor to the end of the line. |
|
Ctrl+F |
Moves the cursor one character to the right. |
|
Ctrl+H |
Deletes the character to the left of the cursor. |
|
Ctrl+K |
Aborts the connection request. |
|
Ctrl+N |
Displays the next command in the command history buffer. |
|
Ctrl+P |
Displays the previous command in the command history buffer. |
|
Ctrl+R |
Redisplays the current line. |
|
Ctrl+V |
Pastes text from the clipboard. |
|
Ctrl+W |
Deletes the word to the left of the cursor. |
|
Ctrl+X |
Deletes all characters to the left of the cursor. |
|
Ctrl+Y |
Deletes all characters to the right of the cursor. |
|
Ctrl+Z |
Returns to user view. |
|
Ctrl+] |
Terminates an incoming connection or a redirect connection. |
|
Esc+B |
Moves the cursor back one word. |
|
Esc+D |
Deletes all characters from the cursor to the end of the word. |
|
Esc+F |
Moves the cursor forward one word. |
|
Esc+N |
Moves the cursor down one line. This hotkey is available before you press Enter. |
|
Esc+P |
Moves the cursor up one line. This hotkey is available before you press Enter. |
|
Esc+< |
Moves the cursor to the beginning of the clipboard. |
|
Esc+> |
Moves the cursor to the ending of the clipboard. |
Enabling redisplaying entered-but-not-submitted commands
After you enable redisplaying entered-but-not-submitted commands:
· If you entered nothing at the command-line prompt before the system outputs system information such as logs, the system does not display the command-line prompt after the output.
· If you entered some information (except Yes or No for confirmation), the system displays a line break and then display what you have entered after the output.
To enable redisplaying entered-but-not-submitted commands:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable redisplaying entered-but-not-submitted commands. |
info-center synchronous |
Disabled by default. For more information about the info-center synchronous command, see Network Management and Monitoring Command Reference. |
Understanding command-line errors
If a command line fails the syntax checking, the CLI displays error messages.
Table 4 Common command-line error messages
|
Error message |
Cause |
|
% Unrecognized command found at '^' position. |
The keyword in the marked position is invalid. |
|
% Incomplete command found at '^' position. |
One or more required keywords or arguments are missing. |
|
% Ambiguous command found at '^' position. |
The entered character sequence matches more than one command. |
|
% Too many parameters found at '^' position. |
The entered character sequence contains excessive keywords or arguments. |
|
% Wrong parameter found at '^' position. |
The argument in the marked position is invalid. |
Using the command history function
The system can automatically save successfully executed commands to the command history buffer for the current user interface. You can view them and execute them again, or set the maximum number of commands that can be saved in the command history buffer.
A command is saved to the command history buffer in the exact format as it was entered. For example, if you enter an incomplete command, the command saved in the command history buffer is also incomplete; if you enter a command by using a command keyword alias, the command saved in the command history buffer also uses the alias.
If you execute the same command multiple times, the switch saves the earliest record. However, if you execute the same command in different formats, the system saves them as different commands. For example, if you execute the display cu command multiple times, the system saves only one command in the command history buffer. If you execute the command twice by entering display cu and display current-configuration, the system saves them as two commands.
By default, the command history buffer can save up to 10 commands for each user. To set the capacity of the command history buffer for the current user interface, use the history-command max-size command. For more information about the history-command max-size command, see Fundamentals Command Reference.
Viewing history commands
You can use arrow keys to access history commands in Windows 200x and Windows XP Terminal or Telnet. In Windows 9x HyperTerminal, the arrow keys are invalid, and you must use Ctrl+P and Ctrl+N instead.
To view command history, use one of the following methods:
|
Task |
Command |
|
Display all commands in the command history buffer. |
display history-command [ | { begin | exclude | include } regular-expression ] |
|
Display the previous history command. |
Up arrow key or Ctrl+P |
|
Display the next history command. |
Down arrow key or Ctrl+N |
Setting the command history buffer size for user interfaces
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter user interface view. |
user-interface { first-num1 [ last-num1 ] | { aux | console | vty } first-num2 [ last-num2 ] } |
N/A |
|
3. Set the maximum number of commands that can be saved in the command history buffer. |
history-command max-size size-value |
Optional. By default, the command history buffer can save up to 10 commands. |
Controlling the CLI output
This section describes the CLI output control features that help you quickly identify the desired output.
Pausing between screens of output
If the output being displayed is more than will fit on one screen, the system automatically pauses after displaying a screen. By default, up to 24 lines can be displayed on a screen. To change the screen length, use the screen-length screen-length command. For more information about this command, see Fundamentals Command Reference. To control output, use keys in Table 5.
Table 5 Keys for controlling output
|
Keys |
Function |
|
Space |
Displays the next screen. |
|
Enter |
Displays the next line. |
|
Ctrl+C |
Stops the displaying and aborts the command execution. |
|
<PageUp> |
Displays the previous page. |
|
<PageDown> |
Displays the next page. |
To display all output at one time and refresh the screen continuously until the final screen is displayed:
|
Task |
Command |
Remarks |
|
Disable pausing between screens of output for the current session. |
screen-length disable |
The default for a session depends on the setting of the screen-length command in user interface view. The default of the screen-length command is pausing between screens of output and displaying up to 24 lines on a screen. This command is executed in user view and takes effect only for the current session. When you relog in to the switch, the default is restored. |
Filtering the output from a display command
You can use one of the following methods to filter the output from a display command:
· Specify the | { begin | exclude | include } regular-expression option at the end of the command.
· When the system pauses after displaying a screen of output, enter a forward slash (/), minus sign (-), or plus sign (+) plus a regular expression to filter subsequent output. The forward slash equals the keyword begin, the minus sign equals the keyword exclude, and the plus sign equals the keyword include.
The following definitions apply to the begin, exclude, and include keywords:
· begin—Displays the first line that matches the specified regular expression and all lines that follow.
· exclude—Displays all lines that do not match the specified regular expression.
· include—Displays all lines that match the specified regular expression.
A regular expression is a case-sensitive string of 1 to 256 characters that supports the special characters in Table 6.
Table 6 Special characters supported in a regular expression
|
Character |
Meaning |
Remarks |
|
^string |
Starting sign. Matches a line that starts with string. |
For example, regular expression "^user" matches a line beginning with "user", not "Auser". |
|
string$ |
Ending sign. Matches a line that ends with string. |
For example, regular expression "user$" only matches a line ending with "user", not "userA". |
|
. |
Matches any single character, such as a single character, a special character, and a blank. |
For example, ".s" matches both "as" and "bs". |
|
* |
Matches the preceding character or character group zero or multiple times. |
For example, "zo*" matches "z" and "zoo"; "(zo)*" matches "zo" and "zozo". |
|
+ |
Matches the preceding character or character group one or multiple times |
For example, "zo+" matches "zo" and "zoo", but not "z". |
|
| |
Matches the preceding or succeeding character string |
For example, "def|int" only matches a character string containing "def" or "int". |
|
_ |
If it is at the beginning or the end of a regular expression, it equals ^ or $. In other cases, it equals comma, space, round bracket, or curly bracket. |
For example, "a_b" matches "a b" or "a(b"; "_ab" only matches a line starting with "ab"; "ab_" only matches a line ending with "ab". |
|
- |
It connects two values (the smaller one before it and the bigger one after it) to indicate a range together with [ ]. |
For example, "1-9" means 1 to 9 (inclusive); "a-h" means a to h (inclusive). |
|
[ ] |
Matches a single character contained within the brackets. |
For example, [16A] matches a string containing any character among 1, 6, and A; [1-36A] matches a string containing any character among 1, 2, 3, 6, and A (- is a hyphen). "]" can be matched as a common character only when it is put at the beginning of characters within the brackets, for example [ ]string]. There is no such limit on "[". |
|
( ) |
A character group. It is usually used with "+" or "*". |
For example, (123A) means a character group "123A"; "408(12)+" matches 40812 or 408121212. But it does not match 408. |
|
\index |
Repeats the character string specified by the index. A character string refers to the string within () before \. index refers to the sequence number (starting from 1 from left to right) of the character group before \. If only one character group appears before \, index can only be 1; if n character groups appear before index, index can be any integer from 1 to n. |
For example, (string)\1 repeats string, and a matching string must contain stringstring. (string1)(string2)\2 repeats string2, and a matching string must contain string1string2string2. (string1)(string2)\1\2 repeats both string1 and string2, and a matching string must contain string1string2string1string2. |
|
[^] |
Matches a single character not contained within the brackets. |
For example, [^16A] means to match a string containing any character except 1, 6 or A, and the matching string can also contain 1, 6 or A, but cannot contain these three characters only. For example, [^16A] matches "abc" and "m16", but not 1, 16, or 16A. |
|
\<string |
Matches a character string starting with string. |
For example, "\<do" matches word "domain" and string "doa". |
|
string\> |
Matches a character string ending with string. |
For example, "do\>" matches word "undo" and string "abcdo". |
|
\bcharacter2 |
Matches character1character2. character1 can be any character except number, letter or underline, and \b equals [^A-Za-z0-9_]. |
For example, "\ba" matches "-a" with "-" being character1, and "a" being character2, but it does not match "2a" or "ba". |
|
\Bcharacter |
Matches a string containing character, and no space is allowed before character. |
For example, "\Bt" matches "t" in "install", but not "t" in "big top". |
|
character1\w |
Matches character1character2. character2 must be a number, letter, or underline, and \w equals [A-Za-z0-9_]. |
For example, "v\w" matches "vlan" ("v" is character1 and "l" is character2) and "service" ( "i" is character2). |
|
\W |
Equals \b. |
For example, "\Wa" matches "-a", with "-" being character1, and "a" being character2, but does not match "2a" or "ba". |
|
\ |
Escape character. If a special character listed in this table follows \, the specific meaning of the character is removed. |
For example, "\\" matches a string containing "\", "\^" matches a string containing "^", and "\\b" matches a string containing "\b". |
The following are several regular expression examples:
# Use | begin user-interface in the display current-configuration command to match the first line of output that contains "user-interface" to the final line of output.
<Sysname> display current-configuration | begin user-interface
user-interface con 0
user-interface aux 0
user-interface vty 0 15
authentication-mode none
user privilege level 3
#
return
# Use | exclude Direct in the display ip routing-table command to filter out direct routes and display only the non-direct routes.
<Sysname> display ip routing-table | exclude Direct
Routing Tables: Public
Destination/Mask Proto Pre Cost NextHop Interface
1.1.1.0/24 Static 60 0 192.168.0.0 Vlan1
# Use | include Vlan in the display ip routing-table command to filter in route entries that contain Vlan.
<Sysname> display ip routing-table | include Vlan
Routing Tables: Public
Destination/Mask Proto Pre Cost NextHop Interface
192.168.1.0/24 Direct 0 0 192.168.1.42 Vlan999
Configuring user privilege and command levels
To avoid unauthorized access, the switch defines the user privilege levels and command levels in Table 7. User privilege levels correspond to command levels. A user logged in with a specific privilege level can use only the commands at that level or lower levels.
Table 7 Command levels and user privilege levels
|
Level |
Privilege |
Default set of commands |
|
0 |
Visit |
Includes commands for network diagnosis and commands for accessing an external switch. Configuration of commands at this level cannot survive a switch restart. Upon switch restart, the commands at this level will be restored to the default settings. Commands at this level include ping, tracert, telnet and ssh2. |
|
1 |
Monitor |
Includes commands for system maintenance and service fault diagnosis. Commands at this level are not saved after being configured. After the switch is restarted, the commands at this level will be restored to the default settings. Commands at this level include debugging, terminal, refresh, and send. |
|
2 |
System |
Includes service configuration commands, including routing configuration commands and commands for configuring services at different network levels. By default, commands at this level include all configuration commands except for those at manage level. |
|
3 |
Manage |
Includes commands that influence the basic operation of the system and commands for configuring system support modules. By default, commands at this level involve the configuration commands of file system, FTP, TFTP, Xmodem download, user management, level setting, and parameter settings within a system, which are not defined by any protocols or RFCs. |
Configuring a user privilege level
If the authentication mode on a user interface is scheme, configure a user privilege level for users that access the interface by using the AAA module or directly on the user interface. For SSH users that use public-key authentication, the user privilege level configured directly on the user interface always takes effect. For other users, the user privilege level configured in the AAA module has priority over the one configured directly on the user interface.
If the authentication mode on a user interface is none or password, configure the user privilege level directly on the user interface.
For more information about user login authentication, see "Logging in to the CLI." For more information about AAA and SSH, see Security Configuration Guide.
Configuring a user privilege level for users by using the AAA module
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter user interface view. |
user-interface { first-num1 [ last-num1 ] | { aux | console | vty } first-num2 [ last-num2 ] } |
N/A |
|
3. Specify the scheme authentication mode. |
authentication-mode scheme |
By default, the authentication mode for VTY and AUX users is password, and no authentication is needed for console users. |
|
4. Return to system view. |
quit |
N/A |
|
5. Configure the authentication mode for SSH users as password. |
For more information, see Security Configuration Guide. |
This task is required only for SSH users that are required to provide their usernames and passwords for authentication. |
|
6. Configure the user privilege level by using the AAA module. |
· To use local authentication: a. Use the local-user command to create a local user and enter local user view. b. Use the level keyword in the authorization-attribute command to configure the user privilege level. · To use remote authentication
(RADIUS, HWTACACS, or LDAP): |
User either method. For local authentication, if you do not configure the user privilege level, the user privilege level is 0. For remote authentication, if you do not configure the user privilege level, the user privilege level depends on the default configuration of the authentication server. For more information about the local-user and authorization-attribute commands, see Security Command Reference. |
For example:
# Configure the switch to use local authentication for Telnet users on VTY 1, and set the user privilege level to 3.
<Sysname> system-view
[Sysname] user-interface vty 1
[Sysname-ui-vty1] authentication-mode scheme
[Sysname-ui-vty1] quit
[Sysname] local-user test
[Sysname-luser-test] password cipher 123
[Sysname-luser-test] service-type telnet
When users Telnet to the switch through VTY 1, they must enter username test and password 12345678. After passing the authentication, the users can only use level-0 commands.
# Assign commands of levels 0 through 3 to the users.
[Sysname-luser-test] authorization-attribute level 3
Configuring the user privilege level directly on a user interface
To configure the user privilege level directly on a user interface that uses the scheme authentication mode:
|
Step |
Command |
Remarks |
|
1. Configure the authentication type for SSH users as publickey. |
For more information, see Security Configuration Guide. |
Required if the SSH login mode is adopted, and only the username is needed during authentication. You must also set the authentication mode of the user interfaces to scheme. |
|
2. Enter system view. |
system-view |
N/A |
|
3. Enter user interface view. |
user-interface { first-num1 [ last-num1 ] | vty first-num2 [ last-num2 ] } |
N/A |
|
4. Configure the authentication mode for any user that uses the current user interface to log in to the switch. |
authentication-mode scheme |
By default, the authentication mode for VTY and AUX users is password, and no authentication is needed for console users. |
|
5. Configure the privilege level for users that log in through the current user interface. |
user privilege level level |
Optional. By default, the user privilege level for users logged in through the console user interface is 3, and that for users logged in through the other user interfaces is 0. |
To configure the user privilege level directly on a user interface that uses the none or password authentication mode:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter user interface view. |
user-interface { first-num1 [ last-num1 ] | { aux | console | vty } first-num2 [ last-num2 ] } |
N/A |
|
3. Configure the authentication mode for any user who uses the current user interface to log in to the switch. |
authentication-mode { none | password } |
Optional. By default, the authentication mode for VTY and AUX user interfaces is password, and no authentication is needed for console users. |
|
4. Configure the privilege level of users logged in through the current user interface. |
user privilege level level |
Optional. By default, the user privilege level for users logged in through the console user interface is 3, and that for users logged in through the other user interfaces is 0. |
For example:
# Display the commands a Telnet user can use by default after login.
<Sysname> ?
User view commands:
display Display current system information
ping Ping function
quit Exit from current command view
ssh2 Establish a secure shell client connection
super Set the current user priority level
telnet Establish one TELNET connection
# Configure the switch to perform no authentication for Telnet users, and to authorize authenticated Telnet users to use level-0 and level-1 commands. (Use no authentication mode only in a secure network environment.)
<Sysname> system-view
[Sysname] user-interface vty 0 15
[Sysname-ui-vty0-15] authentication-mode none
[Sysname-ui-vty0-15] user privilege level 1
# Display the commands a Telnet user can use after login. Because the user privilege level is 1, a Telnet user can use more commands now.
<Sysname> ?
User view commands:
debugging Enable system debugging functions
display Display current system information
graceful-restart Graceful restart
ipc Interprocess communication
oap Open application platform operation
ping Ping function
quit Exit from current command view
refresh Do soft reset
reset Reset operation
screen-length Specify the lines displayed on one screen
send Send information to other user terminal interface
ssh2 Establish a secure shell client connection
super Set the current user priority level
telnet Establish one TELNET connection
terminal Set the terminal line characteristics
tracert Trace route function
undo Cancel current setting
# Configure the switch to perform password authentication for Telnet users, and to authorize authenticated Telnet users to use the commands of privilege levels 0, 1, and 2.
<Sysname> system-view
[Sysname] user-interface vty 0 15
[Sysname-ui-vty0-15] authentication-mode password
[Sysname-ui-vty0-15] set authentication password cipher 123
[Sysname-ui-vty0-15] user privilege level 2
After the configuration is complete, when users Telnet to the switch, they must enter the password 12345678. After passing authentication, they can use commands of levels 0, 1, and 2.
Switching the user privilege level
Users can switch to a different user privilege level without logging out and terminating the current connection. After the privilege level switching, users can continue to manage the switch without relogging in, but the commands they can execute have changed. For example, with the user privilege level 3, a user can configure system parameters. After switching to user privilege level 0, the user can execute only basic commands like ping and tracert and use a few display commands. The switching operation is effective for the current login. After the user relogs in, the user privilege restores to the original level.
To avoid problems, H3C recommends that administrators log in with a lower privilege level to view switch operating parameters, and switch to a higher level temporarily only when they must maintain the switch.
When an administrator must leave for a while or ask someone else to manage the switch temporarily, they can switch to a lower privilege level before they leave to restrict the operation by others.
Configuring the authentication parameters for user privilege level switching
A user can switch to a privilege level equal to or lower than the current one unconditionally and is not required to enter a password (if any).
For security, a user is required to enter a password (if any) to switch to a higher privilege level. The authentication modes are as follows:
|
Keywords |
Authentication mode |
Description |
|
local |
Local password authentication only (local-only) |
The switch authenticates a user by using the privilege level switching password entered by the user. To use this mode, you must set the password for privilege level switching by using the super password command. |
|
scheme |
Remote AAA authentication through HWTACACS or RADIUS |
The switch sends the username and password for privilege level switching to the HWTACACS or RADIUS server for remote authentication. To use this mode, you must perform the following configuration tasks: · Configure the required HWTACACS or RADIUS schemes and configure the ISP domain to use the schemes for users. For more information, see Security Configuration Guide. · Add user accounts and specify the user passwords on the HWTACACS or RADIUS server. |
|
local scheme |
Local password authentication first and then remote AAA authentication |
The switch authenticates a user by using the local password first, and if no password for privilege level switching is set, for the user logged in from the console port, the privilege level is switched directly; for the user logged in from any of the AUX or VTY user interfaces, the AAA authentication is performed. |
|
scheme local |
Remote AAA authentication first and then local password authentication |
AAA authentication is performed first, and if the remote HWTACACS or RADIUS server does not respond or AAA configuration on the switch is invalid, the local password authentication is performed. |
To configure the authentication parameters for a user privilege level:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the authentication mode for user privilege level switching. |
super authentication-mode { local | scheme } * |
Optional. By default, local-only authentication is used. |
|
3. Configure the password for user privilege level switching. |
super password [ level user-level ] [ hash ] { simple | cipher } password |
This step is required when local authentication is involved. By default, a privilege level has no password. The hash keyword is not supported in FIPS mode. Executing this command without specifying the user privilege level, configures a password for user privilege level 3. You cannot configure the super password [ level user-level ] hash cipher password command when the password-control enable command is configured. |
If local-only authentication is used, a console user interface user can switch to a higher privilege level, even if the privilege level has not been assigned a password. Console user interface users include users logged in through the console port and users logged in through the AUX port used as the console port.
Switching the user privilege level
Before switching to a higher user privilege level, obtain the required authentication data as described in Table 8.
When the level switching authentication mode is scheme, you have three opportunities to enter the correct password for one switching operation.
When the level switching authentication mode is local, you have five opportunities to enter the correct password for one switching operation. If you fail to provide the correct password during five consecutive attempts, the switching operation fails. If the login authentication mode is scheme, you must wait 15 minutes before you can perform another switching operation.
To switch the user privilege level, perform the following task in user view:
|
Task |
Command |
Remarks |
|
Switch the user privilege level. |
super [ level ] |
When logging in to the switch, a user has a user privilege level, which depends on user interface or authentication user level. |
When you switch the user privilege level, the information you must provide varies with combinations of the user interface authentication mode and the super authentication mode.
For more information about user interface authentication, see "Logging in to the CLI."
Table 8 Information required for user privilege level switching
|
User interface authentication mode |
User privilege level switching authentication mode |
Information required for the first authentication mode |
Information required for the second authentication mode |
|
none/password |
local |
Password configured for the privilege level on the switch with the super password command |
N/A |
|
local scheme |
Password configured for the privilege level on the switch with the super password command |
Username and password configured on the AAA server for the privilege level |
|
|
scheme |
Username and password for the privilege level |
N/A |
|
|
scheme local |
Username and password for the privilege level |
Local user privilege level switching password. |
|
|
scheme |
local |
Password configured for the privilege level on the device with the super password command |
N/A |
|
local scheme |
Password configured for the privilege level on the device with the super password command |
Password for privilege level switching configured on the AAA server. The system uses the login username as the privilege level switching username. |
|
|
scheme |
Password for privilege level switching configured on the AAA server. The system uses the login username as the privilege level switching username. |
N/A |
|
|
scheme local |
Password for privilege level switching configured on the AAA server. The system uses the login username as the privilege level switching username. |
Local user privilege level switching password. |
Changing the level of a command
Every command in a view has a default command level. The default command level scheme is sufficient for the security and ease of maintenance requirements of most networks. If you want to change the level of a command, make sure that the change does not result in any security risk or maintenance problem.
To change the level of a command:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Change the level of a command in a specific view |
command-privilege level level view view command |
See Table 7 for the default settings. |
Saving the running configuration
You can use the save command in any view to save all the submitted and executed commands into the configuration file. Commands saved in the configuration file can survive a reboot. The save command does not take effect on one-time commands, including display and reset commands. One-time commands are never saved.
Displaying and maintaining CLI
|
Task |
Command |
Remarks |
|
Display the command keyword alias configuration. |
display command-alias [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display data in the clipboard. |
display clipboard [ | { begin | exclude | include } regular-expression ] |
Available in any view. |

