- Table of Contents
-
- 04-DPI Configuration Guide
- 00-Preface
- 01-DPI overview
- 02-DPI engine configuration
- 03-IPS configuration
- 04-URL filtering configuration
- 05-Data filtering configuration
- 06-File filtering configuration
- 07-Anti-virus configuration
- 08-Data analysis center configuration
- 09-Proxy policy configuration
- 10-WAF configuration
- 11-APT defense configuration
- 12-IP reputation configuration
- 13-Domain reputation configuration
- 14-DGA detection configuration
- 15-Intelligent service platform configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 10-WAF configuration | 385.99 KB |
Contents
WAF signature library management
Restrictions: Licensing requirements for WAF
Restrictions and guidelines: WAF
Configuring WAF signature filtering
Configuring common settings for WAF protection
Configuring extended WAF functions
Configuring WAF signature filtering
Configuring WAF signature filtering criteria for a WAF policy
Configuring actions in a WAF policy
Specifying a parameter profile for a WAF action
Applying a CC defense policy to a WAF policy
Configuring common settings for WAF protection
Activating WAF policy settings
Applying a WAF policy to a DPI application profile
Applying a DPI application profile
Managing a user-defined WAF signature
Creating a user-defined WAF signature
Configuring attributes in a user-defined WAF signature
Configure rules for a user-defined WAF signature
Managing the WAF signature library
Scheduling automatic WAF signature library update
Triggering an immediate WAF signature update
Performing a WAF signature manual update
Rolling back the WAF signature library
Configuring server information hiding
Display and maintenance commands for WAF
Example: Using the default WAF policy in a security policy
Example: Using a user-defined WAF policy in a security policy
Example: Manually updating the WAF signature library
Example: Configuring automatic WAF signature library update
Configuring WAF
About WAF
The Web application firewall (WAF) feature protects the internal clients and Web servers by preventing Web application layer attacks. The device monitors HTTP and HTTPS traffic to and from Web applications for malicious activity and proactively take prevention actions.
WAF protection
The WAF feature implements its functions through WAF signature filtering, semantic analysis, CC defense, and Web tamper proof.
WAF signature filtering
The device monitors and blocks network attacks by comparing packets with WAF signatures in a WAF policy.
Semantic analysis
Semantic analysis analyzes the semantics of SQL statements to detect SQL injection attacks to protect internal users and servers.
CC defense
The Challenge Collapsar (CC) attack is a kind of distributed denial of service (DDoS) attack. The CC defense feature blocks malicious traffic from Web applications by performing content inspection, rule matching, and statistics collection.
Web tamper proof
The tamper proof feature detects whether the webpages to be accessed by clients are tampered with and repairs tampered webpages before sending webpage contents to clients. This feature prevents clients being attacked by accessing tampered webpages, for example, phishing websites.
WAF signature filtering
WAF signature filtering is implemented based on WAF policies. A WAF policy contains a set of WAF signatures for matching packets and the actions on the packets.
WAF signatures
The device compares packets with WAF signatures to detect, classify, and prevent network attacks.
Each WAF signature contains various attributes, including attack category, action, protected target, severity level, and direction. You can filter the WAF signatures that a WAF policy uses based on the WAF signature attributes.
The device supports the following types of WAF signatures:
· Predefined WAF signatures—Automatically generated by the device based on the local signature library. You cannot add, modify, or delete a predefined WAF signature.
· User-defined WAF signatures—Manually created. For new attacks that cannot be detected by predefined signatures, you can create user-defined WAF signatures. If you do not quite understand the characteristics of the new attacks, do not create user-defined WAF signatures.
WAF actions
When the device detects a matching packet for a WAF policy, it takes the actions specified for the WAF policy on the packet.
The device supports the following signature actions:
· Drop—Drops matching packets.
· Permit—Permits matching packets to pass through.
· Reset—Closes the TCP connections for matching packets by sending TCP reset messages.
· Redirect—Redirects matching packets to a webpage.
· Block-source—Drops matching packets and adds the packet sources to the IP blacklist. If the IP blacklist feature is enabled, the device blocks the packets from the blacklisted sources for a duration set by the block-period command. If the IP blacklist feature is not enabled, the device does not block the packets from the blacklisted sources.
To enable the IP blacklist feature, use the blacklist global enable command. For more information about the IP blacklist feature, see Security Configuration Guide.
For more information about the block-period command, see DPI Command Reference.
· Capture—Captures matching packets.
· Logging—Logs matching packets.
WAF signature filtering mechanism
WAF signature filtering takes effect after you apply a WAF policy to a DPI application profile and use the DPI application profile in a security policy rule.
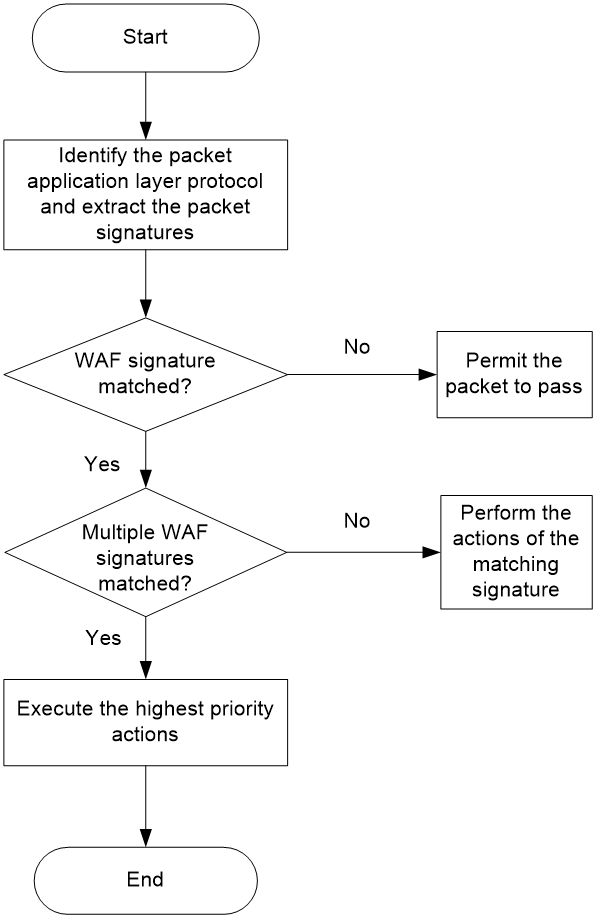
As shown in Figure 1, upon receiving a packet, the device performs the following operations:
1. The device identifies the packet application layer protocol and extracts the packet signatures.
2. The device determines the actions for the packet by comparing the extracted packet signatures with the WAF signatures in the WAF policy:
¡ If the packet does not match any WAF signatures, the device permits the packet to pass.
¡ If the packet matches only one WAF signature, the device takes the signature actions.
¡ If the packet matches multiple WAF signatures, the device uses the following rules to select the actions:
- If the matching WAF signatures have two or more actions, including redirect, drop, permit, and reset, the device takes the action of the highest priority. The actions in descending order of priority are reset, redirect, drop, and permit.
- The device executes the block-source, capture, and logging actions if they are in the matching WAF signatures.
Figure 1 WAF signature filtering mechanism
Semantic analysis
The device performs semantic analysis on the SQL statements extracted from a packet to determine if the packet is an attack packet.
· If the packet is an attack packet, the device selects the action for the packet as follows:
¡ If WAF actions are specified, the device takes the specified actions for the packet.
¡ If no WAF action is specified, the device permits the packet to pass through and sends a WAF log to the fast log output server. For more information about WAF actions, see "WAF signature filtering."
· If the packet is not an attack packet, the device permits the packet to pass through.
Web tamper proof
The device saves a webpage file as a baseline file after learning a static webpage resource accessed by the client under normal circumstances. You can determine whether the device is under normal circumstances depending on actual conditions, including the networking diagram and network status. When the client accesses the webpage again, the device compares the resource file in the response returned from the server with the baseline file to identify whether the webpage is tampered with.
Tamper proof operating mechanism
Web tamper proof operates through the following phases:
1. Generating baseline files.
The device enters the learning state after tamper proof is enabled. In this state, the device learns webpage resource files in the responses returned from the server and generates baseline files when the client accesses the webpage resources. The device learns only the following webpage resources:
¡ Resources that meet the following requirements:
- The request method in the URL requested by the client is GET.
- The resource file type is a file type that can be detected by tamper proof.
¡ Resources in the paths of static webpage resources. If the webpage resources do not meet the above learning requirements, you can manually add resource paths. The tamper proof feature will learn webpage resources in these paths.
2. Manually switching tamper proof state.
You can determine whether the device has finished learning by viewing the auto learned URL list from the Web interface. If learning has finished, disable Webpage auto learning for tamper proof to enter the working state.
Since static webpage resources of the server might change, you can execute the reset waf tamper-proof baseline-file command for the device to clear baseline files and relearn baseline files. This can prevent tamper proof generating reports mistakenly because of old baseline files.
3. Comparing the webpage resources with the baseline files.
In the working state, the device compares the webpage resources in the responses returned from the server with the baseline files, and then performs the following operations as needed:
¡ If they are the same, the webpage resources are not tampered with, and the responses are permitted to pass through.
¡ If they are different, the webpage resources are tampered with. Then, the device takes actions depending on the operating mode of tamper proof. For more information about tamper proof operating modes, see "Operating mode of tamper proof."
¡ If the webpage resources have not been saved as baseline files and meet tamper proof learning requirements, the device will save them as baseline files and generate log messages. You can view information about tamper proof log messages on the Web tamper proof logs page from the Web interface.
¡ If the webpage resources have not been saved as baseline files and do not meet tamper proof learning requirements, the device permit the responses to pass through.
Operating mode of tamper proof
The operating modes of tamper proof include the following:
· Monitor mode—The device only generates a log message when it detects that webpages to be accessed by clients are tampered with.
· Protection mode—When the device detects a tampered webpage, it replaces the webpage resource file in the response from the server with the auto-learned webpage baseline file before sending the response to clients. The device also generates a log message for the tempered webpage. You can view information about tamper proof log messages on the Web tamper proof logs page from the Web interface.
This mode takes effect only when TCP proxy or SSL proxy is configured. For more information about TCP proxy and SSL proxy, see "Configuring the proxy policy."
CC defense
The device detects CC attacks based on CC defense policies. A CC defense policy defines the packet filtering criteria, detection items, and actions on matching packets.
Detection items
The detection items include the following:
· Request rate—Identifies whether a client is accessing a website too frequently.
· Request concentration ratio—Identifies whether a website is most frequently accessed.
Each detection item has a threshold. The device compares the calculated statistics with the thresholds. A CC attack occurs if a threshold is reached.
CC defense mechanism
The CC defense feature is used in a WAF policy that is associated with a security policy.
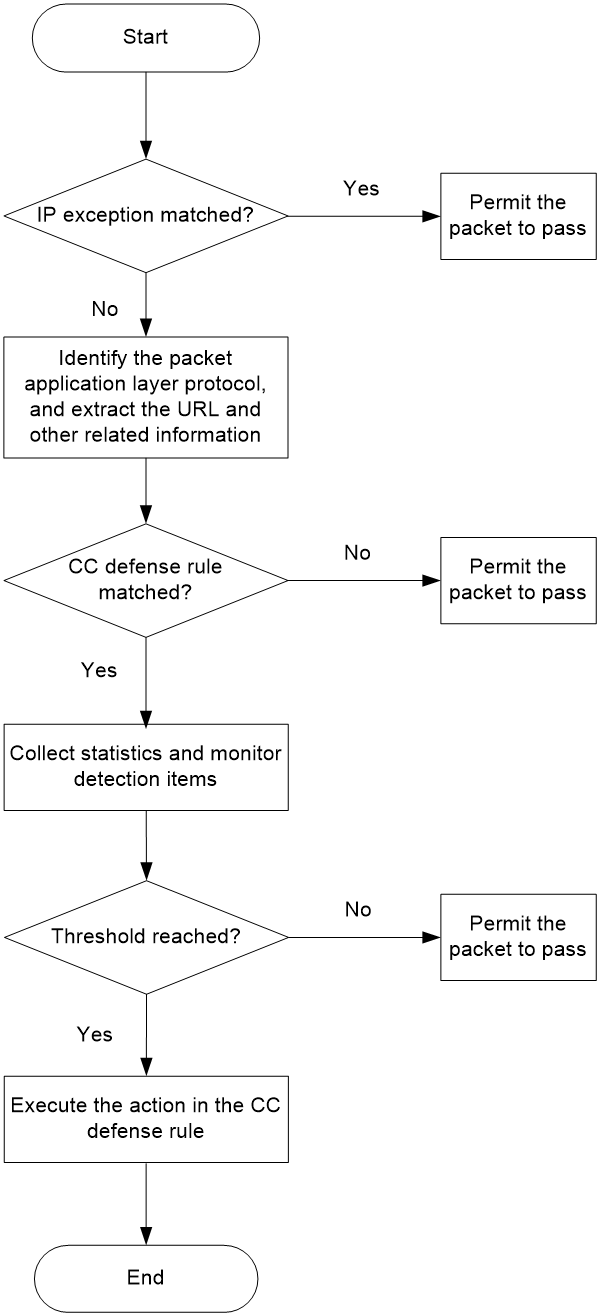
As shown in Figure 2, upon receiving a packet, the device performs the following operations:
1. The device compares the packet with IP exceptions.
¡ If an IP exception is found, the device permits the packet to pass through.
¡ If no IP exception is found, the device goes to step 2.
2. The device identifies the packet application layer protocol, and extracts the URL and other related information.
3. The device compares the extracted packet information with the CC defense rules and determines the action on the packet.
¡ If the packet does not match any CC defense rules, the device permits the packet to pass through.
¡ If the packet matches one CC defense rule, the device stops the matching process and goes to step 4.
4. The device calculates statistics and compares the calculation result with the detection item thresholds in real time.
¡ If no threshold is reached, the device permits the packet to pass through.
¡ If a threshold is reached, the device executes the action on the matching packet.
WAF protection actions
If a packet matches WAF signatures, semantic analysis, and a CC defense rule, the device takes the action of the highest priority among the WAF signatures, semantic analysis, and CC defense rule. The actions in descending order of priority are reset, redirect, drop, and permit. The device will execute the blacklist, capture, and logging actions if they are configured for the matching WAF signatures, semantic analysis, or CC defense rule.
WAF signature library management
The device uses WAF signatures to inspect Web application layer traffic for malicious threats and attacks.
You can update the device WAF signature library to the latest version or roll back the library to the previous or the factory default version.
Updating the WAF signature library
The following methods are available for updating the WAF signature library on the device:
· Automatic update.
The device automatically downloads the most up-to-date WAF signature file to update its local signature library periodically.
· Triggered update.
The device downloads the most up-to-date WAF signature file to update its local signature library immediately after you trigger the operation.
· Manual update.
Use this method when the device cannot obtain the WAF signature file automatically.
You must manually download the most up-to-date WAF signature file, and then use the file to update the signature library on the device.
Rolling back the WAF signature library
If filtering false alarms or filtering exceptions occur frequently, you can roll back the WAF signature library to the previous version or to the factory default version.
Restrictions: Licensing requirements for WAF
The WAF module requires a license to run on the device. If the license expires, you can still use the WAF functions but you cannot upgrade the WAF signature library to the version released after the expiration time. For more information about licenses, see license management in Fundamentals Configuration Guide.
Restrictions and guidelines: WAF
The capture action for WAF will not take effect if you enable SSL proxy or TCP proxy, or enable alarm message sending for the anti-virus feature. For more information about SSL proxy and TCP proxy, see "Configuring the proxy policy." For more information about the anti-virus feature, see "Configuring anti-virus."
WAF tasks at a glance
Configuring WAF signature filtering
2. Configuring WAF signature filtering criteria for a WAF policy
3. Configuring actions in a WAF policy
4. Specifying a parameter profile for a WAF action
Configuring semantic analysis
Configuring Web tamper proof
2. Configuring Web tamper proof
3. Switching tamper proof state
Configuring CC defense
2. Creating a CC defense policy
4. Applying a CC defense policy to a WAF policy
5. (Optional.) Managing CC defense rules
Configuring common settings for WAF protection
1. (Optional.) Activating WAF policy settings
2. Applying a WAF policy to a DPI application profile
3. Applying a DPI application profile to a security policy rule
Configuring extended WAF functions
1. (Optional.) Managing a user-defined WAF signature
2. (Optional.) Managing the WAF signature library
3. (Optional.) Configuring WAF whitelist
4. (Optional.) Configuring server information hiding
Configuring WAF signature filtering
Creating a WAF policy
About this task
By default, a newly created WAF policy uses all enabled WAF signatures and applies to the packet matching a signature the default signature action. You can filter the WAF signatures used by the WAF policy and configure the WAF actions.
Procedure
1. Enter system view.
system-view
2. Create a WAF policy and enter its view.
waf policy policy-name
By default, a default WAF policy named default exists. The default WAF policy uses all enabled WAF signatures on the device and cannot be modified or deleted.
3. (Optional.) Specify an alias and tenant ID for a WAF policy in a Yundi network
yundi alias alias-name tenant tenant-id
By default, no alias or tenant ID is specified for a WAF policy in a Yundi network.
Aliases and tenant IDs are typically deployed by the controller. As a best practice, do not configure aliases or tenant IDs on the device.
Configuring WAF signature filtering criteria for a WAF policy
About this task
By default, a WAF policy uses all enabled WAF signatures on the device. You can set criteria to filter WAF signatures that a WAF policy uses based on the signature attributes.
A WAF policy uses a WAF signature only if the signature matches all the configured criteria.
For certain attribute-based criterion (such as the action, direction, or severity level criterion), you can specify multiple attribute values. A WAF signature matches the criterion if it matches any of the specified attribute values.
Procedure
1. Enter system view.
system-view
2. Enter WAF policy view.
waf policy policy-name
3. Configure the WAF signature filtering criteria.
¡ Set a target criterion.
protected-target { target [ sub-target subtarget ]| all }
By default, the target attribute is not used for WAF signature filtering.
¡ Set an attack category criterion.
attack-category { sub-category subcategory ] | all }
By default, the attack category attribute is not used for WAF signature filtering.
¡ Set an action criterion.
action { block-source | drop | permit | reset } *
By default, the action attribute is not used for WAF signature filtering.
¡ Set a direction criterion.
object-dir { client | server } *
By default, the direction attribute is not used for WAF signature filtering.
¡ Set a severity level criterion.
severity-level { critical | high | low | medium } *
By default, the severity level attribute is not used for WAF signature filtering.
Configuring actions in a WAF policy
About this task
By default, the system applies the default actions of a WAF signature to packets matching the signature.
You can also configure global actions for a WAF policy or change the actions for individual WAF signatures in the policy.
The system selects the actions for packets matching a WAF signature in the following order:
1. Actions configured for the WAF signature in the WAF policy.
2. Actions configured for the WAF policy.
3. Default actions of the WAF signature.
Restrictions and guidelines
The logging keyword enables the WAF module to log packet matching events and use one of the following methods to send log messages:
· Fast log output—You must specify a log host to receive the log messages. Log messages are sent to the specified log host.
· Syslog output—Log messages are sent to the information center. With the information center, you can set log message filtering and output rules, including output destinations. The information center can output WAF syslogs to any destinations except the console and the monitor terminal. If you configure the console or monitor terminal as an output destination, the output destination setting will not take effect. To view WAF syslogs stored on the device, use the display logbuffer command. Make sure you do not disable log output to the log buffer, which is enabled by default.
Syslog output might affect device performance. As a best practice, use fast log output.
For more information about configuring the information center, see Network Management and Monitoring Configuration Guide. For more information about fast log output, see Network Management and Monitoring Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enter the view of a WAF policy.
waf policy policy-name
3. Specify the WAF actions for the WAF policy.
signature override all { { block-source | drop | permit | redirect | reset } | capture | logging } *
By default, no actions are specified for a WAF policy and the default actions of WAF signatures are applied to matching packets.
4. (Optional.) Change the status or actions for a WAF signature.
signature override pre-defined signature-id { disable | enable } [ { block-source | drop | permit | redirect | reset } | capture | logging ] *
By default, the predefined WAF signatures use the actions and statuses defined by the system.
Specifying a parameter profile for a WAF action
About this task
You can specify parameter profiles for WAF actions. A parameter profile is a set of parameters that determine how an action is executed. If you do not specify a parameter profile for an action, or if the specified profile does not exist, the default action parameter settings are used. For information about configuring parameter profiles, see "Configuring DPI engine."
Procedure
1. Enter system view.
system-view
2. Specify a parameter profile for a WAF action.
waf { block-source | capture | email | logging | redirect } parameter-profile parameter-name
By default, no parameter profile is specified for a WAF action.
Configuring semantic analysis
Creating a WAF policy
1. Enter system view.
system-view
2. Create a WAF policy and enter its view.
waf policy policy-name
By default, a default WAF policy named default exists, and the policy is not editable.
3. (Optional.) Specify a description for the WAF policy.
description text
4. (Optional.) Specify an alias and tenant ID for a WAF policy in a Yundi network
yundi alias alias-name tenant tenant-id
By default, no alias or tenant ID is specified for a WAF policy in a Yundi network.
Aliases and tenant IDs are typically deployed by the controller. As a best practice, do not configure aliases or tenant IDs on the device.
Enabling semantic analysis
About this task
If semantic analysis is enabled, the device uses both semantic analysis and signature matching to improve the detection rate of SQL injection attacks. You can enable semantic analysis as needed because this feature might affect the device performance.
Restrictions and guidelines
As a best practice, enable semantic analysis only if necessary, because this feature will affect the device performance
Procedure
1. Enter system view.
system-view
2. Enter the view of a WAF policy.
waf policy policy-name
3. Enable semantic analysis.
semantic-analysis enable
By default, semantic analysis is disabled.
Configuring Web tamper proof
Restrictions and guidelines
If no hard disk or USB disk is installed, the device saves baseline files in memory. If a hard disk or USB disk is installed, baseline files are saved to the hard disk or USB disk and can survive device reboots. The device saves baseline files to a USB disk only when no hard disk is installed.
If the hard disk usage or USB disk usage has reached the upper limit, Web tamper proof stops operating.
The device performs tamper proof detection only on static webpage resources.
Creating a WAF policy
1. Enter system view.
system-view
2. Create a WAF policy and enter its view.
waf policy policy-name
By default, a default WAF policy named default exists, and the policy is not editable.
Enabling Web tamper proof
1. Enable Web tamper proof.
tamper-proof enable
By default, Web tamper proof is disabled.
2. (Optional.) Add a path of static webpage resources to be learned by tamper proof.
tamper-proof web-resources host method uri
Execute this command to add a path of webpage resources, the device will learn the webpage resources in the path if the webpage resources do not meet auto learning requirements. For example, the file types of webpage resources are not supported by tamper proof detection or the request method of client requests is not GET.
3. (Optional.) Clear baseline files for tamper proof in a WAF policy.
reset waf tamper-proof baseline-file [ policy-name ]
You can execute this command for the device to clear baseline files and relearn baseline files when you consider that the webpage resource contents of the server have changed regularly.
Switching tamper proof state
1. Disable webpage auto learning for tamper proof.
undo tamper-proof auto-learn enable
By default, webpage auto learning is enabled.
You can determine whether the device has finished learning by viewing the auto learned URL list from the Web interface. If learning has finished, use this command to disable Webpage auto learning for tamper proof to switch to the working state.
2. (Optional.) Set the operating mode of Web tamper proof to the protection mode.
tamper-proof work-mode protect
By default, Web tamper proof operates in monitor mode.
This command takes effect only when the device is configured with the proxy policy. If no proxy policy is configured, the device only generates a log message when the device detects a webpage resource that is tampered with. For more information about the proxy policy, see "Configuring the proxy policy."
3. (Optional.) Disable tamper proof on a file type.
undo tamper-proof file-type file-type enable
By default, tamper proof detects the following types of files: XLS, HLP, CHM, PPT, DOC, PE, PDF, SWF, ZIP, GIF, JPEG, CSS, HTML, and TXT.
4. (Optional.) Disable file caching for tampered files.
undo waf tamper-proof cache-files enable
By default, file caching is enabled for tampered files and takes effect only when a storage medium (hard disk or USB disk) is installed.
When the device detects that a webpage resource file returned from the server has been tampered with, the device will cache the file as a tampered file to a storage medium (hard disk or USB disk). You can download tampered files on the Web tamper proof logs page from the Web interface for analysis.
File caching will occupy the storage space of storage media and impact the device forwarding performance. You can disable file caching if the storage space is insufficient, the device forwarding performance is degraded, or you do not care about tampered file contents.
Configuring CC defense
Creating a WAF policy
About this task
A CC defense policy takes effect only after it is applied to a WAF policy. To use a CC defense policy, you must first create a WAF policy for associating the CC defense policy.
Procedure
1. Enter system view.
system-view
2. Create a WAF policy and enter its view.
waf policy policy-name
By default, a default WAF policy named default exists, and it is not associated with any CC defense policy. The default WAF policy uses all enabled WAF signatures on the device, and the policy is not editable.
3. (Optional.) Specify a description for the WAF policy.
description text
Creating a CC defense policy
About this task
The device detects CC attacks based on CC defense policies. You can configure filtering criteria and detection items in a CC defense policy as needed.
Procedure
1. Enter system view.
system-view
2. Create a CC defense policy and enter its view.
cc-defense policy policy-name
3. (Optional.) Configure the description for the CC defense policy.
description text-string
4. (Optional.) set the CC attack detection interval.
detection-interval interval
By default, the CC attack detection interval is 30 seconds.
5. (Optional.) Specify IP exceptions in the CC defense policy.
exception { ipv4 ipv4-address | ipv6 ipv6-address }
By default, no IP exceptions are specified in a CC defense policy.
Creating a CC defense rule
About this task
You can configure the following items in a CC defense rule:
· Packet filtering criteria, such as destination IP addresses, destination ports, and request methods.
· Protected paths.
· Detection items and their thresholds.
· Action on matching packets.
The match order of CC defense rules is the rule configuration order. If a packet matches one CC defense rule, the device stops the matching process for the packet.
Procedure
1. Enter system view.
system-view
2. Create the view of a CC defense policy.
cc-defense policy policy-name
3. Create a CC defense rule and enter its view.
rule name rule-name
4. Set the filtering criteria for the rule.
¡ Specify destination IP address filtering criteria.
destination-address { ipv4 ipv4-address | ipv6 ipv6-address }
¡ Specify destination port filtering criteria.
destination-port port-number
¡ Specify request method filtering criteria.
method { connect | delete | get | head | options | post | put | trace } *
5. Specify protected paths.
protected-url url-text
By default, no protected paths are specified in a CC defense rule.
6. Enable X-Forwarded-For inspection.
xff-detection enable
By default, X-Forwarded-For inspection is disabled.
7. Configure detection items.
cc-detection-item { request-concentration [ concentration-value ] [ request-number number ] | request-rate [ rate-value ] }
By default, no detection items are configured in a CC defense rule.
8. Specify the action on packets matching the rule.
action { block-source [ block-time ] | permit }
By default, the action is permit.
9. Enable CC defense logging.
logging enable
By default, CC defense logging is disabled.
Applying a CC defense policy to a WAF policy
1. Enter system view.
system-view
2. Enter the view of a WAF policy.
waf policy policy-name
3. Apply a CC defense policy to the WAF policy.
apply cc-defense policy policy-name
Managing CC defense rules
Rearranging CC defense rules to adjust their match order
1. Enter system view.
system-view
2. Enter the view of a CC defense policy.
cc-defense policy policy-name
3. Move a CC defense rule among the CC defense policy.
rule move rule-name1 { after | before } rule-name2
Copying a CC defense rule to create a new rule
1. Enter system view.
system-view
2. Enter the view of a CC defense policy.
cc-defense policy policy-name
3. Create a CC defense rule by copying an existing rule.
rule copy rule-name new-rule-name
Configuring common settings for WAF protection
Activating WAF policy settings
About this task
After detecting WAF policy changes, the system starts a timer to check for new changes 20 seconds later.
· If no further changes are detected when the timer expires, the system determines that the changes are final and activate the changes at the expiration of the next check interval (after 40 seconds).
· If new changes are detected, the system resets the check interval timer and continue the periodic check until it determines that the changes are final and activates the changes.
You can also use this function to manually activate WAF policy changes.
Restrictions and guidelines
You do not need to perform this task for semantic analysis and CC defense in a WAF policy, because the configuration of semantic analysis and CC defense can take effect immediately.
For more information about activating DPI service module configuration, see "Configuring DPI engine."
Procedure
1. Enter system view.
system-view
2. Activate WAF policy settings.
inspect activate
By default, changes to WAF policy settings take effect after the system automatically activates the changes during the periodic check.
|
CAUTION: This command causes transient DPI service interruption. DPI-based services might also be interrupted. For example, security policies cannot control access to applications and Layer 7 load balancing services cannot load share traffic based on applications. |
Applying a WAF policy to a DPI application profile
About this task
A WAF policy must be applied to a DPI application profile to take effect.
Restrictions and guidelines
A DPI application profile can use only one WAF policy. If you apply different WAF policies to the same DPI application profile, only the most recent configuration takes effect.
Procedure
1. Enter system view.
system-view
2. Enter DPI application profile view.
app-profile profile-name
For more information about this command, see DPI engine commands in DPI Command Reference.
3. Apply a WAF policy to the DPI application profile.
waf apply policy policy-name mode { protect | alert }
By default, no WAF policy is applied to the DPI application profile.
Applying a DPI application profile
Applying a DPI application profile to a security policy rule
1. Enter system view.
system-view
2. Enter security policy view.
security-policy { ip | ipv6 }
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Set the rule action to pass.
action pass
The default rule action is drop.
5. Use a DPI application profile in the rule.
profile app-profile-name
By default, no DPI application profile is used in a security policy rule.
Managing a user-defined WAF signature
Creating a user-defined WAF signature
About this task
You can create signatures that do not exist in the current signature library.
Procedure
1. Enter system view.
system-view
2. Create a WAF signature and enter its view.
waf signature user-defined name signature-name
By default, no user-defined WAF signatures are configured.
3. (Optional.) Configure the description for the user-defined WAF signature.
description text
Configuring attributes in a user-defined WAF signature
About this task
Each WAF signature contains various attributes, including action, direction, severity level, and the logical operator between rules in the signature.
You can create multiple rules in a user-defined WAF signature. If the logical AND operator is specified, a packet matches the signature only when the packet matches all rules in the signature. If the logical OR operator is specified, a packet matches the signature when the packet matches any rule in the signature.
Procedure
1. Enter system view.
system-view
2. Enter the view of a user-defined WAF signature.
waf signature user-defined name signature-name
By default, no user-defined WAF signatures exist.
3. Configure the attributes for the user-defined WAF signature.
¡ Set the actions on packets matching the WAF signature.
action { block-source | drop | permit | reset } [ capture | logging ] *
By default, the action is permit on packets matching a user-defined WAF signature.
¡ Set the traffic direction attribute.
direction { any | to-client | to-server }
By default, both client-to-server and server-to-client directions are defined for a user-defined WAF signature.
¡ Set a severity level.
severity-level { critical | high | low | medium } *
By default, the low severity level attribute is specified for a user-defined WAF signature.
¡ Set a logical operator between rules in the signature.
rule-logic { and | or }
By default, the logical OR operator is specified between rules in a user-defined WAF signature.
Configure rules for a user-defined WAF signature
About this task
A user-defined WAF signature rule can be one of the following types:
· Keyword.
· Integer.
A user-defined signature rule might contain filtering criteria, detection items, and a detection trigger condition. The device uses the rule for packet filtering as follows:
1. The device compares the packet with the filtering criteria.
¡ If the packet matches all filtering criteria, the device goes to the next step.
¡ If the packet does not match all filtering criteria, WAF does not process the packet.
2. The device compares the packet with the detection trigger condition.
This step is available only for a rule of the keyword type.
¡ If the packet matches the detection trigger condition, the device goes to the next step.
¡ If the packet does not match the detection trigger condition, WAF does not process the packet.
3. The device compares the packet with the detection items.
The detection items are used to match the specified contents in a packet. A packet matches a rule only when the packet matches all detection items in the rule. The match order of the detection items is their configuration order.
Restrictions and guidelines
A detection item compares its keyword with the contents in the specified protocol field.
To avoid detection errors, configure detection items based on the sequence of protocol fields in the HTTP protocol.
In a signature rule of the keyword match pattern type, a detection trigger condition must be configured before detection item configuration. If you delete the detection trigger condition, all detection items in the rule will also be deleted.
To define the start and end positions for the match operation, use either the offset and depth, or the relative offset and relative depth.
Procedure
1. Enter system view.
system-view
2. Enter the view of a user-defined WAF signature.
waf signature user-defined name signature-name
3. Create a user-defined WAF signature rule and enter its view.
rule rule-id pattern-type { integer | keyword }
By default, no user-defined WAF signature rules exist.
4. Configure the filtering criteria for the rule.
¡ Set a source IP address.
source-address ip ip-address
By default, a user-defined WAF signature rule matches all source IP addresses.
¡ Set a destination IP address.
destination-address ip ip-address
By default, a user-defined WAF signature rule matches all destination IP addresses.
¡ Set source ports.
source-port start-port [ to end-port ]
By default, a user-defined WAF signature rule matches all source ports.
¡ Set destination ports.
destination-port start-port [ to end-port ]
By default, a user-defined WAF signature rule matches all destination ports.
¡ Set an HTTP request method.
http-method method-name
By default, a user-defined WAF signature rule matches all HTTP request methods.
5. Configure the detection trigger condition and detection items for the rule.
¡ If the rule is of the keyword type, configure a detection trigger condition and detection items in sequence:
i Create a detection trigger condition.
trigger field field-name include { hex hex-string | text text-string } [ offset offset-value ] [ depth depth-value ]
ii Create a detection item.
detection-keyword detection-id field field-name match-type { exclude | include } { hex hex-string | regex regex-pattern | text text-string } [ offset offset-value [ depth depth-value ] | relative-offset relative-offset-value [ relative-depth relative-depth-value ] ]
¡ If the rule is of the integer type:
detection-integer field field-name match-type { eq | gt | gt-eq | lt | lt-eq | nequ } number
Managing the WAF signature library
You can update or roll back the version of the WAF signature library on the device.
Restrictions and guidelines
· Do not delete the /dpi/ folder in the root directory of the storage medium.
· Do not perform WAF signature update or rollback when the device's free memory is below the normal state threshold. For more information about device memory thresholds, see device management in Fundamentals Configuration Guide.
· For successful automatic and immediate signature update, make sure the device can resolve the domain name of the official website into an IP address through DNS. For more information about DNS, see DNS configuration in Layer 3—IP Services Configuration Guide.
· Update only one signature library at a time. Do not perform signature library update until the existing signature library update is completed.
Scheduling automatic WAF signature library update
About this task
You can schedule automatic WAF signature library update if the device can access the signature database services on the official website. The device periodically obtains the latest signature file from the official website to update its local signature library according to the update schedule.
Procedure
1. Enter system view.
system-view
2. Enable automatic WAF signature library update and enter automatic WAF signature library update configuration view.
waf signature auto-update
By default, automatic WAF signature library update is disabled.
3. Schedule the update time.
update schedule { daily | weekly { fri | mon | sat | sun | thu | tue | wed } } start-time time tingle minutes
By default, the device updates the WAF signature library at a random time between 01:00:00 and 03:00:00 every day.
4. (Optional.) Configure the device to overwrite the current WAF signature library without backing up the library during an automatic signature library update.
override-current
By default, the device backs up the current WAF signature library as the previous version before performing an automatic WAF signature library update.
Triggering an immediate WAF signature update
About this task
Anytime you find a release of new signature version on the official website, you can trigger the device to immediately update the local signature library.
Procedure
1. Enter system view.
system-view
2. Trigger an immediate WAF signature library update.
waf signature auto-update-now
Performing a WAF signature manual update
About this task
If the device cannot access the signature database services on the official website, use one of the following methods to manually update the WAF signature library on the device:
· Local update—Updates the WAF signature library by using a locally stored update WAF signature file.
Store the update file on the master device for successful signature library update.
· FTP/TFTP update—Updates the WAF signature library by using the file stored on the FTP or TFTP server.
Procedure
1. Enter system view.
system-view
2. Manually update the WAF signature library on the device.
waf signature update [ override-current ] file-path
Rolling back the WAF signature library
About this task
If a WAF signature library update causes exceptions or a high false alarm rate, you can roll back the WAF signature library.
Before rolling back the WAF signature library, the device backs up the current signature library as the previous version. For example, the previous library version is V1 and the current library version is V2. If you perform a rollback to the previous version, library version V1 becomes the current version and library version V2 becomes the previous version. If you perform a rollback to the previous version again, the library rolls back to library version V2.
Procedure
1. Enter system view.
system-view
2. Roll back the WAF signature library to the previous version or to the factory default version.
waf signature rollback { factory | last }
Configuring WAF whitelist
About this task
If false alarms exist in WAF logs, you can enable the WAF whitelist feature, and add the detected WAF signature IDs, URLs, or source IP addresses to the WAF whitelist. The WAF signature IDs, URLs, and source IP addresses are recorded in the WAF logs. The device permits packets matching the WAF signatures, URLs, or source IP addresses on the WAF whitelist to pass through, reducing false alarms.
If a WAF whitelist entry contains a signature ID, URL, and source IP address, or two of them, a packet matches this entry only when it matches all configured criteria.
Procedure
1. Enter system view.
system-view
2. Enable the WAF whitelist feature.
waf whitelist enable
By default, the WAF whitelist feature is enabled.
3. Create a WAF whitelist entry and enter its view.
waf whitelist entry-id
4. Configure the description for the WAF whitelist entry.
description text
By default, a WAF whitelist entry does not have any description.
5. Configure the WAF whitelist entry. Choose at least one of the following options to configure:
¡ Add a signature ID to the WAF whitelist entry.
signature-id [ serial-number ] sig-id
By default, no signature ID exists in a WAF whitelist entry.
¡ Add a source IP address to the WAF whitelist entry.
source-address { ip ipv4-address | ipv6 ipv6-address }
By default, no source IP address exists in a WAF whitelist entry.
¡ Add a URL to the WAF whitelist entry.
url match-type { accurate | substring } url-text
By default, no URL exists in a WAF whitelist entry.
6. (Optional.) Disable the WAF whitelist entry.
undo entry enable
By default, a WAF whitelist entry is enabled. To disable a WAF whitelist entry not in use, use this command.
7. Return to system view.
quit
8. (Optional.) Activate the WAF whitelist configuration.
waf whitelist activate
By default, when you create, edit, or delete a WAF whitelist entry that contains a URL, the system automatically activate the configuration 10 seconds later to have the configuration take effect. To have the configuration take effect immediately, use this command.
For the configuration on a WAF whitelist entry that does not contain a URL, the configuration automatically takes effect.
Configuring server information hiding
About this task
Some responses from the server to a client might contain server information, including the server version. To prevent attackers from obtaining server information, you can configure this feature to hide server information in these responses.
Restrictions and guidelines
Server information hiding for FTP protocol packets takes effect only for FTP responses with response code 220.
Procedure
1. Enter system view.
system-view
2. Enter WAF policy view.
waf policy policy-name
3. Configure server information hiding. Choose at least one of the following options to configure:
¡ Hide server information in FTP protocol packets.
hide-server-info ftp
By default, server information in FTP protocol packets is not hidden.
¡ Hide server information on an HTTP error code page.
hide-server-info http error-code { client-error | server-error } *
By default, server information is not hidden on an HTTP error code page.
¡ Hide server information in HTTP headers.
hide-server-info http header header-name &<1-4>
By default, server information is not hidden in HTTP headers.
Display and maintenance commands for WAF
Execute display commands in any view.
|
Task |
Command |
|
Display WAF policy information. |
display waf policy policy-name |
|
Display WAF signature library information. |
display waf signature library |
|
Display WAF signature information. |
display waf signature [ pre-defined | user-defined ] [ direction { any | to-client | to-server } ] [ category category-name | fidelity { high | low | medium } | severity { critical | high | low | medium } ] * |
|
Display detailed information about a predefined WAF signature. |
display waf signature pre-defined signature-id |
|
Display detailed information about a user-defined WAF signature. |
display waf signature user-defined signature-id |
WAF configuration examples
Example: Using the default WAF policy in a security policy
Network configuration
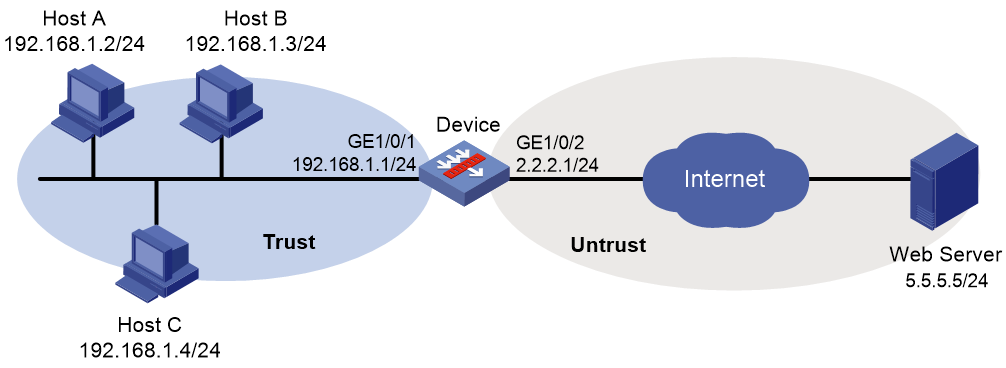
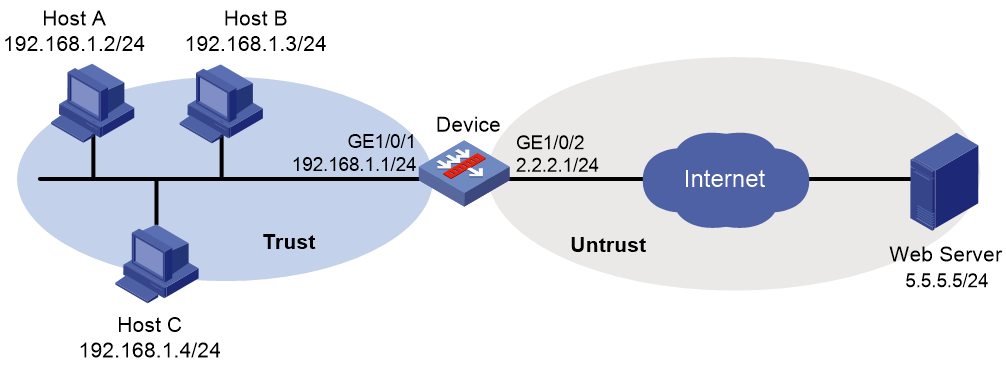
As shown in Figure 3, the device connects to the LAN and Internet through security zones Trust and Untrust, respectively.
Configure the device to use the default WAF policy for attack detection and prevention.
Procedure
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 192.168.1.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Configure settings for routing.
This example configures a static route with next hop address 2.2.2.2.
[Device] ip route-static 5.5.5.0 24 2.2.2.2
3. Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/2
[Device-security-zone-Untrust] quit
4. Apply the default WAF policy to a DPI application profile and activate the WAF policy settings:
# Create a DPI application profile named sec and enter its view. Apply the default WAF policy to the DPI application profile and set the policy mode to protect.
[Device] app-profile sec
[Device-app-profile-sec] waf apply policy default mode protect
[Device-app-profile-sec] quit
# Activate the WAF policy settings.
[Device] inspect activate
5. Configure a security policy:
# Enter IPv4 security policy view. Create a security policy rule named trust-untrust so the device can apply the WAF policy to traffic between the internal users and the Internet.
[Device] security-policy ip
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-10-trust-untrust] source-zone trust
[Device-security-policy-ip-10-trust-untrust] source-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-10-trust-untrust] destination-zone untrust
[Device-security-policy-ip-10-trust-untrust] action pass
[Device-security-policy-ip-10-trust-untrust] profile sec
[Device-security-policy-ip-10-trust-untrust] quit
# Activate rule matching acceleration.
[Device-security-policy-ip] accelerate enhance enable
[Device-security-policy-ip] quit
Verifying the configuration
# Verify that the device can use the default WAF policy to detect and prevent known network attacks. (Details not shown.)
For example, if an incoming attack packet matches predefined WAF signature GNU_Bash_Remote_Code_Execution_Vulnerability(CVE-2014-6271), the device automatically applies the signature actions (reset and logging) to the packet.
Example: Using a user-defined WAF policy in a security policy
Network configuration
As shown in Figure 4, the device connects to the LAN and Internet through security zones Trust and Untrust, respectively.
Perform the following tasks:
1. Configure the device to use a WAF policy for attack detection and prevention.
2. Enable predefined WAF signature 2 and specify actions drop and logging for the signature.
Procedure
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 192.168.1.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Configure settings for routing.
This example configures a static route with next hop address 2.2.2.2.
[Device] ip route-static 5.5.5.0 24 2.2.2.2
3. Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/2
[Device-security-zone-Untrust] quit
4. Create a WAF policy named waf1, and then configure the following settings in the policy:
a. Configure the server to client direction as signature filtering criterion.
b. Enable predefined WAF signature 2 and specify actions drop and logging for the signature.
[Device] waf policy waf1
[Device-waf-policy-waf1] object-dir client
[Device-waf-policy-waf1] signature override pre-defined 2 enable drop logging
[Device-waf-policy-waf1] quit
5. Apply WAF policy waf1 to a DPI application profile and activate the WAF policy settings:
# Create a DPI application profile named sec. Apply WAF policy waf1 to the DPI application profile and set the policy mode to protect.
[Device] app-profile sec
[Device-app-profile-sec] waf apply policy waf1 mode protect
[Device-app-profile-sec] quit
# Activate the WAF policy settings.
[Device] inspect activate
6. Configure a security policy:
# Enter IPv4 security policy view. Create a security policy rule named trust-untrust so the device can apply the WAF policy to traffic between the internal users and the Internet.
[Device] security-policy ip
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-10-trust-untrust] source-zone trust
[Device-security-policy-ip-10-trust-untrust] source-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-10-trust-untrust] destination-zone untrust
[Device-security-policy-ip-10-trust-untrust] action pass
[Device-security-policy-ip-10-trust-untrust] profile sec
[Device-security-policy-ip-10-trust-untrust] quit
# Activate rule matching acceleration.
[Device-security-policy-ip] accelerate enhanced enable
[Device-security-policy-ip] quit
Verifying the configuration
# Verify that the device can use the default WAF policy to detect and prevent known network attacks. (Details not shown.)
# Verify that when a packet matches predefined WAF signature 2, the device executes the drop and logging actions.
Example: Manually updating the WAF signature library
Network configuration
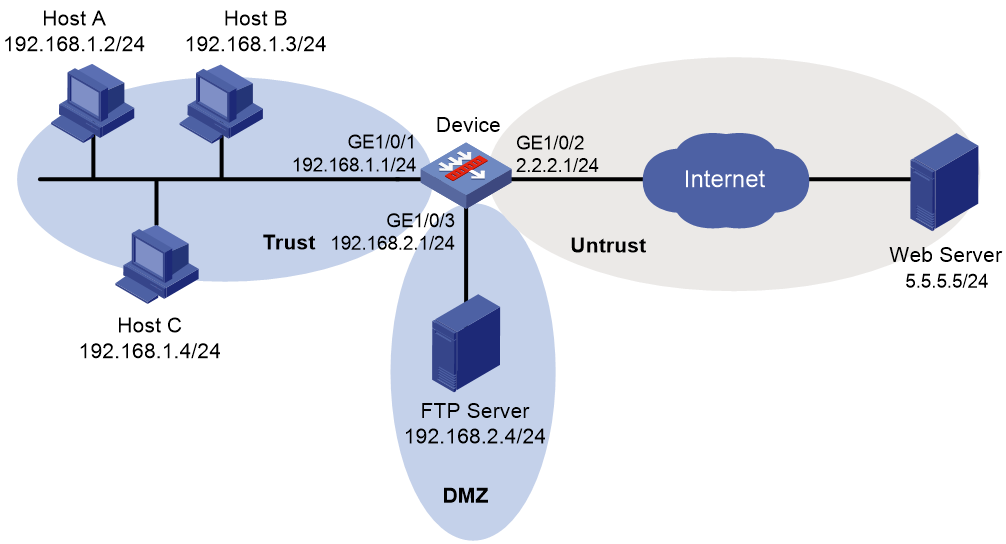
As shown in Figure 5, LAN users in security zone Trust can access the following resources:
· Internet resources in security zone Untrust.
· The FTP server at 192.168.2.4/24 in security zone DMZ. The FTP login username and password are waf and 123, respectively.
Manually update the WAF signature library by using the latest WAF signature file stored on the FTP server.
Procedure
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 192.168.1.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Configure settings for routing.
This example configures a static route with next hop address 2.2.2.2.
[Device] ip route-static 5.5.5.0 24 2.2.2.2
3. Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/2
[Device-security-zone-Untrust] quit
[Device] security-zone name dmz
[Device-security-zone-DMZ] import interface gigabitethernet 1/0/3
[Device-security-zone-DMZ] quit
4. Configure a security policy:
# Configure a security policy rule to permit the traffic between the Trust and Untrust security zones so internal users can access external resources.
[Device] security-policy ip
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-10-trust-untrust] source-zone trust
[Device-security-policy-ip-10-trust-untrust] source-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-10-trust-untrust] destination-zone untrust
[Device-security-policy-ip-10-trust-untrust] action pass
[Device-security-policy-ip-10-trust-untrust] quit
# Configure a security policy rule to permit the traffic between the Trust and DMZ security zones so internal users can access the FTP server in the DMZ security zone.
[Device] security-policy ip
[Device-security-policy-ip] rule name trust-dmz
[Device-security-policy-ip-11-trust-dmz] source-zone trust
[Device-security-policy-ip-11-trust-dmz] source-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-11-trust-dmz] destination-zone dmz
[Device-security-policy-ip-11-trust-dmz] action pass
[Device-security-policy-ip-11-trust-dmz] quit
# Configure a security policy rule to permit the traffic between the FTP server and the device so the device can access the FTP server to obtain the signature library file.
[Device] security-policy ip
[Device-security-policy-ip] rule name downloadlocalout
[Device-security-policy-ip-12-downloadlocalout] source-zone local
[Device-security-policy-ip-12-downloadlocalout] destination-zone dmz
[Device-security-policy-ip-12-downloadlocalout] destination-ip-subnet 192.168.2.0 24
[Device-security-policy-ip-12-downloadlocalout] application ftp
[Device-security-policy-ip-12-downloadlocalout] application ftp-data
[Device-security-policy-ip-12-downloadlocalout] action pass
[Device-security-policy-ip-12-downloadlocalout] quit
# Activate rule matching acceleration.
[Device-security-policy-ip] accelerate enhanced enable
[Device-security-policy-ip] quit
5. Update the WAF signature library on the device by using WAF signature file waf-1.0.8-encrypt.dat on the FTP server.
[Device] waf signature update ftp://waf:[email protected]/waf-1.0.8-encrypt.dat
Verifying the configuration
# Verify that the device WAF signature library is updated.
<Device> display waf signature library
Example: Configuring automatic WAF signature library update
Network configuration
As shown in Figure 6, LAN users in security zone Trust can access Internet resources in security zone Untrust.
Configure the device to start automatically updating the local WAF signature library at a random time between 08:30 a.m. and 09:30 a.m. every Saturday.
Procedure
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 192.168.1.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Configure settings for routing.
This example configures a static route with next hop address 2.2.2.2.
[Device] ip route-static 5.5.5.0 24 2.2.2.2
3. Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/2
[Device-security-zone-Untrust] quit
4. Configure DNS for the device to resolve the domain name of the official website into the correct IP address.
[Device] dns server 10.72.66.36
5. Configure a security policy:
# Configure a security policy rule to permit the traffic between the Trust and Untrust security zones so internal users can access external resources.
[Device] security-policy ip
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-10-trust-untrust] source-zone trust
[Device-security-policy-ip-10-trust-untrust] source-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-10-trust-untrust] destination-zone untrust
[Device-security-policy-ip-10-trust-untrust] action pass
[Device-security-policy-ip-10-trust-untrust] quit
# Configure a security policy rule to permit the traffic between the Local and Untrust security zones so the device can access the official website to obtain the signature library file.
[Device] security-policy ip
[Device-security-policy-ip] rule name downloadlocalout
[Device-security-policy-ip-11-downloadlocalout] source-zone local
[Device-security-policy-ip-11-downloadlocalout] destination-zone untrust
[Device-security-policy-ip-11-downloadlocalout] action pass
[Device-security-policy-ip-11-downloadlocalout] quit
# Activate rule matching acceleration.
[Device-security-policy-ip] accelerate enhanced enable
[Device-security-policy-ip] quit
6. Configure automatic WAF signature library update:
Enable automatic WAF signature library update. Configure the device to perform automatic update at a random time between 08:30 a.m. and 09:30 a.m. every Saturday.
<Device> system-view
[Device] waf signature auto-update
[Device-waf-autoupdate]
[Device-waf-autoupdate] update schedule weekly sat start-time 9:00:00 tingle 60
[Device-waf-autoupdate] quit
Verifying the configuration
# Verify that the device WAF signature library is updated as scheduled.
<Device> display waf signature library