- Table of Contents
-
- 06-ACL and QoS Configuration Examples
- 01-ACL Configuration Examples
- 02-Traffic Filtering Configuration Examples
- 03-Traffic Policing Configuration Examples
- 04-GTS and Rate Limiting Configuration Examples
- 05-Congestion Avoidance and Queue Scheduling Configuration Examples
- 06-Priority Mapping and Queue Scheduling Configuration Examples
- 07-Priority Marking and Queue Scheduling Configuration Examples
- 08-Control Plane-Based QoS Policy Configuration Examples
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-ACL Configuration Examples | 124.71 KB |
Example: Filtering packets by MAC address
Applicable hardware and software versions
Example: Controlling FTP access
Applicable hardware and software versions
Example: Filtering packets by IP address
Applicable hardware and software versions
Denying the Administration department to access the R&D department
Configuring access control for the R&D department
Example: Filtering HTTP packets by using a user-defined ACL
Applicable hardware and software versions
Introduction
This document provides ACL configuration examples.
Prerequisites
This document is not restricted to specific software or hardware versions.
The configuration examples in this document were created and verified in a lab environment, and all the devices were started with the factory default configuration. When you are working on a live network, make sure you understand the potential impact of every command on your network.
This document assumes that you have basic knowledge of ACL.
Example: Filtering packets by MAC address
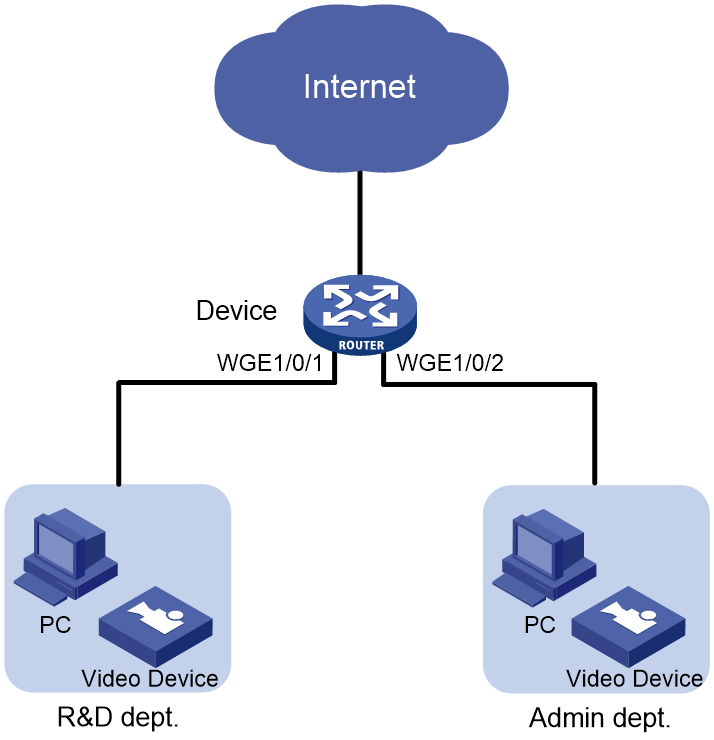
Network configuration
As shown in Figure 1, the R&D department and the Administration department have video devices deployed. The video devices use MAC addresses prefixed with 000f-e2. Configure packet filtering on the device to allow outgoing video data to pass through only from 8:30 to 18:00 every day.
Analysis
Because the MAC addresses of the video devices are fixed, you can use an Ethernet frame header ACL to filter packets by MAC address. In the ACL, specify a MAC address and a mask to match the MAC addresses that have the same prefix.
Applicable hardware and software versions
The following matrix shows the hardware and software versions to which this configuration example is applicable:
|
Hardware |
Software version |
|
S6550X-HI switch series |
Release 1116 and later |
|
S6880 switch series |
Release 1116 and later |
|
S9820-8M switch |
Release 1116 and later |
|
S9855 switch series |
Release 9126 and later |
|
S9825 switch series |
Release 9126 and later |
Procedures
# Create a time range time1 for the time range from 8:30 to 18:00 every day.
<Device> system-view
[Device] time-range time1 8:30 to 18:00 daily
# Configure Ethernet frame header ACL 4000 to allow packets with source MAC addresses prefixed with 000f-e2 to pass through only during time1.
[Device] acl mac 4000
[Device-acl-mac-4000] rule permit source-mac 000f-e200-0000 ffff-ff00-0000 time-range time1
[Device-acl-mac-4000] rule deny source-mac 000f-e200-0000 ffff-ff00-0000
[Device-acl-mac-4000] quit
# Apply ACL 4000 to filter incoming packets on Twenty-FiveGigE 1/0/1 and Twenty-FiveGigE 1/0/2.
[Device] interface twenty-fivegige 1/0/1
[Device-Twenty-FiveGigE1/0/1] packet-filter mac 4000 inbound
[Device-Twenty-FiveGigE1/0/1] quit
[Device] interface twenty-fivegige 1/0/2
[Device-Twenty-FiveGigE1/0/2] packet-filter mac 4000 inbound
[Device-Twenty-FiveGigE1/0/2] quit
Verifying the configuration
# Verify that the ACL is successfully applied for packet filtering.
[Device] display packet-filter interface inbound
Interface: Twenty-FiveGigE1/0/1
Inbound policy:
MAC ACL 4000
Interface: Twenty-FiveGigE1/0/2
Inbound policy:
MAC ACL 4000
# Verify that the video devices can communicate with the external network during the time range time1. (Details not shown.)
# Verify that the video devices cannot communicate with the external network beyond the time range time1. (Details not shown.)
Configuration files
#
interface Twenty-FiveGigE1/0/1
port link-mode bridge
packet-filter mac 4000 inbound
#
interface Twenty-FiveGigE1/0/2
port link-mode bridge
packet-filter mac 4000 inbound
#
time-range time1 08:30 to 18:00 daily
#
acl mac 4000
rule 0 permit source-mac 000f-e200-0000 ffff-ff00-0000 time-range time1
rule 5 deny source-mac 000f-e200-0000 ffff-ff00-0000
Example: Controlling FTP access
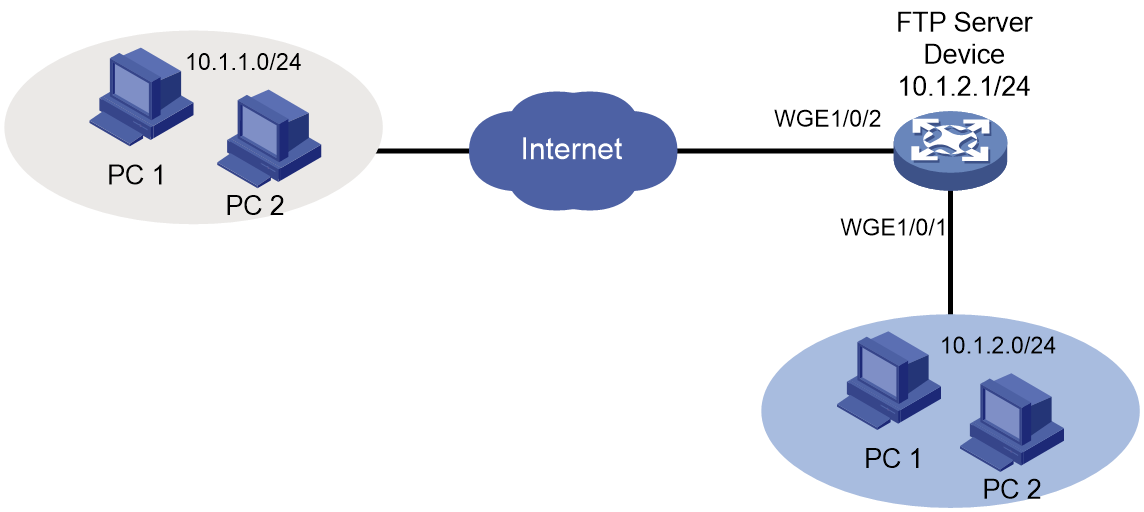
Network configuration
As shown in Figure 2, the device is an FTP server. Configure FTP access control on the device to meet the following requirements:
· Users on subnet 10.1.2.0/24 can access the FTP server at any time.
· Users on subnet 10.1.1.0/24 can access the FTP server during working hours (8:30 to 18:00) on working days (Monday to Friday).
· Qualified users are assigned the level-15 user role.
Analysis
To meet the network requirements, you must perform the following tasks:
· Configure two rules for the ACL. One rule permits packets from subnet 10.1.2.0/24. The other one permits packets from subnet 10.1.1.0/24 and takes effect only during working hours on working days.
· Use the ACL to control access to the FTP server.
Applicable hardware and software versions
The following matrix shows the hardware and software versions to which this configuration example is applicable:
|
Hardware |
Software version |
|
S6550X-HI switch series |
Release 1116 and later |
|
S6880 switch series |
Release 1116 and later |
|
S9820-8M switch |
Release 1116 and later |
|
S9855 switch series |
Release 9126 and later |
|
S9825 switch series |
Release 9126 and later |
Procedures
# Configure the time range ftp for working hours 8:30 to 18:00 from Monday to Friday.
<Device> system-view
[Device] time-range ftp 8:30 to 18:00 working-day
# Create IPv4 basic ACL 2000.
[Device] acl basic 2000
# Configure a rule to permit packets from subnet 10.1.2.0/24.
[Device-acl-ipv4-basic-2000] rule permit source 10.1.2.0 0.0.0.255
# Configure a rule to permit packets from subnet 10.1.1.0/24 during the time range ftp.
[Device-acl-ipv4-basic-2000] rule permit source 10.1.1.0 0.0.0.255 time-range ftp
[Device-acl-ipv4-basic-2000] quit
# Enable FTP server on the device.
[Device] ftp server enable
# Add a local user named ftp and authorize this user to use the FTP service.
[Device] local-user ftp
[Device-luser-manage-ftp] service-type ftp
# Configure a password for the local user.
[Device-luser-manage-ftp] password simple 1234567890H
# Assign the level-15 user role to the local user.
[Device-luser-manage-ftp] authorization-attribute user-role level-15
[Device-luser-manage-ftp] quit
# Use the ACL 2000 to control access to the FTP server.
[Device] ftp server acl 2000
Verifying the configuration
# Verify that you can use the host at 10.1.2.100 to log in to the FTP server during working hours on wording days.
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\>ftp 10.1.2.1
Connected to 10.1.2.1.
220 FTP service ready.
User (10.1.2.1:(none)): ftp
331 Password required for ftp.
Password:
230 User logged in.
# Verify that you can use the host at 10.1.1.100 to log in to the FTP server during working hours on working days.
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\>ftp 10.1.2.1
Connected to 10.1.2.1.
220 FTP service ready.
User (10.1.2.1:(none)): ftp
331 Password required for ftp.
Password:
230 User logged in.
# Verify that you can use the host at 10.1.2.100 to log in to the FTP server outside working hours.
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\>ftp 10.1.2.1
Connected to 10.1.2.1.
220 FTP service ready.
User (10.1.2.1:(none)): ftp
331 Password required for ftp.
Password:
230 User logged in.
# Verify that you cannot use the host at 10.1.1.100 to log in to the FTP server outside working hours.
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\>ftp 10.1.2.1
ftp>
ftp> ls
Not connected.
Configuration files
#
time-range ftp 08:30 to 18:00 working-day
#
acl basic 2000
rule 0 permit source 10.1.2.0 0.0.0.255
rule 5 permit source 10.1.1.0 0.0.0.255 time-range ftp
#
local-user ftp class manage
password hash $h$6$HVOQzdJMVPtVd0A7$hFeYeT1ic7AgOPJ/z/Ci9db347bnJ2krcnzA+lD++iG
0jC5qSybNhuH7zi70tH4d42Y3mYtsqNaBGsN0f0ilvA==
service-type ftp
authorization-attribute user-role level-15
authorization-attribute user-role network-operator
#
ftp server enable
ftp server acl 2000
Example: Filtering packets by IP address
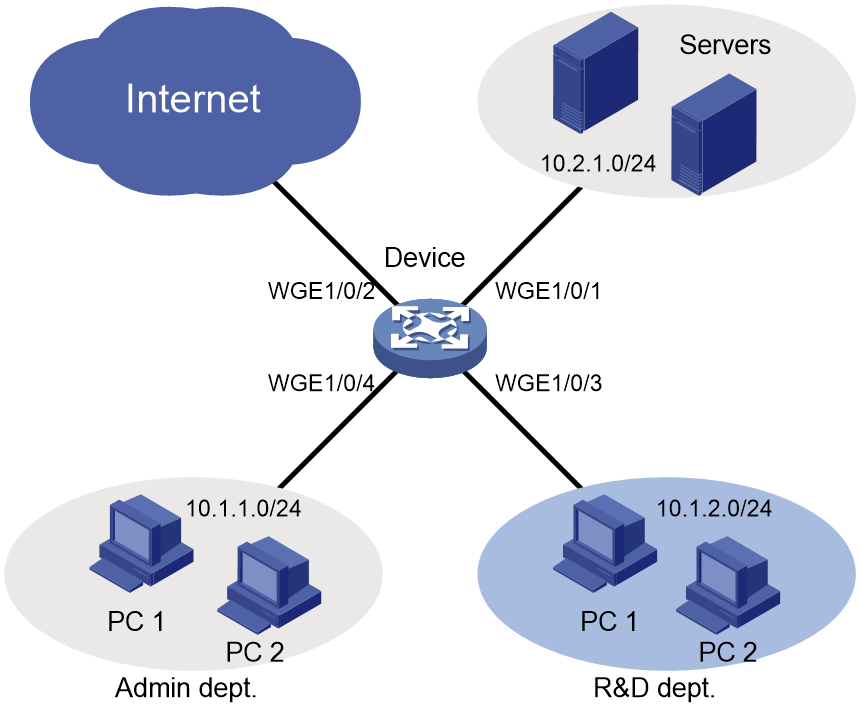
Network configuration
As shown in Figure 3, a company's internal network connects to the Internet through the device. The R&D department, Administration department, and servers are on different subnets.
Configure packet filtering to meet the following requirements:
· The Administration department can access the Internet and servers at any time, but cannot access the R&D department at any time.
· The R&D department can access only the servers during working hours (8:30 to 18:00) on working days (Monday to Friday). It can access the Internet and servers, but cannot access the Administration department outside working hours.
Analysis
To meet the network requirements, you must perform the following tasks:
· To deny the Administration department to access the R&D department, perform the following tasks:
¡ Configure an advanced ACL to deny packets destined for subnet 10.1.2.0/24.
¡ Apply the ACL to filter incoming packets on Twenty-FiveGigE 1/0/4.
· To implement access control for the R&D department, perform the following tasks:
¡ Create a time range for the working hours (8:30 to 18:00) on working days (Monday to Friday).
¡ Create an advanced ACL and configure the following rules:
- Configure rules to allow only packets destined for subnet 10.2.1.0/24 to pass through. Set the rules to be active during the time range.
- To deny the R&D department to access the Administration department, configure a rule to deny packets destined for subnet 10.1.1.0/24.
¡ Apply the ACL to filter incoming packets on Twenty-FiveGigE 1/0/3.
Applicable hardware and software versions
The following matrix shows the hardware and software versions to which this configuration example is applicable:
|
Hardware |
Software version |
|
S6550X-HI switch series |
Release 1116 and later |
|
S6880 switch series |
Release 1116 and later |
|
S9820-8M switch |
Release 1116 and later |
|
S9855 switch series |
Release 9126 and later |
|
S9825 switch series |
Release 9126 and later |
Restrictions and guidelines
When you configure ACL rules to allow the R&D department to access only the servers during working hours on working days, configure the permit rule before the deny rule. Otherwise, the interface denies all packets during working hours on working days.
Procedures
Denying the Administration department to access the R&D department
# Create IPv4 advanced ACL 3000.
<Device> system-view
[Device] acl advanced 3000
# Configure a rule to deny packets destined for subnet 10.1.2.0/24 to pass through.
[Device-acl-ipv4-adv-3000] rule deny ip destination 10.1.2.0 0.0.0.255
[Device-acl-ipv4-adv-3000] quit
# Apply ACL 3000 to filter incoming packets on Twenty-FiveGigE 1/0/4.
[Device] interface twenty-fivegige 1/0/4
[Device-Twenty-FiveGigE1/0/4] packet-filter 3000 inbound
[Device-Twenty-FiveGigE1/0/4] quit
Configuring access control for the R&D department
# Configure a time range worktime for the time range of 8:30 to 18:00 from Monday to Friday.
[Device] time-range worktime 8:30 to 18:00 working-day
# Create IPv4 advanced ACL 3001.
[Device] acl advanced 3001
# Configure a rule to allow packets destined for subnet 10.2.1.0/24 to pass through during worktime.
[Device-acl-ipv4-adv-3001] rule permit ip destination 10.2.1.0 0.0.0.255 time-range worktime
# Configure a rule to deny all IP packets to pass through during worktime.
[Device-acl-ipv4-adv-3001] rule deny ip time-range worktime
# Configure a rule to deny packets destined for subnet 10.1.1.0/24 to pass through.
[Device-acl-ipv4-adv-3001] rule deny ip destination 10.1.1.0 0.0.0.255
[Device-acl-ipv4-adv-3001] quit
# Apply ACL 3001 to filter incoming packets on Twenty-FiveGigE 1/0/3.
[Device] interface twenty-fivegige 1/0/3
[Device-Twenty-FiveGigE1/0/3] packet-filter 3001 inbound
[Device-Twenty-FiveGigE1/0/3] quit
Verifying the configuration
# Verify that the ACLs are successfully applied for packet filtering.
[Device] display packet-filter interface inbound
Interface: Twenty-FiveGigE1/0/3
Inbound policy:
IPv4 ACL 3001
Interface: Twenty-FiveGigE1/0/4
Inbound policy:
IPv4 ACL 3000
# Verify that you cannot ping through a website on the Internet from the R&D department at 9:30 on Monday.
C:\>ping www.google.com
Pinging www.google.com [173.194.127.242] with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 173.194.127.242:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),
C:\>
# Verify that you can ping through a website on the Internet from the Administration department at 9:30 on Monday.
C:\>ping www.google.com
Pinging www.google.com [173.194.127.242] with 32 bytes of data:
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Ping statistics for 173.194.127.242:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 30ms, Maximum = 30ms, Average = 30ms
C:\>
# Verify that you can ping through a website on the Internet from the R&D department at 19:30 on Monday.
C:\>ping www.google.com
Pinging www.google.com [173.194.127.242] with 32 bytes of data:
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Reply from 173.194.127.242: bytes=32 time=30ms TTL=50
Ping statistics for 173.194.127.242:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 30ms, Maximum = 30ms, Average = 30ms
C:\>
Configuration files
#
interface Twenty-FiveGigE1/0/3
port link-mode bridge
packet-filter 3001 inbound
#
interface Twenty-FiveGigE1/0/4
port link-mode bridge
packet-filter 3000 inbound
#
time-range worktime 08:30 to 18:00 working-day
#
acl advanced 3000
rule 0 deny ip destination 10.1.2.0 0.0.0.255
#
acl advanced 3001
rule 0 permit ip destination 10.2.1.0 0.0.0.255 time-range worktime
rule 5 deny ip time-range worktime
rule 10 deny ip destination 10.1.1.0 0.0.0.255
Example: Filtering HTTP packets by using a user-defined ACL
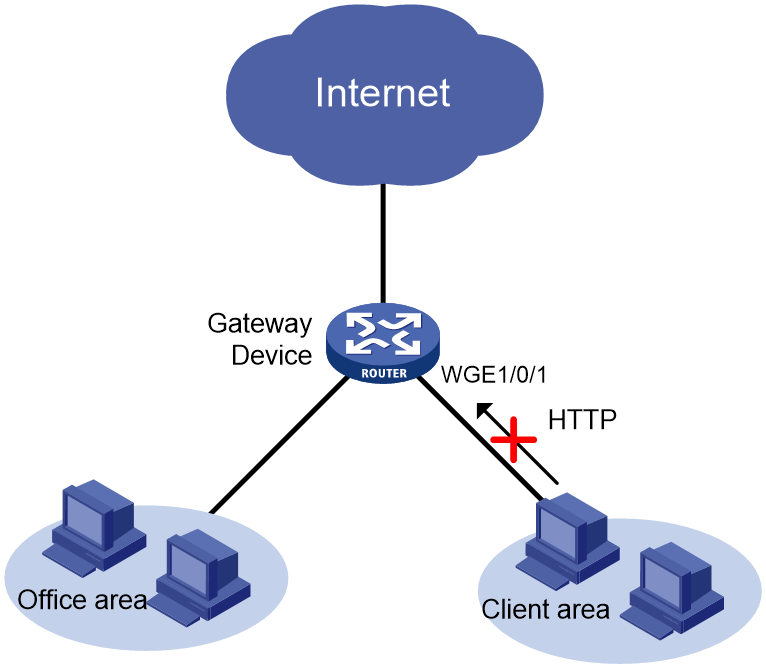
Network configuration
As shown in Figure 4, configure packet filtering on the device to deny all HTTP packets from the client area.
Applicable hardware and software versions
The following matrix shows the hardware and software versions to which this configuration example is applicable:
|
Hardware |
Software version |
|
S6550X-HI switch series |
Not supported |
|
S6880 switch series |
Not supported |
|
S9820-8M switch |
Release 1116 and later |
|
S9855 switch series |
Release 9126 and later |
|
S9825 switch series |
Release 9126 and later |
Procedures
# Create user-defined ACL 5000.
<Device> system-view
[Device] acl user-defined 5000
# Configure a rule to deny HTTP packets to pass through.
[Device-acl-user-5000] rule deny l4 1f90 ffff 0
[Device-acl-user-5000] quit
# Apply ACL 5000 to filter incoming HTTP packets on Twenty-FiveGigE 1/0/1.
[Device] interface twenty-fivegige 1/0/1
[Device-Twenty-FiveGigE1/0/1] packet-filter user-defined 5000 inbound
[Device-Twenty-FiveGigE1/0/1] quit
Verifying the configuration
# Verify that the ACL is successfully applied for packet filtering.
[Device] display packet-filter interface inbound
Interface: Twenty-FiveGigE1/0/1
Inbound policy:
User-defined ACL 5000
Configuration files
#
interface Twenty-FiveGigE1/0/1
port link-mode bridge
packet-filter user-defined 5000 inbound
#
acl user-defined 5000
rule 0 deny l4 1f90 ffff 0