- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-IRF configuration | 675.67 KB |
Contents
File system naming conventions
Multi-active handling procedure
Restrictions: Hardware compatibility with IRF
Restrictions and guidelines: IRF configuration
Hardware compatibility with IRF
Candidate IRF physical interfaces
Transceiver modules and cables selection for IRF
IRF physical interface configuration restrictions and guidelines
Feature compatibility and configuration restrictions with IRF
Licensing requirements for IRF
Configuration rollback restrictions
Assigning a member ID to each IRF member device
Specifying a priority for each member device
Binding physical interfaces to IRF ports
Bulk-configuring basic IRF settings for a member device
Connecting IRF physical interfaces
Restrictions and guidelines for MAD configuration
Excluding interfaces from the shutdown action upon detection of multi-active collision
Optimizing IRF settings for an IRF fabric
Configuring a member device description
Configuring IRF link load sharing mode
Configuring the IRF bridge MAC address
Enabling software auto-update for software image synchronization
Removing an expansion interface card that has IRF physical interfaces
Replacing an expansion interface card that has IRF physical interfaces
Display and maintenance commands for IRF
Example: Configuring an LACP MAD-enabled IRF fabric
Configuring a BFD MAD-enabled IRF fabric
Configuring an ARP MAD-enabled IRF fabric
Configuring an ND MAD-enabled IRF fabric
IRF hot backup configuration examples
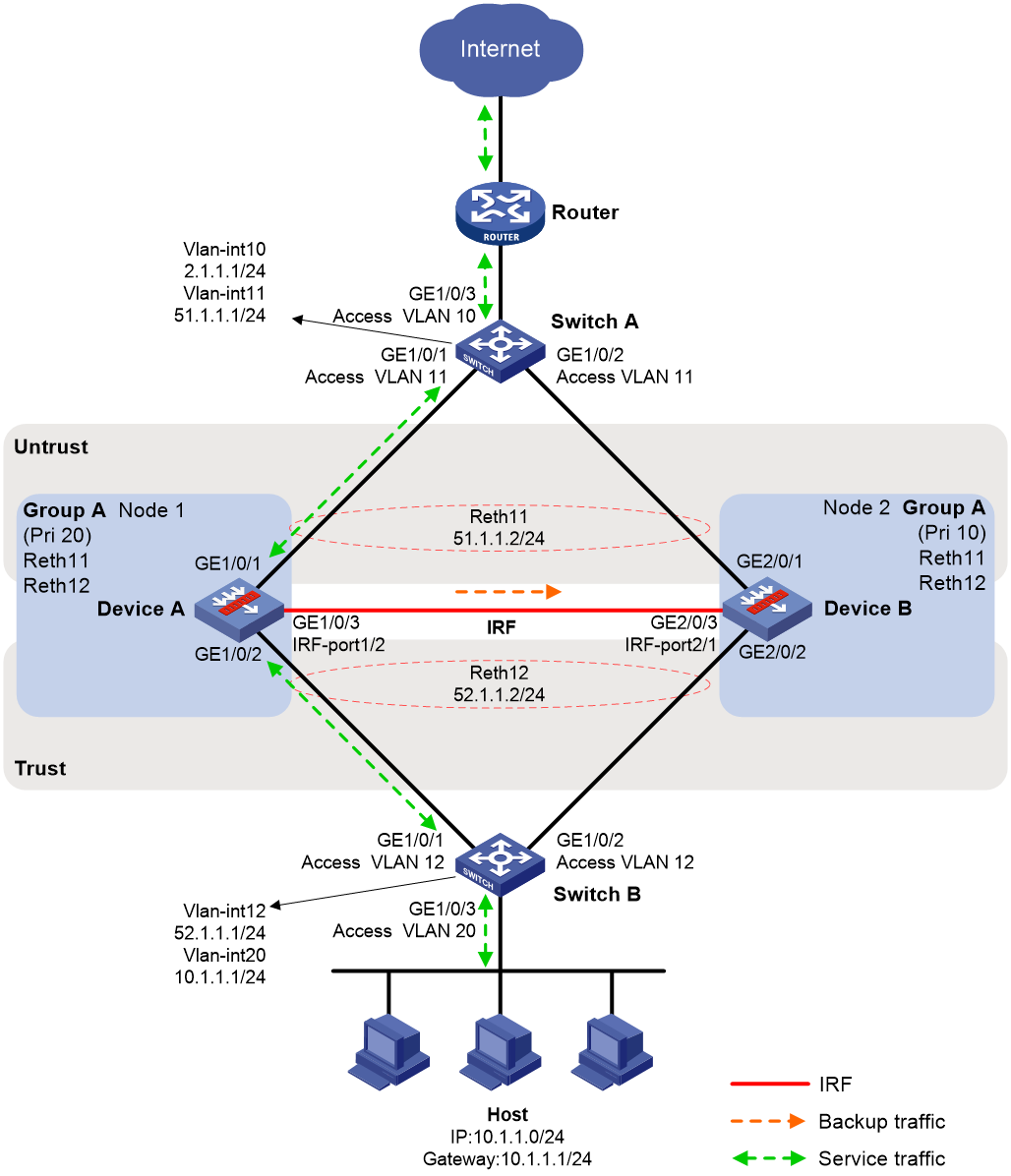
Example: Configuring an IRF hot backup system in active/standby mode with one redundancy group
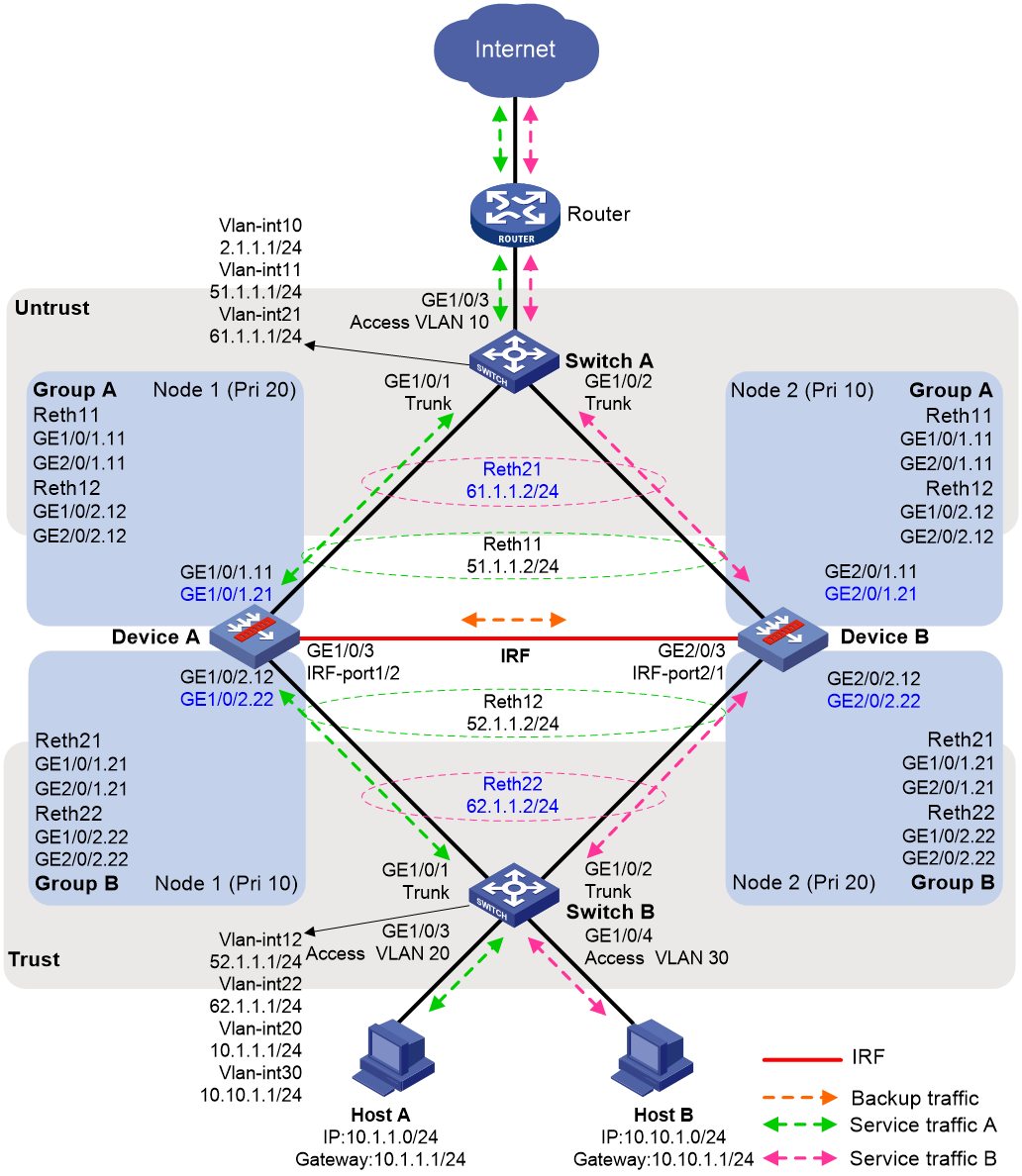
Example: Configuring an IRF hot backup system in dual-active mode with two redundancy groups
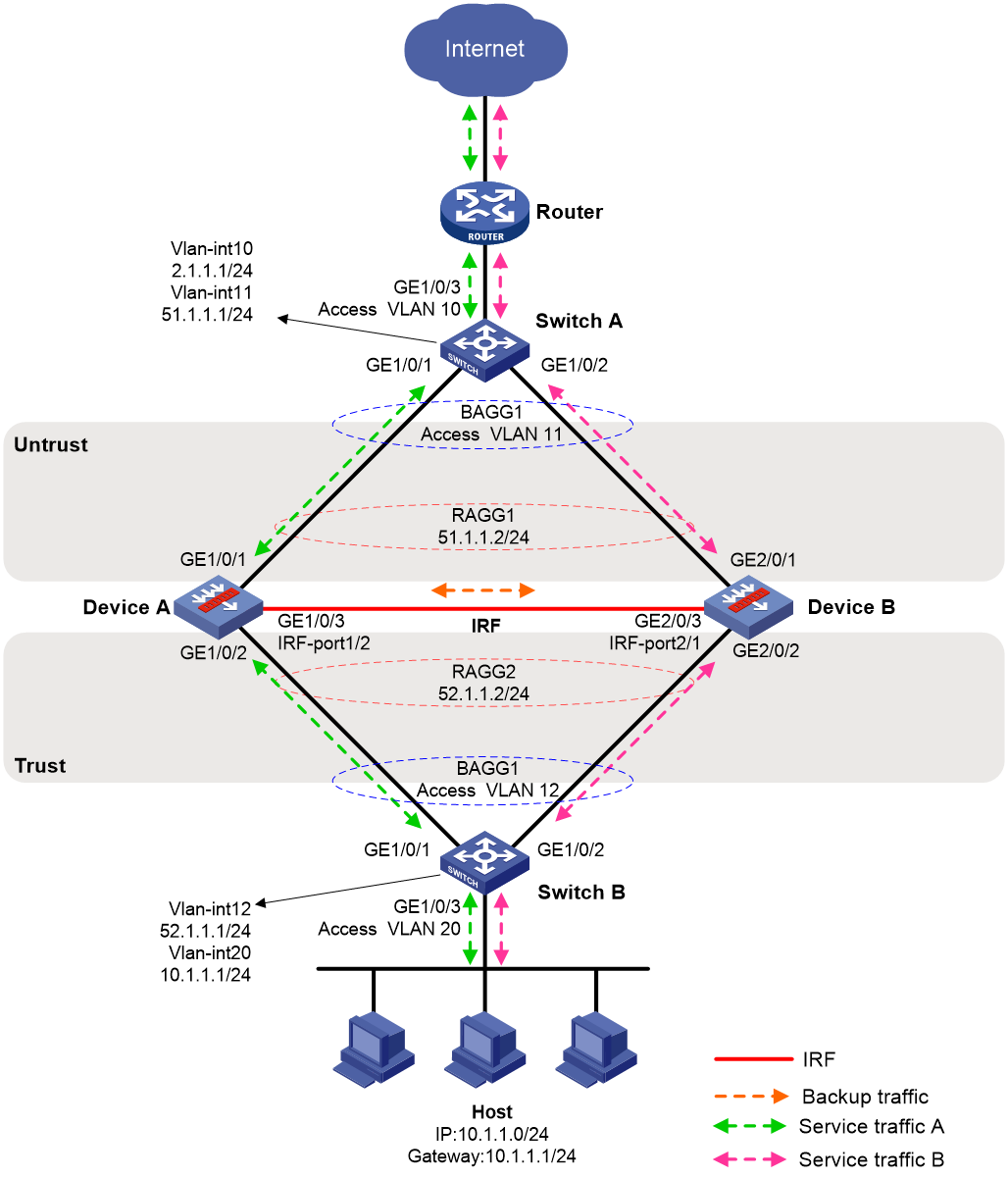
Example: Configuring an IRF hot backup system in dual-active mode with link aggregations
Configuring an IRF fabric
About IRF
The Intelligent Resilient Framework (IRF) technology virtualizes multiple physical devices at the same layer into one virtual fabric to provide data center class availability and scalability. IRF virtualization technology offers processing power, interaction, unified management, and uninterrupted maintenance of multiple devices.
IRF network model
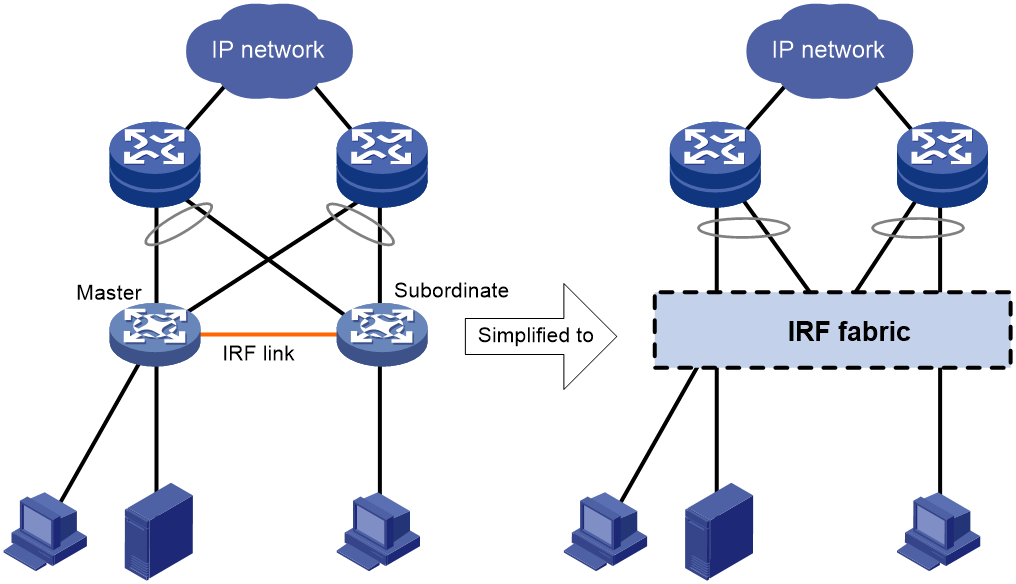
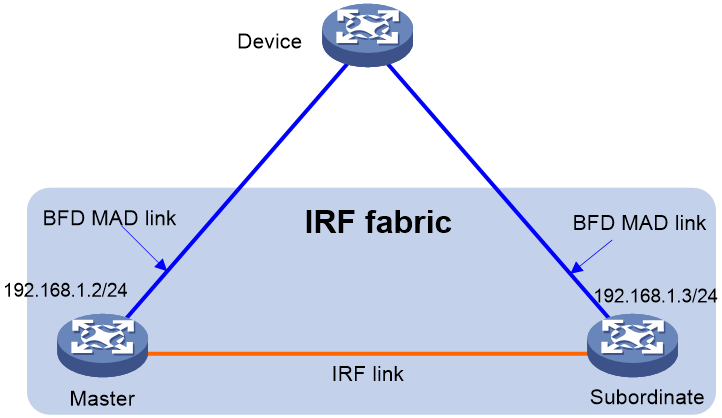
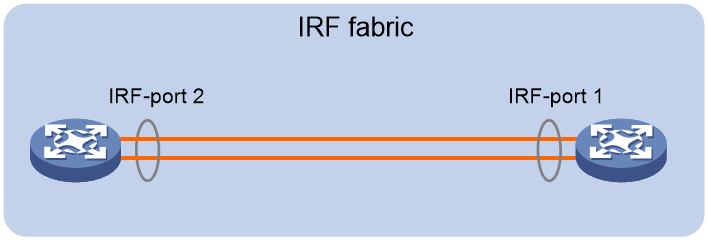
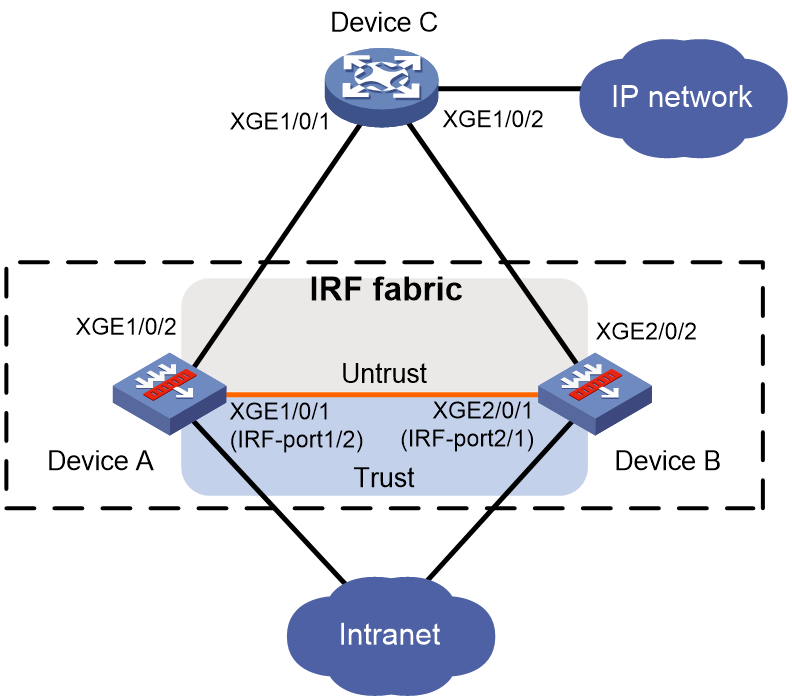
Figure 1 shows an IRF fabric that has two devices, which appear as a single node to the upper-layer and lower-layer devices.
Figure 1 IRF application scenario
IRF benefits
IRF provides the following benefits:
· Simplified topology and easy management—An IRF fabric appears as one node and is accessible at a single IP address on the network. You can use this IP address to log in at any member device to manage all the members of the IRF fabric. In addition, you do not need to run the spanning tree feature among the IRF members.
· 1:N redundancy—In an IRF fabric, one member acts as the master to manage and control the entire IRF fabric. All the other members process services while backing up the master. When the master fails, all the other member devices elect a new master from among them to take over without interrupting services.
· IRF link aggregation—You can assign several physical links between neighboring members to their IRF ports to create a load-balanced aggregate IRF connection with redundancy.
· Multichassis link aggregation—You can use the Ethernet link aggregation feature to aggregate the physical links between the IRF fabric and its upstream or downstream devices across the IRF members.
· Network scalability and resiliency—Processing capacity of an IRF fabric equals the total processing capacities of all the members. You can increase ports, network bandwidth, and processing capacity of an IRF fabric simply by adding member devices without changing the network topology.
Basic concepts
IRF member roles
IRF uses two member roles: master and standby (called subordinate throughout the documentation).
When devices form an IRF fabric, they elect a master to manage and control the IRF fabric, and all the other devices back up the master. When the master device fails, the other devices automatically elect a new master. For more information about master election, see "Master election."
IRF member ID
An IRF fabric uses member IDs to uniquely identify and manage its members. This member ID information is included as the first part of interface numbers and file paths to uniquely identify interfaces and files in an IRF fabric. Two devices cannot form an IRF fabric if they use the same member ID. A device cannot join an IRF fabric if its member ID has been used in the fabric.
Member priority
Member priority determines the possibility of a member device to be elected the master. A member with higher priority is more likely to be elected the master.
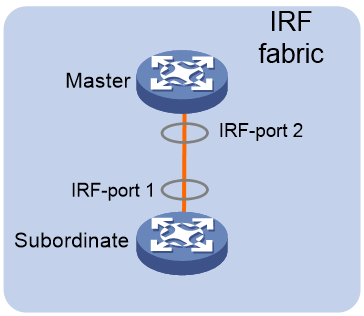
IRF port
An IRF port is a logical interface that connects IRF member devices. Every IRF-capable device has two IRF ports.
The IRF ports are named IRF-port n/1 and IRF-port n/2, where n is the member ID of the device. The two IRF ports are referred to as IRF-port 1 and IRF-port 2.
To use an IRF port, you must bind a minimum of one physical interface to it. The physical interfaces assigned to an IRF port automatically form an aggregate IRF link. An IRF port goes down when all its IRF physical interfaces are down.
IRF physical interface
IRF physical interfaces connect IRF member devices and must be bound to an IRF port. They forward traffic between member devices, including IRF protocol packets and data packets that must travel across IRF member devices.
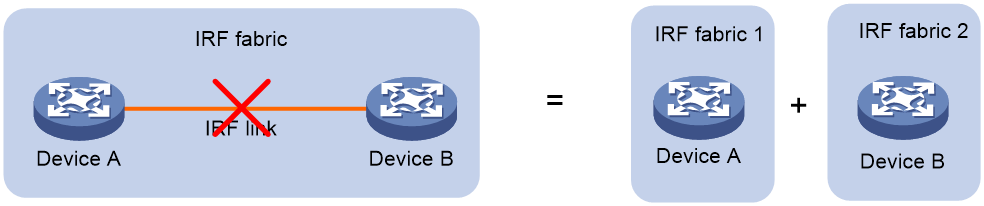
IRF split
IRF split occurs when an IRF fabric breaks up into multiple IRF fabrics because of IRF link failures, as shown in Figure 2. The split IRF fabrics operate with the same IP address. IRF split causes routing and forwarding problems on the network. To quickly detect a multi-active collision, configure a minimum of one MAD mechanism (see "Configuring MAD").
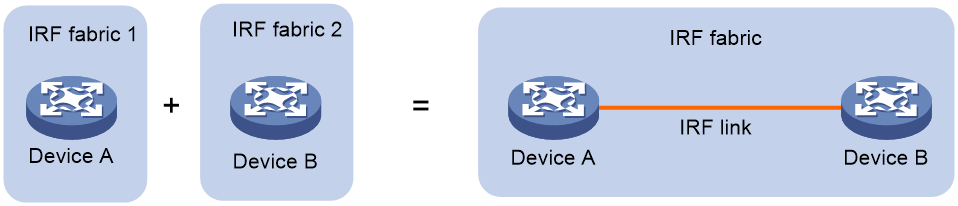
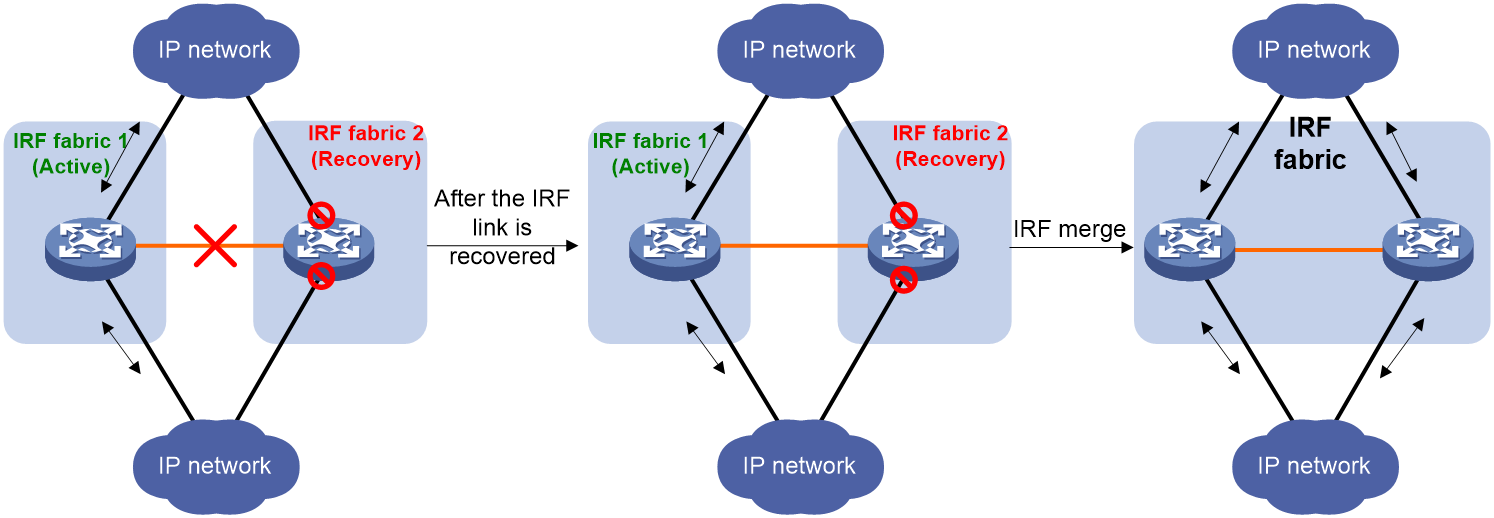
IRF merge
IRF merge occurs when two split IRF fabrics reunite or when two independent IRF fabrics are united, as shown in Figure 3.
MAD
An IRF link failure causes an IRF fabric to split in two IRF fabrics operating with the same Layer 3 settings, including the same IP address. To avoid IP address collision and network problems, IRF uses multi-active detection (MAD) mechanisms to detect the presence of multiple identical IRF fabrics, handle collisions, and recover from faults.
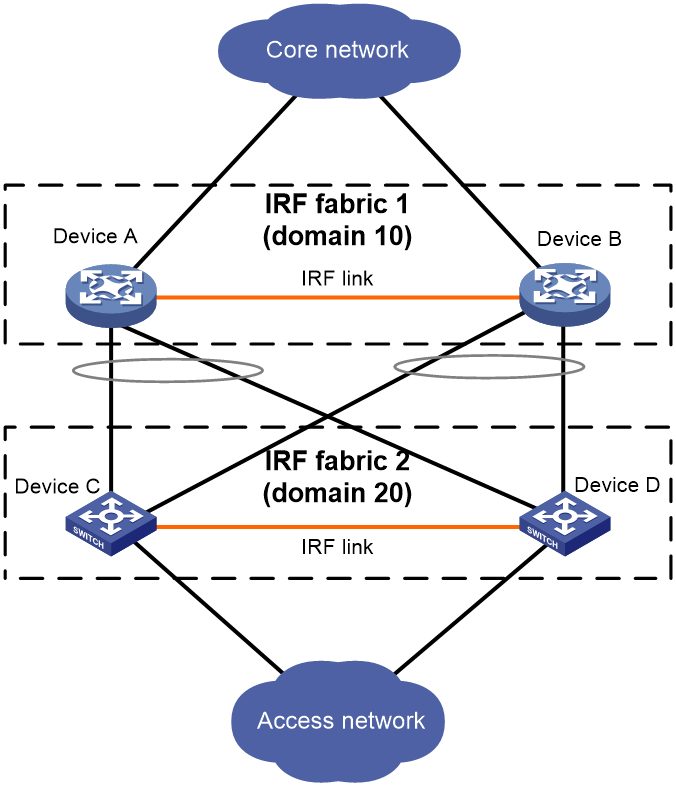
IRF domain ID
One IRF fabric forms one IRF domain. IRF uses IRF domain IDs to uniquely identify IRF fabrics and prevent IRF fabrics from interfering with one another.
As shown in Figure 4, IRF fabric 1 contains Device A and Device B, and IRF fabric 2 contains Device C and Device D. Both fabrics use the LACP aggregate links between them for MAD. When a member device receives an extended LACPDU for MAD, it checks the domain ID to determine whether the packet is from the local IRF fabric. Then, the member device can handle the packet correctly.
Figure 4 A network that contains two IRF domains
IRF network topology
An IRF fabric can use a daisy-chain topology, as shown in Figure 5.
|
IMPORTANT: No relay devices are allowed between IRF member devices. |
Master election
Master election occurs each time the IRF fabric topology changes in the following situations:
· The IRF fabric is established.
· The master device fails or is removed.
· The IRF fabric splits.
· Independent IRF fabrics merge.
|
|
NOTE: Master election does not occur when split IRF fabrics merge. For information about the master device of the merged IRF fabric, see "Failure recovery." |
Master election selects a master in descending order:
1. Current master, even if a new member has higher priority.
When an IRF fabric is being formed, all members consider themselves as the master. This rule is skipped.
2. Member with higher priority.
3. Member with the longest system uptime.
Two members are considered to start up at the same time if the difference between their startup times is equal to or less than 10 minutes. For these members, the next tiebreaker applies.
4. Member with the lowest CPU MAC address.
For the setup of a new IRF fabric, the subordinate devices must reboot to complete the setup after the master election.
For an IRF merge, devices must reboot if they are in the IRF fabric that fails the master election.
Interface naming conventions
A physical interface is numbered in the chassis-number/slot-number/interface-index format.
· chassis-number—Member ID of the device. The default value for this argument is 1. Any change to the member ID takes effect after a reboot.
· slot-number—Slot number of the interface.
· interface-index—Interface index on the device. Interface index depends on the number of physical interfaces available on the device. To identify the index of a physical interface, examine its index mark on the chassis.
For example, GigabitEthernet 2/0/1 represents the first fixed physical interface on member device 2. Set its link type to trunk, as follows:
<Sysname> system-view
[Sysname] interface gigabitethernet 2/0/1
[Sysname-GigabitEthernet2/0/1] port link-type trunk
File system naming conventions
On a single-chassis fabric, you can use its storage device name to access its file system.
On a multichassis IRF fabric, you can use the storage device name to access the file system of the master. To access the file system of any other member device, use the name in the slotmember-ID#storage-device-name format.
For more information about storage device naming conventions, see Fundamentals Configuration Guide.
For example:
· To create and access the test folder under the root directory of the flash memory on the master switch:
<Master> mkdir test
Creating directory flash:/test... Done.
<Master> cd test
<Master> dir
Directory of flash:/test
The directory is empty.
524288 KB total (29832 KB free)
· To create and access the test folder under the root directory of the flash memory on member device 2:
<Master> mkdir slot2#flash:/test
Creating directory slot2#flash:/test... Done.
<Master> cd slot2#flash:/test
<Master> dir
Directory of slot2#flash:/test
The directory is empty.
524288 KB total (128812 KB free)
Configuration synchronization
IRF uses a strict running-configuration synchronization mechanism. In an IRF fabric, all devices obtain and run the running configuration of the master. Configuration changes are automatically propagated from the master to the remaining devices. The configuration files of these devices are retained, but the files do not take effect. The devices use their own startup configuration files only after they are removed from the IRF fabric.
As a best practice, back up the next-startup configuration file on a device before adding the device to an IRF fabric as a subordinate.
A subordinate device's next-startup configuration file might be overwritten if the master and the subordinate use the same file name for their next-startup configuration files. You can use the backup file to restore the original configuration after removing the subordinate from the IRF fabric.
For more information about configuration management, see Fundamentals Configuration Guide.
Multi-active handling procedure
The multi-active handling procedure includes detection, collision handling, and failure recovery.
Detection
IRF provides MAD mechanisms by extending LACP, BFD, ARP, and IPv6 ND to detect multi-active collisions. As a best practice, configure a minimum of one MAD mechanism on an IRF fabric. For more information about the MAD mechanisms and their application scenarios, see "MAD mechanisms."
For information about LACP, see Ethernet link aggregation in Layer 2—LAN Switching Configuration Guide. For information about BFD, see Network Management and Monitoring Configuration Guide. For information about ARP, see Layer 3—IP Services Configuration Guide. For information about ND, see IPv6 basics in Layer 3—IP Services Configuration Guide.
Collision handling
When MAD detects a multi-active collision, it sets all IRF fabrics except one to the Recovery state. The fabric that is not placed in Recovery state can continue to forward traffic. The Recovery-state IRF fabrics are inactive and cannot forward traffic.
LACP MAD and BFD MAD use the following process to handle a multi-active collision:
1. Compare the number of members in each fabric.
2. Set all fabrics to the Recovery state except the one that has the most members.
3. Compare the member IDs of the masters if all IRF fabrics have the same number of members.
4. Set all fabrics to the Recovery state except the one that has the lowest numbered master.
5. Shut down all common network interfaces in the Recovery-state fabrics except for the following interfaces:
¡ Interfaces automatically excluded from being shut down by the system.
¡ Interfaces specified by using the mad exclude interface command.
ARP MAD and ND MAD use the following process to handle a multi-active collision:
1. Compare the member IDs of the masters in the IRF fabrics.
2. Set all fabrics to the Recovery state except the one that has the lowest numbered master.
3. Take the same action on the network interfaces in Recovery-state fabrics as LACP MAD and BFD MAD.
Failure recovery
To merge two split IRF fabrics, first repair the failed IRF link and remove the IRF link failure.
After the failed IRF link between two split IRF fabrics is recovered, reboot the member devices in the inactive IRF fabric. The member devices in the inactive IRF fabric join the active IRF fabric as subordinate devices. The network interfaces that have been shut down by MAD automatically restore their original state, as shown in Figure 6.
|
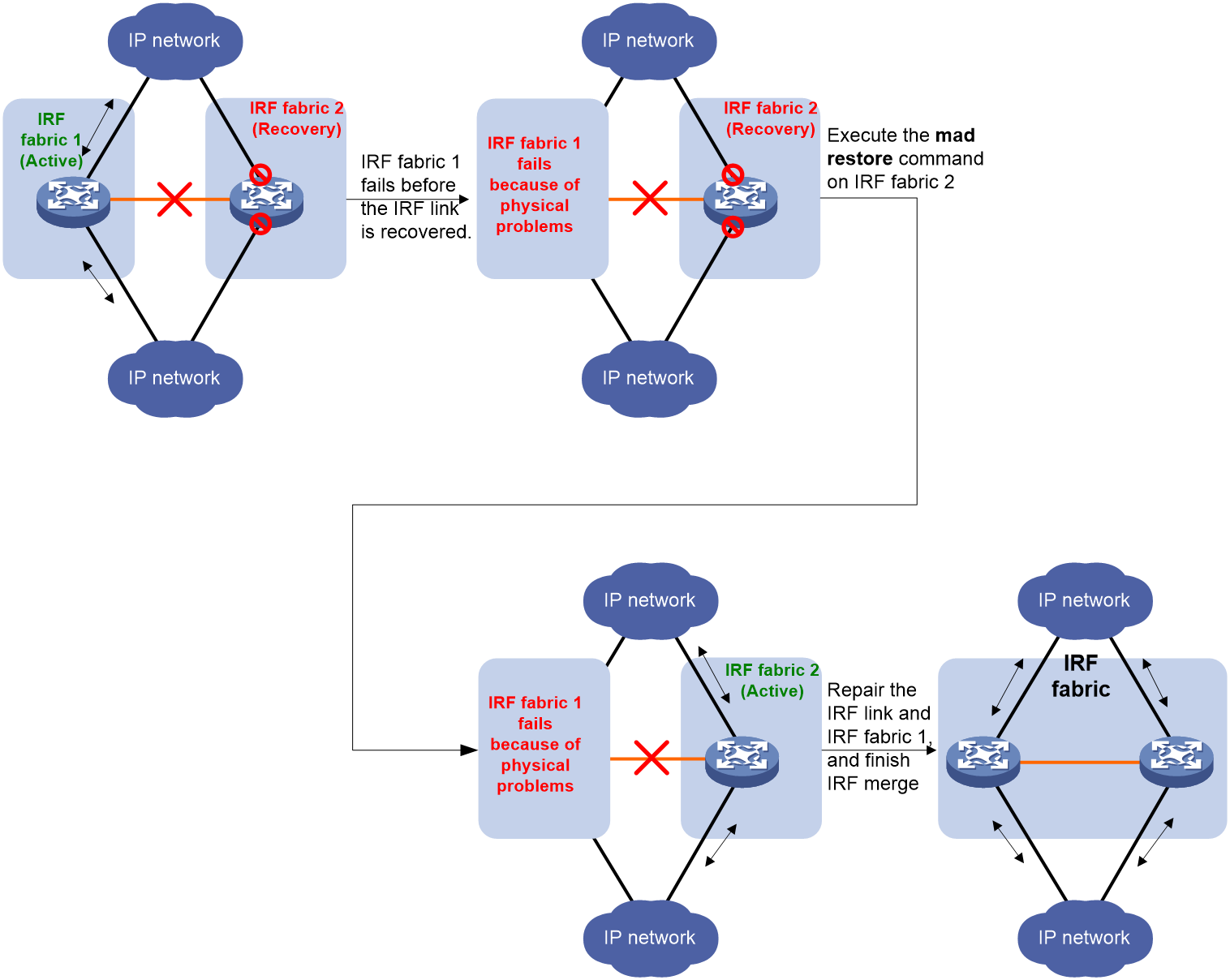
CAUTION: If you inadvertently reboot the active IRF fabric after the failed IRF link recovers, its member devices will join the inactive IRF fabric with their network interfaces being shut down by MAD. To restore the original states of the network interfaces in the merged IRF fabric, use the mad restore command. |
Figure 6 Recovering the IRF fabric
If the active IRF fabric fails before the IRF link is recovered (see Figure 7), use the mad restore command on the inactive IRF fabric to recover the inactive IRF fabric. This command brings up all network interfaces that were shut down by MAD. After the IRF link is repaired, merge the two parts into a unified IRF fabric.
Figure 7 Active IRF fabric fails before the IRF link is recovered
MAD mechanisms
IRF provides MAD mechanisms by extending LACP, BFD, ARP, and IPv6 ND.
Table 1 compares the MAD mechanisms and their application scenarios.
Table 1 Comparison of MAD mechanisms
|
MAD mechanism |
Advantages |
Disadvantages |
Application scenarios |
|
· Detection speed is fast. · Runs on existing aggregate links without requiring MAD-dedicated physical links or Layer 3 interfaces. |
Requires an intermediate device that supports extended LACP for MAD. |
Link aggregation is used between the IRF fabric and its upstream or downstream device. |
|
|
· Detection speed is fast. · Intermediate device, if used, can come from any vendor. |
Requires MAD dedicated physical links and Layer 3 interfaces, which cannot be used for transmitting user traffic. |
· No special requirements for network scenarios. · If no intermediate device is used, this mechanism is only suitable for IRF fabrics that have only two members that are geographically close to one another. |
|
|
· No intermediate device is required. · Intermediate device, if used, can come from any vendor. · Does not require MAD dedicated ports. |
· Detection speed is slower than BFD MAD and LACP MAD. · The spanning tree feature must be enabled. |
Spanning tree-enabled non-link aggregation IPv4 network scenarios. |
|
|
· No intermediate device is required. · Intermediate device, if used, can come from any vendor. · Does not require MAD dedicated ports. |
· Detection speed is slower than BFD MAD and LACP MAD. · The spanning tree feature must be enabled. |
Spanning tree-enabled non-link aggregation IPv6 network scenarios. |
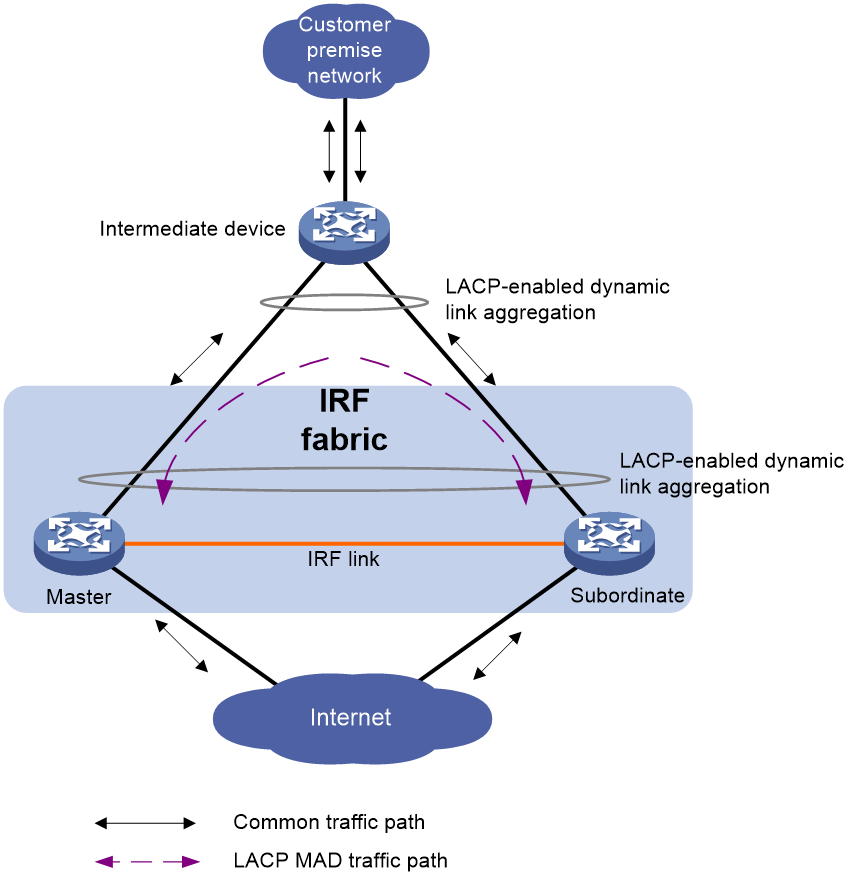
LACP MAD
As shown in Figure 8, LACP MAD has the following requirements:
· Every IRF member must have a link with an intermediate device.
· All the links form a dynamic link aggregation group.
· The intermediate device must be a device that supports extended LACP for MAD.
The IRF member devices send extended LACPDUs that convey a domain ID and an active ID (the member ID of the master). The intermediate device transparently forwards the extended LACPDUs received from one member device to all the other member devices.
· If the domain IDs and active IDs sent by all the member devices are the same, the IRF fabric is integrated.
· If the extended LACPDUs convey the same domain ID but different active IDs, a split has occurred. LACP MAD handles this situation as described in "Collision handling."
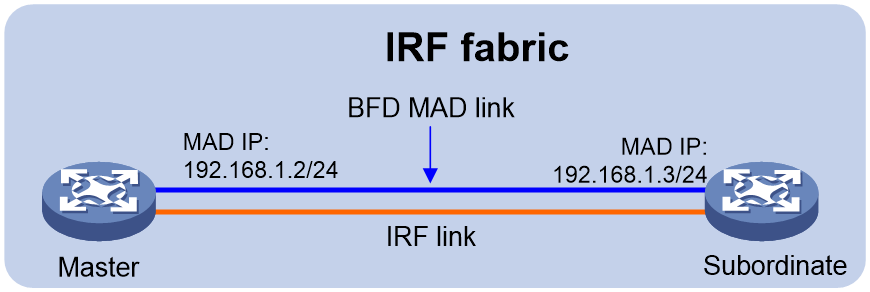
BFD MAD
BFD MAD detects multi-active collisions by using BFD.
You can use common Ethernet ports for BFD MAD.
If management Ethernet ports are used, BFD MAD has the following requirements:
· An intermediate device is required and each IRF member device must have a BFD MAD link to the intermediate device.
· Each member device is assigned a MAD IP address on the master's management Ethernet port.
If common Ethernet ports are used, BFD MAD has the following requirements:
· If an intermediate device is used, each member device must have a BFD MAD link to the intermediate device. If no intermediate device is used, all member devices must have a BFD MAD link to each other. As a best practice, use an intermediate device to connect IRF member devices if the IRF fabric has more than two member devices. A full mesh of IRF members might cause broadcast loops.
· Ports on BFD MAD links are assigned to the same VLAN (or Layer 3 aggregate interface). Each member device is assigned a MAD IP address on the VLAN interface (or Layer 3 aggregate interface).
The BFD MAD links and BFD MAD VLAN (or Layer 3 aggregate interface) must be dedicated. Do not use the BFD MAD links or BFD MAD VLAN (or Layer 3 aggregate interface) for any other purposes.
When you use a Layer 3 aggregate interface for BFD MAD, make sure its member ports do not exceed the maximum number of Selected ports allowed for an aggregation group. If the number of member ports exceeds the maximum number of Selected ports, some member ports cannot become Selected. BFD MAD will be unable to work correctly and its state will change to Faulty. For more information about setting the maximum number of Selected ports for an aggregation group, see Ethernet link aggregation in Layer 2—LAN Switching Configuration Guide.
|
|
NOTE: The MAD addresses identify the member devices and must belong to the same subnet. |
Figure 9 shows a typical BFD MAD scenario that uses an intermediate device. On the intermediate device, assign the ports on the BFD MAD links to the same VLAN.
Figure 10 shows a typical BFD MAD scenario that does not use an intermediate device.
With BFD MAD, the master attempts to establish BFD sessions with other member devices by using its MAD IP address as the source IP address.
· If the IRF fabric is integrated, only the MAD IP address of the master takes effect. The master cannot establish a BFD session with any other member. If you execute the display bfd session command, the state of the BFD sessions is Down.
· When the IRF fabric splits, the IP addresses of the masters in the split IRF fabrics take effect. The masters can establish a BFD session. If you execute the display bfd session command, the state of the BFD session between the two devices is Up.
Figure 9 BFD MAD scenario with an intermediate device
Figure 10 BFD MAD scenario without an intermediate device
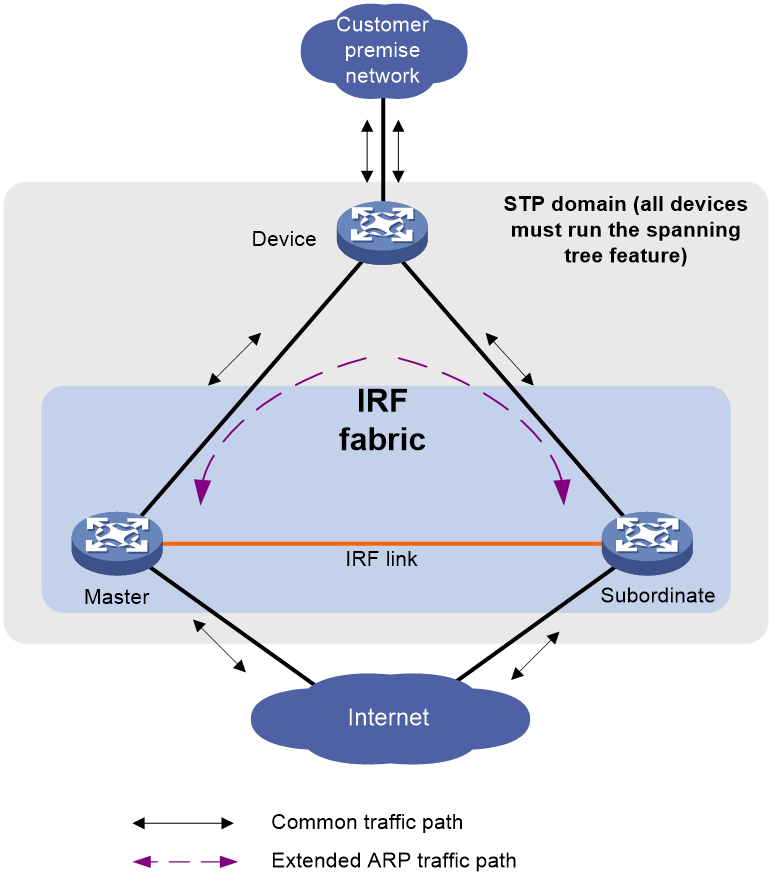
ARP MAD
ARP MAD detects multi-active collisions by using extended ARP packets that convey the IRF domain ID and the active ID (the member ID of the master).
ARP MAD can work with or without an intermediate device. Make sure the following requirements are met:
· If an intermediate device is used, connect each IRF member device to the intermediate device, as shown in Figure 11. Run the spanning tree feature between the IRF fabric and the intermediate device. In this situation, data links can be used.
· If no intermediate device is used, connect each IRF member device to all other member devices. In this situation, IRF links cannot be used for ARP MAD.
Each IRF member compares the domain ID and the active ID (the member ID of the master) in incoming extended ARP packets with its domain ID and active ID.
· If the domain IDs are different, the extended ARP packet is from a different IRF fabric. The device does not continue to process the packet with the MAD mechanism.
· If the domain IDs are the same, the device compares the active IDs.
¡ If the active IDs are different, the IRF fabric has split.
¡ If the active IDs are the same, the IRF fabric is integrated.
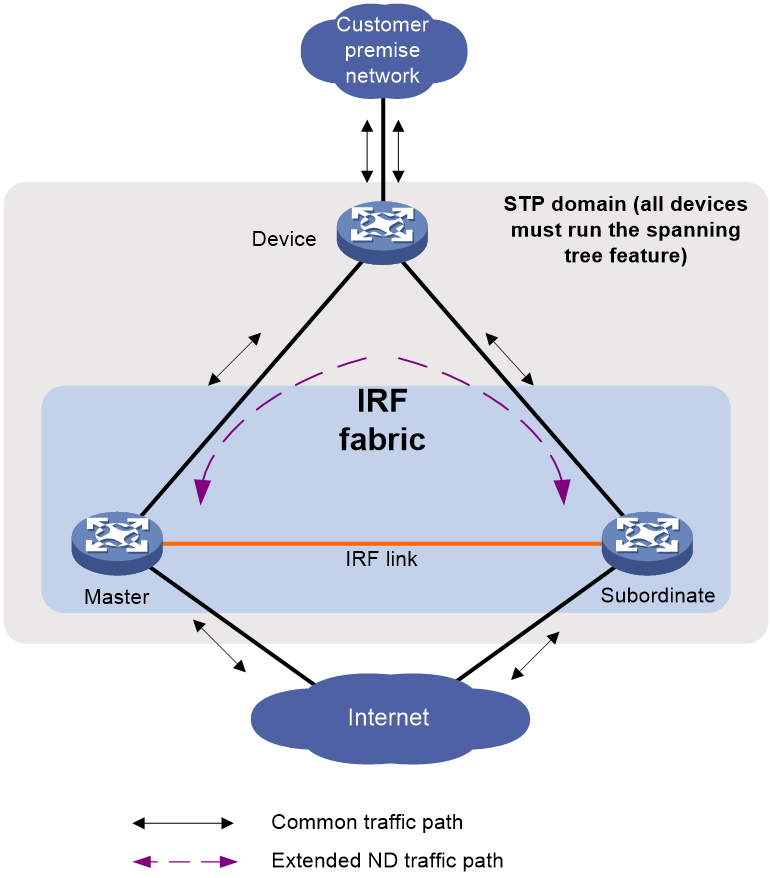
ND MAD
ND MAD detects multi-active collisions by using NS packets to transmit the IRF domain ID and the active ID (the member ID of the master).
You can set up ND MAD links between neighbor IRF member devices or between each IRF member device and an intermediate device (see Figure 12). If an intermediate device is used, you must also run the spanning tree protocol between the IRF fabric and the intermediate device.
Each IRF member device compares the domain ID and the active ID (the member ID of the master) in incoming NS packets with its domain ID and active ID.
· If the domain IDs are different, the NS packet is from a different IRF fabric. The device does not continue to process the packet with the MAD mechanism.
· If the domain IDs are the same, the device compares the active IDs.
¡ If the active IDs are different, the IRF fabric has split.
¡ If the active IDs are the same, the IRF fabric is integrated.
Restrictions: Hardware compatibility with IRF
|
Hardware |
IRF compatibility |
|
F5010, F5020, F5020-GM, F5030, F5030-6GW, F5040, F5060, F5080, F5000-AI-20, F5000-AI-40, F5000-V30, F5000-C, F5000-S, F5000-M, F5000-A |
Yes |
|
F1000-AI-20, F1000-AI-30, F1000-AI-50, F1000-AI-60, F1000-AI-70, F1000-AI-80, F1000-AI-90 |
Yes |
|
F1003-L, F1005-L, F1010-L |
No |
|
F1005, F1010 |
No |
|
F1020, F1020-GM, F1030, F1030-GM, F1050, F1060, F1070, F1070-GM, F1070-GM-L, F1080, F1090, F1000-V70 |
Yes |
|
F1000-AK1110, F1000-AK1120, F1000-AK1130, F1000-AK1140 |
No |
|
F1000-AK1212, F1000-AK1222, F1000-AK1232, F1000-AK1312, F1000-AK1322, F1000-AK1332 |
Yes |
|
F1000-AK1414, F1000-AK1424, F1000-AK1434, F1000-AK1514, F1000-AK1524, F1000-AK1534, F1000-AK1614 |
Yes |
|
F1000-AK108, F1000-AK109, F1000-AK110, F1000-AK115, F1000-AK120, F1000-AK125, F1000-AK710 |
No |
|
F1000-AK130, F1000-AK135, F1000-AK140, F1000-AK145, F1000-AK150, F1000-AK155, F1000-AK160, F1000-AK165, F1000-AK170, F1000-AK175, F1000-AK180, F1000-AK185, F1000-GM-AK370, F1000-GM-AK380, F1000-AK711 |
Yes |
|
LSU3FWCEA0, LSUM1FWCEAB0, LSX1FWCEA1 |
Yes |
|
LSXM1FWDF1, LSUM1FWDEC0, IM-NGFWX-IV, LSQM1FWDSC0, LSWM1FWD0, LSPM6FWD, LSQM2FWDSC0 |
Yes |
|
vFW1000, vFW2000 |
No |
Restrictions and guidelines: IRF configuration
Hardware compatibility with IRF
The device can form an IRF fabric only with devices of the same model.
Software requirements for IRF
All IRF member devices must run the same software image version. Make sure the software auto-update feature is enabled on all member devices.
IRF fabric size
An IRF fabric can contain a maximum of two member devices.
Candidate IRF physical interfaces
As a best practice, use high-speed ports as IRF physical interfaces.
Do not use a port as an IRF physical interface if it has been assigned by default or manually to a bridge instance enabled with security service bypass. For more information about security service bypass, see Layer 2 forwarding in Layer 2—LAN Switching Configuration Guide.
On the LSU3FWCEA0, LSUM1FWCEAB0, and LSX1FWCEA1 modules, only the fiber external ports can be used as IRF physical interfaces.
On H3C SecBlade IV NGFW firewall modules, only the ports on the front panel can be used as IRF physical interfaces. If the panel has both 10-GE and GE ports, only the 10-GE ports can be used as IRF physical interfaces.
On the F5030, F5030-6GW, F5060, F5080, F5000-AI-20, F5000-AI-40, F5000-V30, F5000-M, and F5000-A firewalls, only the following ports can be used as IRF physical interfaces:
· Fixed ports in fiber mode.
· Ports on slot 1.
· Ports on slot 2.
To use a port as an IRF physical interface, use the port group interface command to bind the port to an IRF port.
Transceiver modules and cables selection for IRF
When you select transceiver modules and cables, follow these restrictions and guidelines:
· Use Category 5 (or above) twisted-pair cables to connect 10/100/1000Mbps Ethernet ports for a short-distance connection.
· Use SFP or SFP+ DAC cables to connect SFP or SFP+ ports for a short-distance connection.
· Use SFP or SFP+ transceiver modules and fibers to connect SFP or SFP+ ports for a long-distance connection.
· The transceiver modules at the two ends of an IRF link must be the same type.
For more information about the transceiver modules and DAC cables, see the device installation guide and H3C Transceiver Modules User Guide.
|
|
NOTE: The transceiver modules and DAC cables available for the device are subject to change over time. For the most up-to-date list of transceiver modules and DAC cables, contact your H3C sales representative. |
IRF port connection
When you connect two neighboring IRF members, follow these restrictions and guidelines:
· You must connect the physical interfaces of IRF-port 1 on one member to the physical interfaces of IRF-port 2 on the other.
· For high availability, bind multiple physical interfaces to an IRF port.
· No relay devices are allowed between neighboring members.
Figure 13 Connecting IRF physical interfaces
IRF physical interface configuration restrictions and guidelines
Command configuration restrictions
On a physical interface bound to an IRF port, you can execute only the following commands:
· Interface commands, including:
¡ description.
¡ flow-interval.
¡ shutdown.
For more information about these commands, see Ethernet interface configuration in Interface Command Reference.
· The itu-channel command for setting the ITU channel number for a transceiver module. For more information about this command, see device management commands in Fundamentals Command Reference.
· LLDP commands, including:
¡ lldp admin-status.
¡ lldp check-change-interval.
¡ lldp enable.
¡ lldp encapsulation snap.
¡ lldp notification remote-change enable.
¡ lldp tlv-enable.
For more information about these commands, see Layer 2—LAN Switching Command Reference.
· The mirroring-group reflector-port command, which specifies the physical interface as a reflector port for remote mirroring. For more information about this command, see port mirroring in Network Management and Monitoring Command Reference.
|
IMPORTANT: Do not execute the mirroring-group reflector-port command on an IRF physical interface if that interface is the only member interface of an IRF port. Doing so will split the IRF fabric, because this command also removes the binding of the physical interface and IRF port. |
Feature compatibility and configuration restrictions with IRF
ACL
To form an IRF fabric, all member devices in the IRF fabric must have the same settings for the ACL hardware mode. For more information about hardware-based ACLs, see ACL and QoS Configuration Guide.
Licensing requirements for IRF
For a license-based feature to run correctly on an IRF fabric, make sure the licenses installed for the feature on all member devices are the same. For more information about feature licensing, see Fundamentals Configuration Guide.
Configuration rollback restrictions
The configuration rollback feature cannot roll back the following IRF settings:
· Member device description (set by using the irf member description command).
· Member device priority (set by using the irf member priority command).
· IRF physical interface and IRF port bindings (set by using the port group interface command).
For more information about the configuration rollback feature, see configuration file management in Fundamentals Configuration Guide.
IRF tasks at a glance
To configure IRF, perform the following tasks:
Configure a minimum of one MAD mechanism on an IRF fabric.
¡ Excluding interfaces from the shutdown action upon detection of multi-active collision
This feature excludes an interface from the shutdown action for management or other special purposes when an IRF fabric transits to the Recovery state.
3. (Optional.) Optimizing IRF settings for an IRF fabric
¡ Configuring a member device description
¡ Configuring IRF link load sharing mode
¡ Configuring the IRF bridge MAC address
¡ Enabling software auto-update for software image synchronization
This feature automatically synchronizes the current software images of the master to devices that are attempting to join the IRF fabric.
¡ Removing an expansion interface card that has IRF physical interfaces
¡ Replacing an expansion interface card that has IRF physical interfaces
Planning the IRF fabric setup
Consider the following items when you plan an IRF fabric:
· Hardware compatibility and restrictions.
· IRF fabric size.
· Master device.
· Member ID and priority assignment scheme.
· Fabric topology and cabling scheme.
· IRF physical interfaces.
Setting up an IRF fabric
IRF setup tasks at a glance
To set up an IRF fabric, perform the following tasks:
1. Configure member IDs, priorities, and IRF physical interfaces separately.
a. Assigning a member ID to each IRF member device
b. (Optional.) Specifying a priority for each member device
c. Binding physical interfaces to IRF ports
Skip these tasks if you configure member IDs, priorities, domain ID, and IRF physical interfaces in bulk.
2. Bulk-configuring basic IRF settings for a member device
Skip this task if you configure member IDs, priorities, domain ID, and IRF physical interfaces separately.
3. Connecting IRF physical interfaces
Assigning a member ID to each IRF member device
Restrictions and guidelines
To create an IRF fabric, you must assign a unique IRF member ID to each member device.
The new member ID of a device takes effect at a reboot. After the device reboots, the settings on all member ID-related physical resources (including common physical network interfaces) are removed, regardless of whether you have saved the configuration.
After the IRF fabric is formed, you can perform this task to change the member ID of a device. However, doing so might cause undesirable interface configuration changes and data loss. Before you do that, back up the configuration, and make sure you fully understand the impact on your network.
Procedure
1. Enter system view.
system-view
2. Assign a member ID to a member device.
irf member member-id renumber new-member-id
The default IRF member ID is 1.
3. (Optional.) Save the configuration.
save
If you have bound physical interfaces to IRF ports or assigned member priority, you must perform this step for these settings to take effect after the reboot.
4. Return to user view.
quit
5. Reboot the device.
reboot [ slot slot-number ] [ force ]
Specifying a priority for each member device
About this task
IRF member priority represents the possibility for a device to be elected the master in an IRF fabric. A larger priority value indicates a higher priority.
A change to member priority affects the election result at the next master election, but it does not cause an immediate master re-election.
Procedure
1. Enter system view.
system-view
2. Specify a priority for the device.
irf member member-id priority priority
The default IRF member priority is 1.
Binding physical interfaces to IRF ports
Restrictions and guidelines
Select qualified physical interfaces as IRF physical interfaces as described in "Candidate IRF physical interfaces."
Make sure the IRF physical interfaces of an IRF port use the same binding mode.
After binding physical interfaces to IRF ports for the first time, you must use the irf-port-configuration active command to activate the settings on the IRF ports.
The system activates the IRF port settings automatically only in the following situations:
· The configuration file that the device starts with contains IRF port bindings.
· You are adding physical interfaces to an IRF port (in UP state) after an IRF fabric is formed.
Procedure
1. Enter system view.
system-view
2. Enter interface view or interface range view.
¡ Enter interface view.
interface interface-type interface-number
¡ Enter interface range view. Choose one of the following commands:
interface range { interface-type interface-number [ to interface-type interface-number ] } &<1-24>
interface range name name [ interface { interface-type interface-number [ to interface-type interface-number ] } &<1-24> ]
To shut down a range of IRF physical interfaces, enter interface range view.
To shut down one IRF physical interface, enter its interface view.
3. Shut down the physical interfaces.
shutdown
By default, a physical interface is not administratively down.
You must always shut down a physical interface before binding it to an IRF port or removing the binding. If the system prevents you from shutting down an interface, follow the system instructions to disable its peer interface.
4. Return to system view.
quit
5. Enter IRF port view.
irf-port member-id/irf-port-number
6. Bind each physical interface to the IRF port.
port group interface interface-type interface-number
By default, no physical interfaces are bound to an IRF port.
Repeat this step to assign multiple physical interfaces to the IRF port.
7. Return to system view.
quit
8. Enter interface view or interface range view.
¡ Enter interface view.
interface interface-type interface-number
¡ Enter interface range view. Choose one of the following commands:
interface range { interface-type interface-number [ to interface-type interface-number ] } &<1-24>
interface range name name [ interface { interface-type interface-number [ to interface-type interface-number ] } &<1-24> ]
9. Bring up the physical interfaces.
undo shutdown
10. Return to system view.
quit
11. Save the configuration.
save
Activating IRF port configurations causes IRF merge and reboot. To avoid data loss, save the running configuration to the startup configuration file before you perform the operation.
12. Activate the IRF port settings.
irf-port-configuration active
Bulk-configuring basic IRF settings for a member device
About this task
Use the easy IRF feature to bulk-configure basic IRF settings for a member device, including the member ID, domain ID, priority, and IRF port bindings.
The easy IRF feature provides the following configuration methods:
· Interactive method—Enter the easy-irf command without parameters. The system will guide you to set the parameters step by step.
· Non-interactive method—Enter the easy-irf command with parameters.
As a best practice, use the interactive method if you are new to IRF.
Restrictions and guidelines
The member device reboots immediately after you specify a new member ID for it. Make sure you are aware of the impact on the network.
If you execute the easy-irf command multiple times, the following settings take effect:
· The most recent settings for the member ID, domain ID, and priority.
· IRF port bindings added through repeated executions of the command. To remove an IRF physical interface from an IRF port, you must use the undo port group interface command in IRF port view.
If you specify IRF physical interfaces by using the interactive method, you must also follow these restrictions and guidelines:
· Do not enter spaces between the interface type and interface number.
· Use a comma (,) to separate two physical interfaces. No spaces are allowed between interfaces.
Procedure
1. Enter system view.
system-view
2. Bulk-configure basic IRF settings for the device.
easy-irf [ member member-id [ renumber new-member-id ] domain domain-id [ priority priority ] [ irf-port1 interface-list1 ] [ irf-port2 interface-list2 ] ]
Make sure the new member ID is unique in the IRF fabric to which the device will be added.
Connecting IRF physical interfaces
Follow the restrictions in "IRF port connection" to connect IRF physical interfaces as well as based on the topology and cabling scheme. The devices perform master election. The member devices that fail the master election automatically reboot to form an IRF fabric with the master device.
Accessing the IRF fabric
The IRF fabric appears as one device after it is formed. You configure and manage all IRF members at the CLI of the master. All settings you have made are automatically propagated to the IRF members.
The following methods are available for accessing an IRF fabric:
· Local login—Log in through the console port of any member device.
· Remote login—Log in at a Layer 3 interface on any member device by using methods including Telnet and SNMP.
When you log in to an IRF fabric, you are placed at the CLI of the master, regardless of at which member device you are logged in.
For more information, see login configuration in Fundamentals Configuration Guide.
Configuring MAD
Restrictions and guidelines for MAD configuration
MAD mechanism compatibility
As a best practice, configure a minimum of one MAD mechanism on an IRF fabric for prompt IRF split detection. Because MAD mechanisms use different collision handling processes, follow these restrictions and guidelines when you configure multiple MAD mechanisms on an IRF fabric:
· Do not configure LACP MAD together with ARP MAD or ND MAD.
· Do not configure BFD MAD together with ARP MAD or ND MAD.
Assigning IRF domain IDs
An IRF fabric has only one IRF domain ID.
You can change the IRF domain ID by using the following commands: irf domain, mad enable, mad arp enable, or mad nd enable. The IRF domain IDs configured by using these commands overwrite each other.
If you change the IRF domain ID in one context, the IRF domain IDs in all other contexts change automatically. The irf domain command is available only on the default context. The mad enable, mad arp enable, and mad nd enable commands are available on any contexts.
If LACP MAD, ARP MAD, or ND MAD runs between two IRF fabrics, assign each fabric a unique IRF domain ID. (For BFD MAD, this task is optional.)
Actions on interfaces shut down by MAD
To prevent a multi-active collision from causing network issues, avoid using the undo shutdown command to bring up the interfaces shut down by a MAD mechanism on a Recovery-state IRF fabric.
Configuring LACP MAD
1. Enter system view.
system-view
2. Assign a domain ID to the IRF fabric.
irf domain domain-id
The default IRF domain ID is 0.
3. Create an aggregate interface and enter aggregate interface view.
¡ Enter Layer 2 aggregate interface view.
interface bridge-aggregation interface-number
¡ Enter Layer 3 aggregate interface view.
interface route-aggregation interface-number
Perform this step also on the intermediate device.
4. Configure the aggregation group to operate in dynamic aggregation mode.
link-aggregation mode dynamic
By default, an aggregation group operates in static aggregation mode.
LACP MAD takes effect only on dynamic aggregate interfaces.
Perform this step also on the intermediate device.
5. Enable LACP MAD.
mad enable
By default, LACP MAD is disabled.
6. Return to system view.
quit
7. Enter Ethernet interface view or interface range view.
¡ Enter Ethernet interface view.
interface interface-type interface-number
¡ Enter interface range view. Choose one of the following commands:
interface range { interface-type interface-number [ to interface-type interface-number ] } &<1-24>
interface range name name [ interface { interface-type interface-number [ to interface-type interface-number ] } &<1-24> ]
To assign a range of ports to the aggregation group, enter interface range view.
To assign one port to the aggregation group, enter Ethernet interface view.
8. Assign the Ethernet port or the range of Ethernet ports to the specified aggregation group.
port link-aggregation group group-id
Multichassis link aggregation is allowed.
Perform this step also on the intermediate device.
Configuring BFD MAD
Restrictions and guidelines for configuring BFD MAD
As a best practice, use the following procedure to set up BFD MAD:
1. Choose a BFD MAD link scheme as described in "BFD MAD."
2. Configure BFD MAD.
3. Connect the BFD MAD links.
When you configure BFD MAD on a VLAN interface, follow these restrictions and guidelines:
|
Category |
Restrictions and guidelines |
|
BFD MAD VLAN |
· Do not enable BFD MAD on VLAN-interface 1. · If you are using an intermediate device, perform the following tasks: ¡ On the IRF fabric and the intermediate device, create a VLAN for BFD MAD. ¡ On the IRF fabric and the intermediate device, assign the ports of BFD MAD links to the BFD MAD VLAN. ¡ On the IRF fabric, create a VLAN interface for the BFD MAD VLAN. · Make sure the IRF fabrics on the network use different BFD MAD VLANs. · Make sure the BFD MAD VLAN contains only ports on the BFD MAD links. Exclude a port from the BFD MAD VLAN if that port is not on a BFD MAD link. If you have assigned that port to all VLANs by using the port trunk permit vlan all command, use the undo port trunk permit command to exclude that port from the BFD MAD VLAN. |
|
BFD MAD VLAN and feature compatibility |
Do not use the BFD MAD VLAN and its member ports for any purpose other than configuring BFD MAD. · Use only the mad bfd enable and mad ip address commands on the BFD MAD-enabled VLAN interface. If you configure other features, both BFD MAD and other features on the interface might run incorrectly. · Disable the spanning tree feature on any Layer 2 Ethernet ports in the BFD MAD VLAN. The MAD feature is mutually exclusive with the spanning tree feature. |
|
MAD IP address |
· To avoid network issues, only use the mad ip address command to configure IP addresses on the BFD MAD-enabled VLAN interface. Do not configure an IP address by using the ip address command or configure a VRRP virtual address on the BFD MAD-enabled VLAN interface. · Make sure all the MAD IP addresses are on the same subnet. |
When you configure BFD MAD on a Layer 3 aggregate interface, follow these restrictions and guidelines:
|
Category |
Restrictions and guidelines |
|
BFD MAD-enabled Layer 3 aggregate interface |
· Make sure the Layer 3 aggregate interface operates in static aggregation mode. · Make sure the member ports in the aggregation group do not exceed the maximum number of Selected ports allowed for an aggregation group. If the number of member ports exceeds the maximum number of Selected ports, some member ports cannot become Selected. BFD MAD will be unable to work correctly and its state will change to Faulty. |
|
BFD MAD VLAN |
· On the intermediate device (if any), assign the ports on the BFD MAD links to the same VLAN. Do not assign the ports to an aggregate interface. If the ports are hybrid ports, make sure these ports are untagged members of their PVIDs. · If the intermediate device acts as a BFD MAD intermediate device for multiple IRF fabrics, assign different BFD MAD VLANs to the IRF fabrics. · Do not use the BFD MAD VLAN on the intermediate device for any purposes other than BFD MAD. · Make sure the BFD MAD VLAN on the intermediate device contains only ports on the BFD MAD links. Exclude a port from the BFD MAD VLAN if that port is not on a BFD MAD link. If you have assigned that port to all VLANs by using the port trunk permit vlan all command, use the undo port trunk permit command to exclude that port from the BFD MAD VLAN. |
|
BFD MAD-enabled Layer 3 aggregate interface and feature compatibility |
Use only the mad bfd enable and mad ip address commands on the BFD MAD-enabled interface. If you configure other features, both BFD MAD and other features on the interface might run incorrectly. |
|
MAD IP address |
· To avoid network issues, only use the mad ip address command to configure IP addresses on the BFD MAD-enabled interface. Do not configure an IP address by using the ip address command or configure a VRRP virtual address on the BFD MAD-enabled interface. · Make sure all the MAD IP addresses are on the same subnet. |
Configuring BFD MAD on a VLAN interface
1. Enter system view.
system-view
2. (Optional.) Assign a domain ID to the IRF fabric.
irf domain domain-id
By default, the domain ID of an IRF fabric is 0.
3. Create a VLAN dedicated to BFD MAD.
vlan vlan-id
By default, only VLAN 1 exists.
4. Return to system view.
quit
5. Enter Ethernet interface view or interface range view.
¡ Enter Ethernet interface view.
interface interface-type interface-number
¡ Enter interface range view. Choose one of the following commands:
interface range { interface-type interface-number [ to interface-type interface-number ] } &<1-24>
interface range name name [ interface { interface-type interface-number [ to interface-type interface-number ] } &<1-24> ]
To assign a range of ports to the BFD MAD VLAN, enter interface range view.
To assign one port to the BFD MAD VLAN, enter Ethernet interface view.
6. Assign the port or the range of ports to the BFD MAD VLAN.
¡ Assign the ports to the VLAN as access ports.
port access vlan vlan-id
¡ Assign the ports to the VLAN as trunk ports.
port trunk permit vlan vlan-id
¡ Assign the ports to the VLAN as hybrid ports.
port hybrid vlan vlan-id { tagged | untagged }
The link type of BFD MAD ports can be access, trunk, or hybrid.
The default link type of a port is access.
7. Return to system view.
quit
8. Enter VLAN interface view.
interface vlan-interface vlan-interface-id
9. Enable BFD MAD.
mad bfd enable
By default, BFD MAD is disabled.
10. Assign a MAD IP address to a member device on the VLAN interface.
mad ip address ip-address { mask | mask-length } member member-id
By default, no MAD IP addresses are configured on any VLAN interfaces.
Repeat this step to assign a MAD IP address to each member device on the VLAN interface.
Configuring BFD MAD on a Layer 3 aggregate interface
1. Enter system view.
system-view
2. (Optional.) Assign a domain ID to the IRF fabric.
irf domain domain-id
By default, the domain ID of an IRF fabric is 0.
3. Create a Layer 3 aggregate interface for BFD MAD.
interface route-aggregation interface-number
4. Return to system view.
quit
5. Enter interface view or interface range view.
¡ Enter Ethernet interface view.
interface interface-type interface-number
¡ Enter interface range view. Choose one of the following commands:
interface range { interface-type interface-number [ to interface-type interface-number ] } &<1-24>
interface range name name [ interface { interface-type interface-number [ to interface-type interface-number ] } &<1-24> ]
To assign a range of ports to the aggregation group for the aggregate interface, enter interface range view.
To assign one port to the aggregation group for the aggregate interface, enter Ethernet interface view.
6. Assign the port or the range of ports to the aggregation group for the aggregate interface.
port link-aggregation group number
7. Return to system view.
quit
8. Enter Layer 3 aggregate interface view.
interface route-aggregation interface-number
9. Enable BFD MAD.
mad bfd enable
By default, BFD MAD is disabled.
10. Assign a MAD IP address to a member device on the Layer 3 aggregate interface.
mad ip address ip-address { mask | mask-length } member member-id
By default, no MAD IP addresses are configured on aggregate interfaces.
Repeat this step to assign a MAD IP address to each member device on the aggregate interface.
Configuring ARP MAD
Restrictions and guidelines
As a best practice, use the following procedure to set up ARP MAD:
1. Choose an ARP MAD link scheme as described in "ARP MAD."
2. Configure ARP MAD.
3. Connect the ARP MAD links if you are not using existing data links as ARP MAD links.
When you configure ARP MAD, follow these restrictions and guidelines:
|
Category |
Restrictions and guidelines |
|
ARP MAD VLAN |
· Do not enable ARP MAD on VLAN-interface 1. · If you are using an intermediate device, perform the following tasks: ¡ On the IRF fabric and the intermediate device, create a VLAN for ARP MAD. ¡ On the IRF fabric and the intermediate device, assign the ports of ARP MAD links to the ARP MAD VLAN. ¡ On the IRF fabric, create a VLAN interface for the ARP MAD VLAN. · Do not use the ARP MAD VLAN for any other purposes. |
|
ARP MAD and feature configuration |
If an intermediate device is used, make sure the following requirements are met: · Run the spanning tree feature between the IRF fabric and the intermediate device to ensure that there is only one ARP MAD link in forwarding state. For more information about the spanning tree feature and its configuration, see Layer 2—LAN Switching Configuration Guide. · Enable the IRF fabric to change its bridge MAC address as soon as the address owner leaves. · If the intermediate device is also an IRF fabric, assign the two IRF fabrics different domain IDs for correct split detection. |
Procedure
1. Enter system view.
system-view
2. Assign a domain ID to the IRF fabric.
irf domain domain-id
The default IRF domain ID is 0.
3. Configure the IRF bridge MAC address to change as soon as the address owner leaves.
undo irf mac-address persistent
By default, the IRF bridge MAC address remains unchanged for 6 minutes after the address owner leaves.
4. Create a VLAN dedicated to ARP MAD.
vlan vlan-id
By default, only VLAN 1 exists.
5. Return to system view.
quit
6. Enter Ethernet interface view or interface range view.
¡ Enter Ethernet interface view.
interface interface-type interface-number
¡ Enter interface range view. Choose one of the following commands:
interface range { interface-type interface-number [ to interface-type interface-number ] } &<1-24>
interface range name name [ interface { interface-type interface-number [ to interface-type interface-number ] } &<1-24> ]
To assign a range of ports to the ARP MAD VLAN, enter interface range view.
To assign one port to the ARP MAD VLAN, enter Ethernet interface view.
7. Assign the port or the range of ports to the ARP MAD VLAN.
¡ Assign the ports to the VLAN as access ports.
port access vlan vlan-id
¡ Assign the ports to the VLAN as trunk ports.
port trunk permit vlan vlan-id
¡ Assign the ports to the VLAN as hybrid ports.
port hybrid vlan vlan-id { tagged | untagged }
The link type of ARP MAD ports can be access, trunk, or hybrid.
The default link type of a port is access.
8. Return to system view.
quit
9. Enter VLAN interface view.
interface vlan-interface vlan-interface-id
10. Assign the interface an IP address.
ip address ip-address { mask | mask-length }
By default, no IP addresses are assigned to any VLAN interfaces.
11. Enable ARP MAD.
mad arp enable
By default, ARP MAD is disabled.
Configuring ND MAD
Restrictions and guidelines
When you use ND MAD, follow these guidelines:
· If an intermediate device is used, you can use common data links as ND MAD links. If no intermediate device is used, set up dedicated ND MAD links between IRF member devices.
· If an intermediate device is used, make sure the following requirements are met:
¡ Run the spanning tree feature between the IRF fabric and the intermediate device. Make sure there is only one ND MAD link in forwarding state. For more information about the spanning tree feature and its configuration, see Layer 2—LAN Switching Configuration Guide.
¡ Enable the IRF fabric to change its bridge MAC address as soon as the address owner leaves.
¡ If the intermediate device is also an IRF fabric, assign the two IRF fabrics different domain IDs for correct split detection.
Procedure
1. Enter system view.
system-view
2. Assign a domain ID to the IRF fabric.
irf domain domain-id
The default IRF domain ID is 0.
3. Configure the IRF bridge MAC address to change as soon as the address owner leaves.
undo irf mac-address persistent
By default, the IRF bridge MAC address remains unchanged for 6 minutes after the address owner leaves.
4. Create a VLAN dedicated to ND MAD.
vlan vlan-id
By default, only VLAN 1 exists.
Do not configure ND MAD on VLAN-interface 1.
Do not use the VLAN configured for ND MAD for any other purposes.
Perform this task also on the intermediate device (if any).
5. Return to system view.
quit
6. Enter Ethernet interface view or interface range view.
¡ Enter Ethernet interface view.
interface interface-type interface-number
¡ Enter interface range view. Choose one of the following commands:
interface range { interface-type interface-number [ to interface-type interface-number ] } &<1-24>
interface range name name [ interface { interface-type interface-number [ to interface-type interface-number ] } &<1-24> ]
To assign a range of ports to the ND MAD VLAN, enter interface range view.
To assign one port to the ND MAD VLAN, enter Ethernet interface view.
7. Assign the port or the range of ports to the ND MAD VLAN.
¡ Assign the ports to the VLAN as access ports.
port access vlan vlan-id
¡ Assign the ports to the VLAN as trunk ports.
port trunk permit vlan vlan-id
¡ Assign the ports to the VLAN as hybrid ports.
port hybrid vlan vlan-id { tagged | untagged }
The link type of ND MAD ports can be access, trunk, or hybrid.
The default link type of a port is access.
Perform this task also on the intermediate device (if any).
8. Return to system view.
quit
9. Enter VLAN interface view.
interface vlan-interface vlan-interface-id
10. Assign the interface an IPv6 address.
ipv6 address { ipv6-address/prefix-length | ipv6-address prefix-length }
By default, no IPv6 addresses are assigned to any VLAN interfaces.
11. Enable ND MAD.
mad nd enable
By default, ND MAD is disabled.
Excluding interfaces from the shutdown action upon detection of multi-active collision
About this task
When an IRF fabric transits to the Recovery state, the system automatically excludes the following network interfaces from being shut down:
· IRF physical interfaces.
· Member interfaces of an aggregate interface if the aggregate interface is excluded from being shut down.
You can exclude a network interface from the shutdown action for management or other special purposes. For example:
· Exclude a port from the shutdown action so you can Telnet to the port for managing the device.
· Exclude a VLAN interface and its Layer 2 ports from the shutdown action so you can log in through the VLAN interface.
Restrictions and guidelines
If the Layer 2 ports of a VLAN interface are distributed on multiple member devices, the exclusion operation might introduce IP collision risks. The VLAN interface might be up on both active and inactive IRF fabrics.
Procedure
1. Enter system view.
system-view
2. Configure a network interface to not shut down when the IRF fabric transits to the Recovery state.
mad exclude interface interface-type interface-number
By default, all network interfaces on a Recovery-state IRF fabric are shut down, except for the network interfaces automatically excluded by the system.
Recovering an IRF fabric
About this task
For split IRF fabrics, if the active IRF fabric fails before the IRF link is recovered, perform this task on the inactive IRF fabric to recover the inactive IRF fabric. The manual recovery operation brings up all interfaces that were shut down by MAD on the inactive IRF fabric.
Procedure
1. Enter system view.
system-view
2. Recover the inactive IRF fabric.
mad restore
Optimizing IRF settings for an IRF fabric
Configuring a member device description
1. Enter system view.
system-view
2. Configure a description for a member device.
irf member member-id description text
By default, no member device description is configured.
Configuring IRF link load sharing mode
About this task
On an IRF port, traffic is balanced across its physical links.
You can configure the IRF port to distribute traffic based on any combination of the following criteria:
· IP addresses.
· MAC addresses.
The system displays an error message if a criteria combination is not supported.
The criteria can also be packet types, such as Layer 2, IPv4, and IPv6.
Restrictions and guidelines for configuring IRF link load sharing mode
Configure the IRF link load sharing mode for IRF links in system view or IRF port view:
· In system view, the configuration is global and takes effect on all IRF ports.
· In IRF port view, the configuration is port specific and takes effect only on the specified IRF port.
An IRF port preferentially uses the port-specific load sharing mode. If no port-specific load sharing mode is available, the IRF port uses the global load sharing mode.
Before you configure a port-specific load sharing mode, make sure you have bound a minimum of one physical interface to the IRF port.
Configuring the global load sharing mode
1. Enter system view.
system-view
2. Configure the global IRF link load sharing mode.
irf-port global load-sharing mode { destination-ip | destination-mac | source-ip | source-mac } *
By default, packets are distributed based on the load sharing mode automatically selected depending on the packet type.
If you execute this command multiple times, the most recent configuration takes effect.
Configuring a port-specific load sharing mode
1. Enter system view.
system-view
2. Enter IRF port view.
irf-port member-id/irf-port-number
3. Configure the port-specific load sharing mode.
irf-port load-sharing mode { destination-ip | destination-mac | source-ip | source-mac } *
By default, packets are distributed based on the load sharing mode automatically selected depending on the packet type.
If you execute this command multiple times, the most recent configuration takes effect.
Configuring the IRF bridge MAC address
About this task
The bridge MAC address of a system must be unique on a switched LAN. IRF bridge MAC address identifies an IRF fabric by Layer 2 protocols (for example, LACP) on a switched LAN.
By default, an IRF fabric uses the bridge MAC address of the master as the IRF bridge MAC address. After the master leaves, the IRF bridge MAC address persists for a period of time or permanently depending on the IRF bridge MAC persistence setting. When the IRF bridge MAC persistence timer expires, the IRF fabric uses the bridge MAC address of the current master as the IRF bridge MAC address.
If IRF fabric merge occurs, IRF determines the IRF bridge MAC address of the merged IRF fabric as follows:
1. When IRF fabrics merge, IRF ignores the IRF bridge MAC addresses and checks the bridge MAC address of each member device in the IRF fabrics. IRF merge fails if any two member devices have the same bridge MAC address.
2. After IRF fabrics merge, the merged IRF fabric uses the bridge MAC address of the merging IRF fabric that won the master election as the IRF bridge MAC address.
Restrictions and guidelines
|
CAUTION: The bridge MAC address change causes transient traffic disruption. |
When you configure IRF bridge MAC persistence, follow these restrictions and guidelines:
· If ARP MAD or ND MAD is used with the spanning tree feature, you must disable IRF bridge MAC persistence by using the undo irf mac-address persistent command.
· If the IRF fabric has multichassis aggregate links, do not use the undo irf mac-address persistent command. Use of this command might cause traffic disruption.
Configuring IRF bridge MAC persistence
1. Enter system view.
system-view
2. Configure IRF bridge MAC persistence.
¡ Retain the bridge MAC address permanently even if the address owner has left the fabric.
irf mac-address persistent always
¡ Retain the bridge MAC address for 6 minutes after the address owner leaves the fabric.
irf mac-address persistent timer
¡ Change the bridge MAC address as soon as the address owner leaves the fabric.
undo irf mac-address persistent
By default, the IRF bridge MAC address remains unchanged for 6 minutes after the address owner leaves.
The irf mac-address persistent timer command avoids unnecessary bridge MAC address changes caused by device reboot, transient link failure, or purposeful link disconnection.
Enabling software auto-update for software image synchronization
About this task
The software auto-update feature automatically synchronizes the current software images of the master to devices that are attempting to join the IRF fabric.
To join an IRF fabric, a device must use the same software images as the master in the fabric.
When you add a device to the IRF fabric, software auto-update compares the startup software images of the device with the current software images of the IRF master. If the two sets of images are different, the device automatically performs the following operations:
1. Downloads the current software images of the master.
2. Sets the downloaded images as its main startup software images.
3. Reboots with the new software images to rejoin the IRF fabric.
You must manually update the new device with the software images running on the IRF fabric if software auto-update is disabled.
Restrictions and guidelines
To ensure a successful software auto-update in a multi-user environment, prevent anyone from rebooting member devices during the auto-update process. To inform administrators of the auto-update status, configure the information center to output the status messages to configuration terminals (see Network Management and Monitoring Configuration Guide).
Make sure the device you are adding to the IRF fabric has sufficient storage space for the new software images.
If sufficient storage space is not available, the device automatically deletes the current software images. If the reclaimed space is still insufficient, the device cannot complete the auto-update. You must reboot the device, and then access the Bootware menu to delete files.
Procedure
1. Enter system view.
system-view
2. Enable software auto-update.
irf auto-update enable
By default, software auto-update is enabled.
Removing an expansion interface card that has IRF physical interfaces
To remove an expansion interface card that provides IRF physical interfaces:
1. Perform one of the following tasks to eliminate temporary packet loss:
¡ Remove cables from the IRF physical interfaces on the card.
¡ Shut down the IRF physical interfaces on the card by using the shutdown command.
2. Remove the card.
Replacing an expansion interface card that has IRF physical interfaces
Replacing the old card with a different model replacement card
1. Shut down the IRF physical interfaces on the old card by using the shutdown command.
2. Remove the IRF port bindings that contain the physical interfaces.
3. Remove the old card, and then install the replacement card.
4. Verify that the replacement card has been correctly installed by using the display device command.
5. Reconfigure the IRF port bindings, as described in "Binding physical interfaces to IRF ports."
6. Activate the IRF port settings by using the irf-port-configuration active command.
You can skip this step if the IRF port is in UP state when you add bindings.
Replacing the old card with the same model replacement card
1. Shut down the IRF physical interfaces on the old card by using the shutdown command.
2. Remove the old card, and then install the replacement card.
3. Verify that the replacement card has been correctly installed by using the display device command.
Bring up the physical interfaces by using the undo shutdown command after the interface card completes startup.
Display and maintenance commands for IRF
Execute display commands in any view.
|
Task |
Command |
|
Display information about all IRF members. |
display irf |
|
Display the IRF fabric topology. |
display irf topology |
|
Display IRF link information. |
display irf link |
|
Display IRF configuration. |
display irf configuration |
|
Display the load sharing mode for IRF links. |
display irf-port load-sharing mode [ irf-port [ member-id/irf-port-number ] ] |
|
Display MAD configuration. |
display mad [ verbose ] |
IRF configuration examples
The IRF configuration examples show how to set up IRF fabrics that use different MAD mechanisms.
Example: Configuring an LACP MAD-enabled IRF fabric
Network configuration
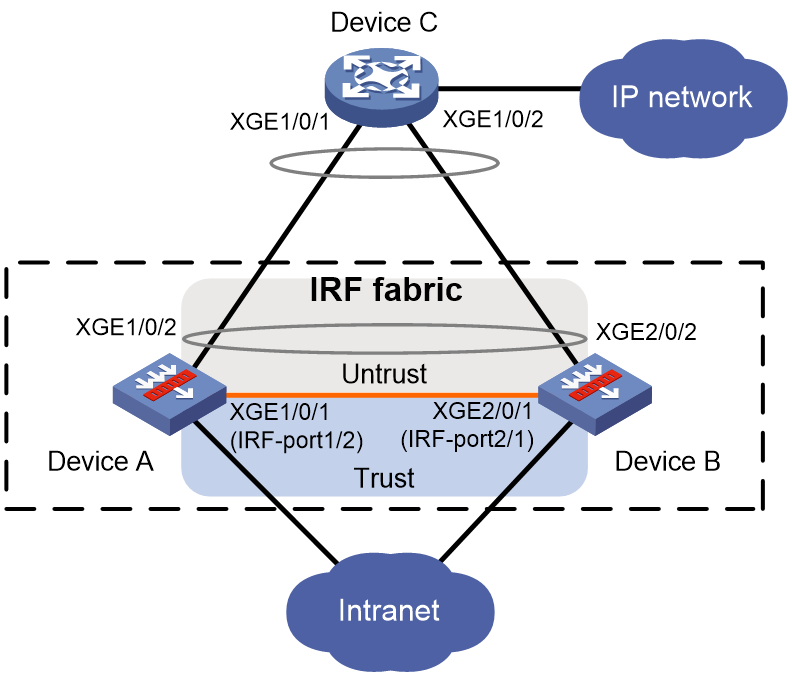
As shown in Figure 14, set up a two-member IRF fabric at the access layer of the network.
Configure LACP MAD on the multimember aggregation to Device C, which supports extended LACP.
Procedure
1. Configure Device A:
# Change the member priority of the device to 32.
<DeviceA> system-view
[DeviceA] irf member 1 priority 32
# Bind Ten-GigabitEthernet 1/0/1 to IRF port 1/2, and save the configuration.
[DeviceA] interface ten-gigabitethernet 1/0/1
[DeviceA-Ten-GigabitEthernet1/0/1] shutdown
[DeviceA-Ten-GigabitEthernet1/0/1] quit
[DeviceA] irf-port 1/2
[DeviceA-irf-port1/2] port group interface ten-gigabitethernet 1/0/1
[DeviceA-irf-port1/2] quit
[DeviceA] interface ten-gigabitethernet 1/0/1
[DeviceA-Ten-GigabitEthernet1/0/1] undo shutdown
[DeviceA-Ten-GigabitEthernet1/0/1] quit
[DeviceA] save
# Activate the IRF port configuration.
[DeviceA] irf-port-configuration active
2. Configure Device B:
# Change the member ID of Device B to 2, and reboot the device to have the change take effect.
<DeviceB> system-view
[DeviceB] irf member 1 renumber 2
Warning: Renumbering the device number may result in configuration change or loss. Continue? [Y/N]:y
[DeviceB] quit
<DeviceB> reboot
# Connect Device B to Device A, as shown in Figure 14.
# Log in to Device B. (Details not shown.)
# Bind Ten-GigabitEthernet 2/0/1 to IRF port 2/1, and save the configuration.
<DeviceB> system-view
[DeviceB] interface ten-gigabitethernet 2/0/1
[DeviceB-Ten-GigabitEthernet2/0/1] shutdown
[DeviceB-Ten-GigabitEthernet2/0/1] quit
[DeviceB] irf-port 2/1
[DeviceB-irf-port2/1] port group interface ten-gigabitethernet 2/0/1
[DeviceB-irf-port2/1] quit
[DeviceB] interface ten-gigabitethernet 2/0/1
[DeviceB-Ten-GigabitEthernet2/0/1] undo shutdown
[DeviceB-Ten-GigabitEthernet2/0/1] quit
[DeviceB] save
# Activate the IRF port configuration.
[DeviceB] irf-port-configuration active
The two devices perform master election, and the one that has lost the election reboots to form an IRF fabric with the master. In this example, Device B reboots.
3. Re-log in to the IRF fabric. (Details not shown.)
4. Configure LACP MAD on the IRF fabric:
# Set the domain ID of the IRF fabric to 1.
[DeviceA] irf domain 1
# Create a dynamic aggregate interface, assign it an IP address, and enable LACP MAD.
[DeviceA] interface route-aggregation 2
[DeviceA-Route-Aggregation2] ip address 192.168.1.1 24
[DeviceA-Route-Aggregation2] link-aggregation mode dynamic
[DeviceA-Route-Aggregation2] mad enable
You need to assign a domain ID (range: 0-4294967295)
[Current domain is: 1]:
The assigned domain ID is: 1
MAD LACP only enable on dynamic aggregation interface.
[DeviceA-Route-Aggregation2] quit
# Assign Ten-GigabitEthernet 1/0/2 and Ten-GigabitEthernet 2/0/2 to the aggregate interface.
[DeviceA] interface ten-gigabitethernet 1/0/2
[DeviceA-Ten-GigabitEthernet1/0/2] port link-aggregation group 2
[DeviceA-Ten-GigabitEthernet1/0/2] quit
[DeviceA] interface ten-gigabitethernet 2/0/2
[DeviceA-Ten-GigabitEthernet2/0/2] port link-aggregation group 2
[DeviceA-Ten-GigabitEthernet2/0/2] quit
5. Configure security zones and an inter-zone security policy to make sure the IRF fabric and Device C can communicate with each other:
# Add the interfaces between the IRF fabric and Device C to security zone Untrust.
[DeviceA] security-zone name Untrust
[DeviceA-security-zone-Untrust] import interface ten-gigabitethernet 1/0/2
[DeviceA-security-zone-Untrust] import interface ten-gigabitethernet 2/0/2
[DeviceA-security-zone-Untrust] quit
# Add a security policy and configure a rule to permit the traffic from the IRF fabric (in the default local security zone) to security zone Untrust. This rule allows the IRF fabric to send traffic to Device C.
[DeviceA] security-policy ip
[DeviceA-security-policy-ip] rule name irflocalout
[DeviceA-security-policy-ip-1-irflocalout] source-zone local
[DeviceA-security-policy-ip-1-irflocalout] destination-zone Untrust
[DeviceA-security-policy-ip-1-irflocalout] action pass
[DeviceA-security-policy-ip-1-irflocalout] quit
[DeviceA-security-policy-ip] quit
# Configure a rule in the security policy to permit the traffic from security zone Untrust to the IRF fabric. This rule allows the IRF fabric to receive traffic from Device C.
[DeviceA] security-policy ip
[DeviceA-security-policy-ip] rule name irflocalin
[DeviceA-security-policy-ip-2-irflocalin] source-zone Untrust
[DeviceA-security-policy-ip-2-irflocalin] destination-zone local
[DeviceA-security-policy-ip-2-irflocalin] action pass
[DeviceA-security-policy-ip-2-irflocalin] quit
[DeviceA-security-policy-ip] quit
6. Configure Device C as the intermediate device:
|
CAUTION: If the intermediate device is also an IRF fabric, assign the two IRF fabrics different domain IDs for correct split detection. False detection causes IRF split. |
# Create a dynamic aggregate interface and assign an IP address to it.
<DeviceC> system-view
[DeviceC] interface route-aggregation 2
[DeviceC-Route-Aggregation2] link-aggregation mode dynamic
[DeviceC-Route-Aggregation2] ip address 192.168.1.2 24
[DeviceC-Route-Aggregation2] quit
# Assign Ten-GigabitEthernet 1/0/1 and Ten-GigabitEthernet 1/0/2 to the aggregate interface.
[DeviceC] interface ten-gigabitethernet 1/0/1
[DeviceC-Ten-GigabitEthernet1/0/1] port link-aggregation group 2
[DeviceC-Ten-GigabitEthernet1/0/1] quit
[DeviceC] interface ten-gigabitethernet 1/0/2
[DeviceC-Ten-GigabitEthernet1/0/2] port link-aggregation group 2
[DeviceC-Ten-GigabitEthernet1/0/2] quit
Verifying the configuration
# Display IRF fabric information to verify that the IRF fabric has been set up and Device A is the master.
[DeviceA] display irf
MemberID Role Priority CPU-Mac Description
*+1 Master 32 487a-da95-93b5 ---
2 Standby 1 3897-d6a8-1b1a ---
--------------------------------------------------
* indicates the device is the master.
+ indicates the device through which the user logs in.
The bridge MAC of the IRF is: 487a-da95-93b3
Auto upgrade : yes
Mac persistent : no
Domain ID : 1
# Display detailed MAD information to verify that LACP MAD is operating correctly.
[DeviceA] display mad verbose
Multi-active recovery state: No
Excluded ports (user-configured):
Excluded ports (system-configured):
Ten-GigabitEthernet1/0/1
Ten-GigabitEthernet2/0/1
MAD ARP disabled.
MAD ND disabled.
MAD LACP enabled interface: Route-Aggregation2
MAD status : Normal
Member ID Port MAD status
1 Ten-GigabitEthernet1/0/2 Normal
2 Ten-GigabitEthernet2/0/2 Normal
MAD BFD disabled.
# Split the IRF fabric and verify that LACP MAD state changes to Faulty.
[DeviceA] display mad verbose
Multi-active recovery state: No
Excluded ports (user-configured):
Excluded ports (system-configured):
Ten-GigabitEthernet1/0/1
MAD ARP disabled.
MAD ND disabled.
MAD LACP enabled interface: Route-Aggregation2
MAD status : Faulty
Member ID Port MAD status
1 Ten-GigabitEthernet1/0/2 Faulty
MAD BFD disabled.
# Verify that all network interfaces on Device B except for the IRF physical interface are shut down. (Details not shown.)
Configuring a BFD MAD-enabled IRF fabric
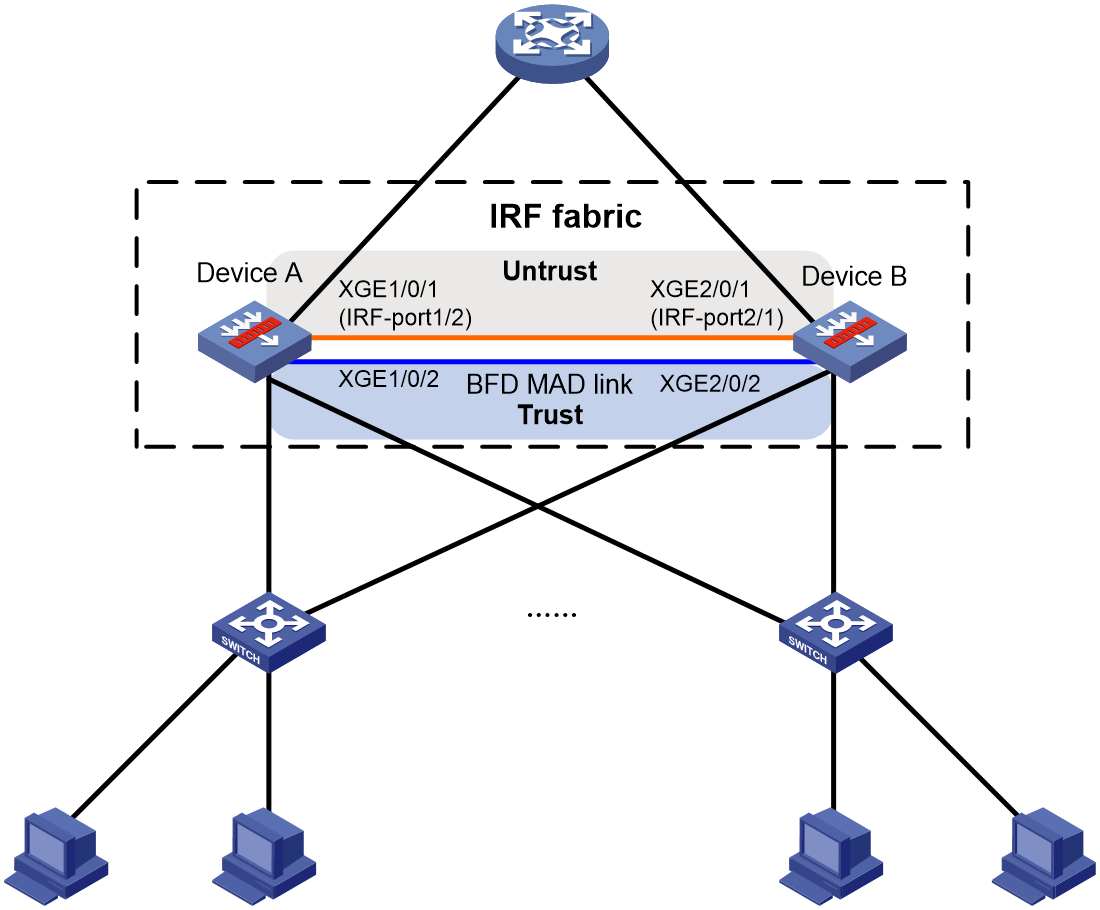
Network configuration
As shown in Figure 15, set up an IRF fabric at the distribution layer of the enterprise network. Configure BFD MAD in the IRF fabric and set up BFD MAD links between the member devices.
Procedure
1. Configure Device A:
# Change the member priority of the device to 32.
<DeviceA> system-view
[DeviceA] irf member 1 priority 32
# Bind Ten-GigabitEthernet 1/0/1 to IRF port 1/2, and save the configuration.
[DeviceA] interface ten-gigabitethernet 1/0/1
[DeviceA-Ten-GigabitEthernet1/0/1] shutdown
[DeviceA-Ten-GigabitEthernet1/0/1] quit
[DeviceA] irf-port 1/2
[DeviceA-irf-port1/2] port group interface ten-gigabitethernet 1/0/1
[DeviceA-irf-port1/2] quit
[DeviceA] interface ten-gigabitethernet 1/0/1
[DeviceA-Ten-GigabitEthernet1/0/1] undo shutdown
[DeviceA-Ten-GigabitEthernet1/0/1] quit
[DeviceA] save
# Activate the IRF port configuration.
[DeviceA] irf-port-configuration active
2. Configure Device B:
# Change the member ID of Device B to 2, and reboot the device to have the change take effect.
<DeviceB> system-view
[DeviceB] irf member 1 renumber 2
Warning: Renumbering the device number may result in configuration change or loss. Continue? [Y/N]:y
[DeviceB] quit
<DeviceB> reboot
# Connect Device B to Device A, as shown in Figure 15.
# Log in to Device B. (Details not shown.)
# Bind Ten-GigabitEthernet 2/0/1 to IRF port 2/1 and save the configuration.
<DeviceB> system-view
[DeviceB] interface ten-gigabitethernet 2/0/1
[DeviceB-Ten-GigabitEthernet2/0/1] shutdown
[DeviceB-Ten-GigabitEthernet2/0/1] quit
[DeviceB] irf-port 2/1
[DeviceB-irf-port2/1] port group interface ten-gigabitethernet 2/0/1
[DeviceB-irf-port2/1] quit
[DeviceB] interface ten-gigabitethernet 2/0/1
[DeviceB-Ten-GigabitEthernet2/0/1] undo shutdown
[DeviceB-Ten-GigabitEthernet2/0/1] quit
[DeviceB] save
# Activate the IRF port configuration.
[DeviceB] irf-port-configuration active
The two devices perform master election, and the one that has lost the election reboots to form an IRF fabric with the master. In this example, Device B reboots.
3. Configure BFD MAD:
# Create Layer 3 aggregate interface 3.
[DeviceA] interface route-aggregation 3
[DeviceA-Route-Aggregation3] quit
# Assign Ten-GigabitEthernet 1/0/2 on Device A and Ten-GigabitEthernet 2/0/2 on Device B to aggregation group 3.
[DeviceA] interface ten-gigabitethernet 1/0/2
[DeviceA-Ten-GigabitEthernet1/0/2] port link-aggregation group 3
[DeviceA-Ten-GigabitEthernet1/0/2] quit
[DeviceA] interface ten-gigabitethernet 2/0/2
[DeviceA-Ten-GigabitEthernet2/0/2] port link-aggregation group 3
[DeviceA-Ten-GigabitEthernet2/0/2] quit
# Enable BFD MAD on Layer 3 aggregate interface 3 and assign a MAD IP address to each member device on the aggregate interface.
[DeviceA] interface route-aggregation 3
[DeviceA-Route-Aggregation3] mad bfd enable
[DeviceA-Route-Aggregation3] mad ip address 192.168.2.1 24 member 1
[DeviceA-Route-Aggregation3] mad ip address 192.168.2.2 24 member 2
[DeviceA-Route-Aggregation3] quit
4. Configure security zones and an inter-zone policy to make sure the IRF member devices can sent and receive MAD packets to and from each other over the BFD MAD links:
# Add Layer 3 aggregate interface 3 to security zone Trust.
[DeviceA] security-zone name Trust
[DeviceA-security-zone-Trust] import interface route-aggregation 3
[DeviceA-security-zone-Trust] quit
# Add a security policy and configure a rule to permit the traffic from the IRF fabric (in the default local security zone) to security zone Trust. This rule allows the IRF member devices to send out traffic over the BFD MAD links.
[DeviceA] security-policy ip
[DeviceA-security-policy-ip] rule name irflocalout
[DeviceA-security-policy-ip-1-irflocalout] source-zone local
[DeviceA-security-policy-ip-1-irflocalout] destination-zone Trust
[DeviceA-security-policy-ip-1-irflocalout] action pass
[DeviceA-security-policy-ip-1-irflocalout] quit
[DeviceA-security-policy-ip] quit
# Configure a rule in the security policy to permit the traffic from security zone Trust to the IRF fabric. This rule allows the IRF member devices to receive traffic from the BFD MAD links.
[DeviceA] security-policy ip
[DeviceA-security-policy-ip] rule name irflocalin
[DeviceA-security-policy-ip-2-irflocalin] source-zone Trust
[DeviceA-security-policy-ip-2-irflocalin] destination-zone local
[DeviceA-security-policy-ip-2-irflocalin] action pass
[DeviceA-security-policy-ip-2-irflocalin] quit
[DeviceA-security-policy-ip] quit
Verifying the configuration
# Display IRF fabric information to verify that the IRF fabric has been set up and Device A is the master.
[DeviceA] display irf
MemberID Role Priority CPU-Mac Description
*+1 Master 32 487a-da95-93b5 ---
2 Standby 1 3897-d6a8-1b1a ---
--------------------------------------------------
* indicates the device is the master.
+ indicates the device through which the user logs in.
The bridge MAC of the IRF is: 487a-da95-93b3
Auto upgrade : yes
Mac persistent : no
Domain ID : 0
# Display detailed MAD information to verify that BFD MAD is operating correctly.
[DeviceA] display mad verbose
Multi-active recovery state: No
Excluded ports (user-configured):
Excluded ports (system-configured):
Ten-GigabitEthernet1/0/1
Ten-GigabitEthernet2/0/1
MAD ARP disabled.
MAD ND disabled.
MAD LACP disabled.
MAD BFD enabled interface: Route-Aggregation3
MAD status : Normal
Member ID MAD IP address Neighbor MAD status
1 192.168.2.1/24 2 Normal
2 192.168.2.2/24 1 Normal
# Split the IRF fabric and verify that BFD MAD state changes to Faulty.
[DeviceA] display mad verbose
Excluded ports (user-configured):
Excluded ports (system-configured):
Ten-GigabitEthernet1/0/1
MAD ARP disabled.
MAD ND disabled.
MAD LACP disabled.
MAD BFD enabled interface: Route-Aggregation3
MAD status : Faulty
Member ID MAD IP address Neighbor MAD status
1 192.168.2.1/24 2 Faulty
# Verify that all network interfaces on Device B except for the IRF physical interface are shut down. (Details not shown.)
Configuring an ARP MAD-enabled IRF fabric
Network configuration
As shown in Figure 16, set up an IRF fabric in the enterprise network.
· Configure ARP MAD in the IRF fabric and use the links connected to Device C to transmit ARP MAD packets.
· To prevent loops, run the spanning tree feature between Device C and the IRF fabric.
Procedure
1. Configure Device A:
# Change the member priority of the device to 32.
<DeviceA> system-view
[DeviceA] irf member 1 priority 32
# Bind Ten-GigabitEthernet 1/0/1 to IRF port 1/2, and save the configuration.
<DeviceA> system-view
[DeviceA] interface ten-gigabitethernet 1/0/1
[DeviceA-Ten-GigabitEthernet1/0/1] shutdown
[DeviceA-Ten-GigabitEthernet1/0/1] quit
[DeviceA] irf-port 1/2
[DeviceA-irf-port1/2] port group interface ten-gigabitethernet 1/0/1
[DeviceA-irf-port1/2] quit
[DeviceA] interface ten-gigabitethernet 1/0/1
[DeviceA-Ten-GigabitEthernet1/0/1] undo shutdown
[DeviceA-Ten-GigabitEthernet1/0/1] quit
[DeviceA] save
# Activate the IRF port configuration.
[DeviceA] irf-port-configuration active
2. Configure Device B:
# Assign IP addresses to interfaces and configure routes, security zones, zone pairs, and interzone policies. Make sure the network connections are available. (Details not shown.)
# Change the member ID of Device B to 2, and reboot the device to have the change take effect.
<DeviceB> system-view
[DeviceB] irf member 1 renumber 2
Warning: Renumbering the device number may result in configuration change or loss. Continue? [Y/N]:y
[DeviceB] quit
<DeviceB> reboot
# Connect Device B to Device A, as shown in Figure 16.
# Log in to Device B. (Details not shown.)
# Bind Ten-GigabitEthernet 2/0/1 to IRF port 2/1 and save the configuration.
<DeviceB> system-view
[DeviceB] interface ten-gigabitethernet 2/0/1
[DeviceB-Ten-GigabitEthernet2/0/1] shutdown
[DeviceB-Ten-GigabitEthernet2/0/1] quit
[DeviceB] irf-port 2/1
[DeviceB-irf-port2/1] port group interface ten-gigabitethernet 2/0/1
[DeviceB-irf-port2/1] quit
[DeviceB] interface ten-gigabitethernet 2/0/1
[DeviceB-Ten-GigabitEthernet2/0/1] undo shutdown
[DeviceB-Ten-GigabitEthernet2/0/1] quit
[DeviceB] save
# Activate the IRF port configuration.
[DeviceB] irf-port-configuration active
The two devices perform master election, and the one that has lost the election reboots to form an IRF fabric with the master. In this example, Device B reboots.
3. Configure ARP MAD on the IRF fabric:
# Enable the spanning tree feature globally, and map the ARP MAD VLAN to MSTI 1 in the MST region.
[DeviceA] stp global enable
[DeviceA] stp region-configuration
[DeviceA-mst-region] region-name arpmad
[DeviceA-mst-region] instance 1 vlan 3
[DeviceA-mst-region] active region-configuration
[DeviceA-mst-region] quit
# Configure the IRF fabric to change its bridge MAC address as soon as the address owner leaves.
[DeviceA] undo irf mac-address persistent
# Set the domain ID of the IRF fabric to 1.
[DeviceA] irf domain 1
# Create VLAN 3, and add Ten-GigabitEthernet 1/0/2 on Device A and Ten-GigabitEthernet 2/0/2 on Device B to VLAN 3.
[DeviceA] vlan 3
[DeviceA-vlan3] quit
[DeviceA] interface ten-gigabitethernet 1/0/2
[DeviceA-Ten-GigabitEthernet1/0/2] port link-mode bridge
[DeviceA-Ten-GigabitEthernet1/0/2] port access vlan 3
[DeviceA-Ten-GigabitEthernet1/0/2] quit
[DeviceA] interface ten-gigabitethernet 2/0/2
[DeviceA-Ten-GigabitEthernet2/0/2] port link-mode bridge
[DeviceA-Ten-GigabitEthernet2/0/2] port access vlan 3
[DeviceA-Ten-GigabitEthernet2/0/2] quit
# Create VLAN-interface 3, assign it an IP address, and enable ARP MAD on the interface.
[DeviceA] interface vlan-interface 3
[DeviceA-Vlan-interface3] ip address 192.168.2.1 24
[DeviceA-Vlan-interface3] mad arp enable
You need to assign a domain ID (range: 0-4294967295)
[Current domain is: 1]:
The assigned domain ID is: 1
4. Configure security zones and an inter-zone security policy to make sure the IRF fabric and Device C can communicate with each other.
# Add the interfaces between the IRF fabric and Device C in VLAN 3 to security zone Untrust.
[DeviceA] security-zone name Untrust
[DeviceA-security-zone-Untrust] import interface ten-gigabitethernet 1/0/2 vlan 3
[DeviceA-security-zone-Untrust] import interface ten-gigabitethernet 2/0/2 vlan 3
[DeviceA-security-zone-Untrust] quit
# Add a security policy and configure a rule to permit the traffic from the IRF fabric (in the default local security zone) to security zone Untrust. This rule allows the IRF member devices to send out traffic to Device C in VLAN 3.
[DeviceA] security-policy ip
[DeviceA-security-policy-ip] rule name irflocalout
[DeviceA-security-policy-ip-1-irflocalout] source-zone local
[DeviceA-security-policy-ip-1-irflocalout] destination-zone Untrust
[DeviceA-security-policy-ip-1-irflocalout] action pass
[DeviceA-security-policy-ip-1-irflocalout] quit
[DeviceA-security-policy-ip] quit
# Configure a rule in the security policy to permit the traffic from security zone Untrust to the IRF fabric. This rule allows the IRF fabric to receive traffic in VLAN 3 from Device C.
[DeviceA] security-policy ip
[DeviceA-security-policy-ip] rule name irflocalin
[DeviceA-security-policy-ip-2-irflocalin] source-zone Untrust
[DeviceA-security-policy-ip-2-irflocalin] destination-zone local
[DeviceA-security-policy-ip-2-irflocalin] action pass
[DeviceA-security-policy-ip-2-irflocalin] quit
[DeviceA-security-policy-ip] quit
5. Configure Device C as the intermediate device:
|
CAUTION: If the intermediate device is also an IRF fabric, assign the two IRF fabrics different domain IDs for correct split detection. False detection causes IRF split. |
# Enable the spanning tree feature globally, and map the ARP MAD VLAN to MSTI 1 in the MST region.
<DeviceC> system-view
[DeviceC] stp global enable
[DeviceC] stp region-configuration
[DeviceC-mst-region] region-name arpmad
[DeviceC-mst-region] instance 1 vlan 3
[DeviceC-mst-region] active region-configuration
[DeviceC-mst-region] quit
# Create VLAN 3, and add ports Ten-GigabitEthernet 1/0/1 and Ten-GigabitEthernet 1/0/2 to VLAN 3 to forward ARP MAD packets.
[DeviceC] vlan 3
[DeviceC-vlan3] port ten-gigabitethernet 1/0/1 ten-gigabitethernet 1/0/2
[DeviceC-vlan3] quit
Verifying the configuration
# Display IRF fabric information to verify that the IRF fabric has been set up and Device A is the master.
[DeviceA] display irf
MemberID Role Priority CPU-Mac Description
*+1 Master 32 487a-da95-93b5 ---
2 Standby 1 3897-d6a8-1b1a ---
--------------------------------------------------
* indicates the device is the master.
+ indicates the device through which the user logs in.
The bridge MAC of the IRF is: 487a-da95-93b3
Auto upgrade : yes
Mac persistent : no
Domain ID : 1
# Display detailed MAD information to verify ARP MAD configuration.
[DeviceA] display mad verbose
Multi-active recovery state: No
Excluded ports (user-configured):
Excluded ports (system-configured):
Ten-GigabitEthernet1/0/1
Ten-GigabitEthernet2/0/1
MAD ARP enabled interface:
Vlan-interface3
MAD ND disabled.
MAD LACP disabled.
MAD BFD disabled.
# Split the IRF fabric and verify that the IRF physical interface on Device B is not displayed as a port excluded from the MAD shutdown action.
[DeviceA] display mad verbose
Multi-active recovery state: No
Excluded ports (user-configured):
Excluded ports (system-configured):
Ten-GigabitEthernet1/0/1
MAD ARP enabled interface:
Vlan-interface3
MAD ND disabled.
MAD LACP disabled.
MAD BFD disabled.
# Verify that all network interfaces on Device B except for the IRF physical interface are shut down. (Details not shown.)
Configuring an ND MAD-enabled IRF fabric
Network configuration
As shown in Figure 17, set up an IRF fabric in the IPv6 enterprise network.
· Configure ND MAD in the IRF fabric and use the links connected to Device C for transmitting ND MAD packets.
· To prevent loops, run the spanning tree feature between Device C and the IRF fabric.
Procedure
1. Configure Device A:
# Change the member priority of the device to 32.
<DeviceA> system-view
[DeviceA] irf member 1 priority 32
# Bind Ten-GigabitEthernet 1/0/1 to IRF port 1/2 and save the configuration.
[DeviceA] interface ten-gigabitethernet 1/0/1
[DeviceA-Ten-GigabitEthernet1/0/1] shutdown
[DeviceA-Ten-GigabitEthernet1/0/1] quit
[DeviceA] irf-port 1/2
[DeviceA-irf-port1/2] port group interface ten-gigabitethernet 1/0/1
[DeviceA-irf-port1/2] quit
[DeviceA] interface ten-gigabitethernet 1/0/1
[DeviceA-Ten-GigabitEthernet1/0/1] undo shutdown
[DeviceA-Ten-GigabitEthernet1/0/1] quit
[DeviceA] save
# Activate the IRF port configuration.
[DeviceA] irf-port-configuration active
2. Configure Device B:
# Assign IP addresses to interfaces and configure routes, security zones, zone pairs, and interzone policies. Make sure the network connections are available. (Details not shown.)
# Change the member ID of Device B to 2, and reboot the device to have the change take effect.
<DeviceB> system-view
[DeviceB] irf member 1 renumber 2
Warning: Renumbering the member ID may result in configuration change or loss. Continue? [Y/N]:y
[DeviceB] quit
<DeviceB> reboot
# Connect Device B to Device A, as shown in Figure 17.
# Log in to Device B. (Details not shown.)
# Bind Ten-GigabitEthernet 2/0/1 to IRF port 2/1, and save the configuration.
<DeviceB> system-view
[DeviceB] interface ten-gigabitethernet 2/0/1
[DeviceB-Ten-GigabitEthernet2/0/1] shutdown
[DeviceB-Ten-GigabitEthernet2/0/1] quit
[DeviceB] irf-port 2/1
[DeviceB-irf-port2/1] port group interface ten-gigabitethernet 2/0/1
[DeviceB-irf-port2/1] quit
[DeviceB] interface ten-gigabitethernet 2/0/1
[DeviceB-Ten-GigabitEthernet2/0/1] undo shutdown
[DeviceB-Ten-GigabitEthernet2/0/1] quit
[DeviceB] save
# Activate the IRF port configuration.
[DeviceB] irf-port-configuration active
The two devices perform master election, and the one that has lost the election reboots to form an IRF fabric with the master. In this example, Device B reboots.
3. Configure ND MAD on the IRF fabric:
# Enable the spanning tree feature globally, and map the ND MAD VLAN to MSTI 1 in the MST region.
[DeviceA] stp global enable
[DeviceA] stp region-configuration
[DeviceA-mst-region] region-name ndmad
[DeviceA-mst-region] instance 1 vlan 3
[DeviceA-mst-region] active region-configuration
[DeviceA-mst-region] quit
# Configure the IRF fabric to change its bridge MAC address as soon as the address owner leaves.
[DeviceA] undo irf mac-address persistent
# Set the domain ID of the IRF fabric to 1.
[DeviceA] irf domain 1
# Create VLAN 3, and add Ten-GigabitEthernet 1/0/2 on Device A and Ten-GigabitEthernet 2/0/2 on Device B to VLAN 3.
[DeviceA] vlan 3
[DeviceA-vlan3] quit
[DeviceA] interface ten-gigabitethernet 1/0/2
[DeviceA-Ten-GigabitEthernet1/0/2] port link-mode bridge
[DeviceA-Ten-GigabitEthernet1/0/2] port access vlan 3
[DeviceA-Ten-GigabitEthernet1/0/2] quit
[DeviceA] interface ten-gigabitethernet 2/0/2
[DeviceA-Ten-GigabitEthernet2/0/2] port link-mode bridge
[DeviceA-Ten-GigabitEthernet2/0/2] port access vlan 3
[DeviceA-Ten-GigabitEthernet2/0/2] quit
# Create VLAN-interface 3, assign it an IPv6 address, and enable ND MAD on the interface.
[DeviceA] interface vlan-interface 3
[DeviceA-Vlan-interface3] ipv6 address 2001::1 64
[DeviceA-Vlan-interface3] mad nd enable
You need to assign a domain ID (range: 0-4294967295)
[Current domain is: 1]:
The assigned domain ID is: 1
4. Configure security zones and an inter-zone security policy to make sure the IRF fabric and Device C can communicate with each other.
# Add the interfaces between the IRF fabric and Device C in VLAN 3 to security zone Untrust.
[DeviceA] security-zone name Untrust
[DeviceA-security-zone-Untrust] import interface ten-gigabitethernet 1/0/2 vlan 3
[DeviceA-security-zone-Untrust] import interface ten-gigabitethernet 2/0/2 vlan 3
[DeviceA-security-zone-Untrust] quit
# Add a security policy and configure a rule to permit the traffic from the IRF fabric (in the default local security zone) to security zone Untrust. This rule allows the IRF member devices to send out traffic to Device C in VLAN 3.
[DeviceA] security-policy ip
[DeviceA-security-policy-ip] rule name irflocalout
[DeviceA-security-policy-ip-1-irflocalout] source-zone local
[DeviceA-security-policy-ip-1-irflocalout] destination-zone Untrust
[DeviceA-security-policy-ip-1-irflocalout] action pass
[DeviceA-security-policy-ip-1-irflocalout] quit
[DeviceA-security-policy-ip] quit
# Configure a rule in the security policy to permit the traffic from security zone Untrust to the IRF fabric. This rule allows the IRF fabric to receive traffic in VLAN 3 from Device C.
[DeviceA] security-policy ip
[DeviceA-security-policy-ip] rule name irflocalin
[DeviceA-security-policy-ip-2-irflocalin] source-zone Untrust
[DeviceA-security-policy-ip-2-irflocalin] destination-zone local
[DeviceA-security-policy-ip-2-irflocalin] action pass
[DeviceA-security-policy-ip-2-irflocalin] quit
[DeviceA-security-policy-ip] quit
5. Configure Device C as the intermediate device:
|
CAUTION: If the intermediate device is also an IRF fabric, assign the two IRF fabrics different domain IDs for correct split detection. False detection causes IRF split. |
# Enable the spanning tree feature globally, and map the ND MAD VLAN to MSTI 1 in the MST region.
<DeviceC> system-view
[DeviceC] stp global enable
[DeviceC] stp region-configuration
[DeviceC-mst-region] region-name ndmad
[DeviceC-mst-region] instance 1 vlan 3
[DeviceC-mst-region] active region-configuration
[DeviceC-mst-region] quit
# Create VLAN 3, and add Ten-GigabitEthernet 1/0/1 and Ten-GigabitEthernet 1/0/2 to VLAN 3 to forward ND MAD packets.
[DeviceC] vlan 3
[DeviceC-vlan3] port ten-gigabitethernet 1/0/1 ten-gigabitethernet 1/0/2
[DeviceC-vlan3] quit
Verifying the configuration
# Display IRF fabric information to verify that the IRF fabric has been set up and Device A is the master.
[DeviceA] display irf
MemberID Role Priority CPU-Mac Description
*+1 Master 32 487a-da95-93b5 ---
2 Standby 1 3897-d6a8-1b1a ---
--------------------------------------------------
* indicates the device is the master.
+ indicates the device through which the user logs in.
The bridge MAC of the IRF is: 487a-da95-93b3
Auto upgrade : yes
Mac persistent : no
Domain ID : 1
# Display detailed MAD information to verify ND MAD configuration.
[DeviceA] display mad verbose
Multi-active recovery state: No
Excluded ports (user-configured):
Excluded ports (system-configured):
Ten-GigabitEthernet1/0/1
Ten-GigabitEthernet2/0/1
MAD ARP disabled.
MAD ND enabled interface:
Vlan-interface3
MAD LACP disabled.
MAD BFD disabled.
# Split the IRF fabric and verify that the IRF physical interface on Device B is not displayed as a port excluded from the MAD shutdown action.
[DeviceA] display mad verbose
Multi-active recovery state: No
Excluded ports (user-configured):
Excluded ports (system-configured):
Ten-GigabitEthernet1/0/1
MAD ARP disabled.
MAD ND enabled interface:
Vlan-interface3
MAD LACP disabled.
MAD BFD disabled.
# Verify that all network interfaces on Device B except for the IRF physical interface are shut down. (Details not shown.)
IRF hot backup configuration examples
Example: Configuring an IRF hot backup system in active/standby mode with one redundancy group
Network configuration
As shown in Figure 18, set up an IRF hot backup system at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the hot backup system to operate in active/standby mode.
· Configure Device A and Device B as the primary device and the secondary device, respectively.
Procedure
1. Configure IRF:
¡ Configure Device A:
# Bind GigabitEthernet 1/0/3 to IRF-port 1/2 and save the configuration.
<DeviceA> system-view
[DeviceA] interface gigabitethernet 1/0/3
[DeviceA-GigabitEthernet1/0/3] shutdown
[DeviceA-GigabitEthernet1/0/3] quit
[DeviceA] irf-port 1/2
[DeviceA-irf-port1/2] port group interface gigabitethernet 1/0/3
You must perform the following tasks for a successful IRF setup:
Save the configuration after completing IRF configuration.
Execute the "irf-port-configuration active" command to activate the IRF ports.
[DeviceA-irf-port1/2] quit
[DeviceA] interface gigabitethernet 1/0/3
[DeviceA-GigabitEthernet1/0/3] undo shutdown
[DeviceA-GigabitEthernet1/0/3] quit
[DeviceA] save
[DeviceA] irf-port-configuration active
# Change the member priority of Device A to 2 for it to be elected as the master.
[DeviceA] irf member 1 priority 2
# Activate the IRF port configuration.
[DeviceA] irf-port-configuration active
¡ Configure Device B:
# Change the member ID of Device B to 2, and reboot the device to have the change take effect.
<DeviceB> system-view
[DeviceB] irf member 1 renumber 2
Renumbering the member ID may result in configuration change or loss. Continue? [Y/N]:y
[DeviceB] quit
<DeviceB> reboot
# Connect Device B to Device A, as shown in Figure 18.
# Log in to Device B. (Details not shown.)
# Bind GigabitEthernet 2/0/3 to IRF port 2/1, and save the configuration.
<DeviceB> system-view
[DeviceB] interface gigabitethernet 2/0/3
[DeviceB-GigabitEthernet2/0/3] shutdown
[DeviceB-GigabitEthernet2/0/3] quit
[DeviceB] irf-port 2/1
[DeviceB-irf-port2/1] port group interface gigabitethernet 2/0/3
You must perform the following tasks for a successful IRF setup:
Save the configuration after completing IRF configuration.
Execute the "irf-port-configuration active" command to activate the IRF ports.
[DeviceB-irf-port2/1] quit
[DeviceB] interface gigabitethernet 2/0/3
[DeviceB-GigabitEthernet2/0/3] undo shutdown
[DeviceB-GigabitEthernet2/0/3] quit
[DeviceB] save
# Activate the IRF port configuration.
[DeviceB] irf-port-configuration active
The two devices perform master election, and the one that has lost the election reboots to form an IRF fabric with the master. In this example, Device B reboots.
2. Configure Track to monitor the status of the uplink and downlink interfaces of the IRF fabric.
<DeviceA> system-view
[DeviceA] track 1 interface gigabitethernet 1/0/1
[DeviceA-track-1] quit
[DeviceA] track 2 interface gigabitethernet 1/0/2
[DeviceA-track-2] quit
[DeviceA] track 3 interface gigabitethernet 2/0/1
[DeviceA-track-3] quit
[DeviceA] track 4 interface gigabitethernet 2/0/2
[DeviceA-track-4] quit
3. Configure Reth interfaces:
# Configure Reth 11.
[DeviceA] interface reth 11
[DeviceA-Reth11] member interface gigabitethernet 1/0/1 priority 100
[DeviceA-Reth11] member interface gigabitethernet 2/0/1 priority 80
[DeviceA-Reth11] ip address 51.1.1.2 255.255.255.0
[DeviceA-Reth11] quit
# Configure Reth 12.
[DeviceA] interface reth 12
[DeviceA-Reth12] member interface gigabitethernet 1/0/2 priority 100
[DeviceA-Reth12] member interface gigabitethernet 2/0/2 priority 80
[DeviceA-Reth12] ip address 52.1.1.2 255.255.255.0
[DeviceA-Reth12] quit
4. Configure a redundancy group:
# Create redundancy group a.
[DeviceA] redundancy group a
# Assign Reth 11 and Reth 12 to redundancy group a.
[DeviceA-redundancy-group-a] member interface reth 11
[DeviceA-redundancy-group-a] member interface reth 12
# Bind Node 1 to Device A, set the priority of the node to 20, and associate track entries 1 and 2 with the node.
[DeviceA-redundancy-group-a] node 1
[DeviceA-redundancy-group-a-node1] bind slot 1
[DeviceA-redundancy-group-a-node1] priority 20
[DeviceA-redundancy-group-a-node1] track 1 interface gigabitethernet 1/0/1
[DeviceA-redundancy-group-a-node1] track 2 interface gigabitethernet 1/0/2
[DeviceA-redundancy-group-a-node1] quit
# Bind Node 2 to Device B, set the priority of the node to 10, and associate track entries 3 and 4 with the node.
[DeviceA-redundancy-group-a] node 2
[DeviceA-redundancy-group-a-node2] bind slot 2
[DeviceA-redundancy-group-a-node2] priority 10
[DeviceA-redundancy-group-a-node2] track 3 interface gigabitethernet 2/0/1
[DeviceA-redundancy-group-a-node2] track 4 interface gigabitethernet 2/0/2
[DeviceA-redundancy-group-a-node2] quit
[DeviceA-redundancy-group-a] quit
5. Enable session synchronization.
[DeviceA] session synchronization enable
6. Enable session active/standby mode.
[DeviceA] undo session dual-active enable
7. Assign IP addresses to interfaces and configure routes, security zones, zone pairs, and interzone policies. Make sure the network connections are available. (Details not shown.)
8. Assign Reth 11 to security zone Untrust, and assign Reth 12 to security zone Trust. (Details not shown.)
9. Configure Switch A:
|
|
NOTE: The following information provides only the summary procedure to configure Switch A. |
¡ Create VLAN 10 and VLAN 11.
¡ Configure GigabitEthernet 1/0/1 and GigabitEthernet 1/0/2 to operate at Layer 2, and assign them to VLAN 11 as access interfaces.
¡ Configure GigabitEthernet 1/0/3 to operate at Layer 2, and assign it to VLAN 10 as an access interface.
¡ Assign 51.1.1.1/24 and 2.1.1.1/24 to VLAN-interface 11 and VLAN-interface 10, respectively.
¡ Specify 51.1.1.2 (IP address of Reth 11) as the next hop of the route to the internal network, and specify 2.1.1.2 (an IP address on the router) as the next hop of the route to the Internet.
10. Configure Switch B:
|
|
NOTE: The following information provides only the summary procedure to configure Switch B. |
¡ Create VLAN 12 and VLAN 20.
¡ Configure GigabitEthernet 1/0/1 and GigabitEthernet 1/0/2 to operate at Layer 2, and assign them to VLAN 12 as access interfaces.
¡ Configure GigabitEthernet 1/0/3 to operate at Layer 2, and assign it to VLAN 20 as an access interface.
¡ Assign 52.1.1.1/24 and 10.1.1.1/24 to VLAN-interface 12 and VLAN-interface 20.
¡ Specify 52.1.1.2 (IP address of Reth 12) as the next hop of the route to the Internet.
11. On the host, specify 10.1.1.1 (IP address of VLAN-interface 20 on Switch B) as the default gateway.
Verifying the configuration
# Verify that Device A is the high-priority node in the redundancy group and the member interfaces on both nodes are up when Device A and Device B are operating correctly.
[DeviceA] display redundancy group a
Redundancy group a (ID 1):
Node ID Slot Priority Status Track weight
1 Slot1 20 Primary 255
2 Slot2 10 Secondary 255
Preempt delay time remained : 0 min
Preempt delay timer setting : 60 min
Remaining hold-down time : 0 sec
Hold-down timer setting : 1 sec
Manual switchover request : No
Member interfaces:
Reth11 Reth12
Node 1:
Track info:
Track Status Reduced weight Interface
1 Positive 255 GE1/0/1
2 Positive 255 GE1/0/2
Node 2:
Track info:
Track Status Reduced weight Interface
3 Positive 255 GE2/0/1
4 Positive 255 GE2/0/2
# Shut down GigabitEthernet 1/0/2 on Device A and verify that Device B takes over to forward traffic.
[DeviceA] interface gigabitethernet 1/0/2
[DeviceA-GigabitEthernet1/0/2] shutdown
[DeviceA-GigabitEthernet1/0/2] display redundancy group a
Redundancy group a (ID 1):
Node ID Slot Priority Status Track weight
1 Slot1 20 Secondary -255
2 Slot2 10 Primary 255
Preempt delay time remained : 0 min
Preempt delay timer setting : 1 min
Remaining hold-down time : 0 sec
Hold-down timer setting : 1 sec
Manual switchover request : No
Member interfaces:
Reth11 Reth12
Node 1:
Track info:
Track Status Reduced weight Interface
1 Negative 255 GE1/0/1
2 Negative(Faulty) 255 GE1/0/2
Node 2:
Track info:
Track Status Reduced weight Interface
3 Positive 255 GE2/0/1
4 Positive 255 GE2/0/2
Example: Configuring an IRF hot backup system in dual-active mode with two redundancy groups
Network configuration
As shown in Figure 19, set up an IRF hot backup system at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the hot backup system to operate in dual-active mode.
· Configure Device A and Device B to process the traffic of Host A and Host B, respectively.
Procedure
1. Configure IRF as described in "Example: Configuring an IRF hot backup system in active/standby mode with one redundancy group."
2. Configure Layer 3 Ethernet subinterfaces to terminate the outermost VLAN ID of packets.
<DeviceA> system-view
[DeviceA] interface gigabitethernet 1/0/1.11
[DeviceA-GigabitEthernet1/0/1.11] vlan-type dot1q vid 11
[DeviceA] interface gigabitethernet 1/0/1.21
[DeviceA-GigabitEthernet1/0/1.21] vlan-type dot1q vid 21
[DeviceA] interface gigabitethernet 1/0/2.12
[DeviceA-GigabitEthernet1/0/2.12] vlan-type dot1q vid 12
[DeviceA] interface gigabitethernet 1/0/2.22
[DeviceA-GigabitEthernet1/0/2.22] vlan-type dot1q vid 22
[DeviceA] interface gigabitethernet 2/0/1.11
[DeviceA-GigabitEthernet2/0/1.11] vlan-type dot1q vid 11
[DeviceA] interface gigabitethernet 2/0/1.21
[DeviceA-GigabitEthernet2/0/1.21] vlan-type dot1q vid 21
[DeviceA] interface gigabitethernet 2/0/2.12
[DeviceA-GigabitEthernet2/0/2.12] vlan-type dot1q vid 12
[DeviceA] interface gigabitethernet 2/0/2.22
[DeviceA-GigabitEthernet2/0/2.22] vlan-type dot1q vid 22
[DeviceA-GigabitEthernet2/0/2.22] quit
3. Configure Track to monitor the status of the uplink and downlink subinterfaces of the IRF fabric.
[DeviceA] track 1 interface gigabitethernet 1/0/1.11
[DeviceA-track-1] quit
[DeviceA] track 2 interface gigabitethernet 1/0/1.21
[DeviceA-track-2] quit
[DeviceA] track 3 interface gigabitethernet 1/0/2.12
[DeviceA-track-3] quit
[DeviceA] track 4 interface gigabitethernet 1/0/2.22
[DeviceA-track-4] quit
[DeviceA] track 5 interface gigabitethernet 2/0/1.11
[DeviceA-track-5] quit
[DeviceA] track 6 interface gigabitethernet 2/0/1.21
[DeviceA-track-6] quit
[DeviceA] track 7 interface gigabitethernet 2/0/2.12
[DeviceA-track-7] quit
[DeviceA] track 8 interface gigabitethernet 2/0/2.22
[DeviceA-track-8] quit
4. Configure Reth interfaces:
# Configure Reth 11.
[DeviceA] interface reth 11
[DeviceA-Reth11] member interface gigabitethernet 1/0/1.11 priority 100
[DeviceA-Reth11] member interface gigabitethernet 2/0/1.11 priority 80
[DeviceA-Reth11] ip address 51.1.1.2 255.255.255.0
[DeviceA-Reth11] quit
# Configure Reth 12.
[DeviceA] interface reth 12
[DeviceA-Reth12] member interface gigabitethernet 1/0/2.12 priority 100
[DeviceA-Reth12] member interface gigabitethernet 2/0/2.12 priority 80
[DeviceA-Reth12] ip address 52.1.1.2 255.255.255.0
[DeviceA-Reth12] quit
# Configure Reth 21.
[DeviceA] interface reth 21
[DeviceA-Reth21] member interface gigabitethernet 1/0/1.21 priority 80
[DeviceA-Reth21] member interface gigabitethernet 2/0/1.21 priority 100
[DeviceA-Reth21] ip address 61.1.1.2 255.255.255.0
[DeviceA-Reth21] quit
# Configure Reth 22.
[DeviceA] interface reth 22
[DeviceA-Reth22] member interface gigabitethernet 1/0/2.22 priority 80
[DeviceA-Reth22] member interface gigabitethernet 2/0/2.22 priority 100
[DeviceA-Reth22] ip address 62.1.1.2 255.255.255.0
[DeviceA-Reth22] quit
5. Configure redundancy groups:
# Create redundancy group a.
[DeviceA] redundancy group a
# Assign Reth 11 and Reth 12 to redundancy group a.
[DeviceA-redundancy-group-a] member interface reth 11
[DeviceA-redundancy-group-a] member interface reth 12
# Bind Node 1 to Device A, set the priority of the node to 20, and associate track entries 1 and 3 with the node.
[DeviceA-redundancy-group-a] node 1
[DeviceA-redundancy-group-a-node1] bind slot 1
[DeviceA-redundancy-group-a-node1] priority 20
[DeviceA-redundancy-group-a-node1] track 1 interface gigabitethernet 1/0/1.11
[DeviceA-redundancy-group-a-node1] track 3 interface gigabitethernet 1/0/2.12
[DeviceA-redundancy-group-a-node1] quit
# Bind Node 2 to Device B, set the priority of the node to 10, and associate track entries 5 and 7 with the node.
[DeviceA-redundancy-group-a] node 2
[DeviceA-redundancy-group-a-node2] bind slot 2
[DeviceA-redundancy-group-a-node2] priority 10
[DeviceA-redundancy-group-a-node2] track 5 interface gigabitethernet 2/0/1.11
[DeviceA-redundancy-group-a-node2] track 7 interface gigabitethernet 2/0/2.12
[DeviceA-redundancy-group-a-node2] quit
[DeviceA-redundancy-group-a] quit
# Create redundancy group b.
[DeviceA] redundancy group b
# Assign Reth 21 and Reth 22 to redundancy group b.
[DeviceA-redundancy-group-b] member interface reth 21
[DeviceA-redundancy-group-b] member interface reth 22
# Bind Node 1 to Device A, set the priority of the node to 10, and associate track entries 2 and 4 with the node.
[DeviceA-redundancy-group-b] node 1
[DeviceA-redundancy-group-b-node1] bind slot 1
[DeviceA-redundancy-group-b-node1] priority 10
[DeviceA-redundancy-group-b-node1] track 2 interface gigabitethernet 1/0/1.21
[DeviceA-redundancy-group-b-node1] track 4 interface gigabitethernet 1/0/2.22
[DeviceA-redundancy-group-b-node1] quit
# Bind Node 2 to Device B, set the priority of the node to 20, and associate track entries 6 and 8 with the node.
[DeviceA-redundancy-group-b] node 2
[DeviceA-redundancy-group-b-node2] bind slot 2
[DeviceA-redundancy-group-b-node2] priority 20
[DeviceA-redundancy-group-b-node2] track 6 interface gigabitethernet 2/0/1.21
[DeviceA-redundancy-group-b-node2] track 8 interface gigabitethernet 2/0/2.22
[DeviceA-redundancy-group-b-node2] quit
[DeviceA-redundancy-group-b] quit
6. Enable session synchronization.
[DeviceA] session synchronization enable
7. Enable session dual-active mode.
[DeviceA] session dual-active enable
8. Assign IP addresses to interfaces and configure routes, security zones, zone pairs, and interzone policies. Make sure the network connections are available. (Details not shown.)
9. Assign Reth 11 and Reth 21 to security zone Untrust, and assign Reth 12 and Reth 22 to security zone Trust. (Details not shown.)
10. Configure the static routes to the external network. Specify the next hop of the route to 10.1.1.0/24 as 52.1.1.1(IP address of VLAN-interface 12 on Switch B). Specify the next hop of the route to 10.10.1.0/24 as 62.1.1.1 (IP address of VLAN-interface 22 on Switch B).
[DeviceA] ip route-static 10.1.1.0 24 52.1.1.1
[DeviceA] ip route-static 10.10.1.0 24 62.1.1.1
11. Configure PBR policies for the traffic sent from the internal network to reach the Internet.
# Configure ACL 2000 to permit the packets from 10.1.1.0/24.
[DeviceA] acl basic 2000
[DeviceA-acl-ipv4-basic-2000] rule 10 permit source 10.1.1.0 0.0.0.255
[DeviceA-acl-ipv4-basic-2000] quit
# Configure ACL 2001 to permit the packets from 10.10.1.0/24.
[DeviceA] acl basic 2001
[DeviceA-acl-ipv4-basic-2001] rule 10 permit source 10.10.1.0 0.0.0.255
[DeviceA-acl-ipv4-basic-2001] quit
# Configure PBR policy aaa to specify 51.1.1.1 (IP address of VLAN-interface 11 on Switch A) as the next hop for the packets from 10.1.1.0/24.
[DeviceA] policy-based-route aaa permit node 0
[DeviceA-pbr-aaa-0] if-match acl 2000
[DeviceA-pbr-aaa-0] apply next-hop 51.1.1.1
[DeviceA-pbr-aaa-0] quit
# Configure PBR policy bbb to specify 61.1.1.1 (IP address of VLAN-interface 21 on Switch B) as the next hop for the packets from 10.10.1.0/24.
[DeviceA] policy-based-route bbb permit node 0
[DeviceA-pbr-bbb-0] if-match acl 2001
[DeviceA-pbr-bbb-0] apply next-hop 61.1.1.1
[DeviceA-pbr-bbb-0] quit
# Apply PBR policy aaa to Reth 12 for Device A to forward the traffic sent from 10.1.1.0/24 to the Internet.
[DeviceA] interface reth 12
[DeviceA-Reth12] ip policy-based-route aaa
[DeviceA-Reth12] quit
# Apply PBR policy bbb to Reth 22 for Device B to forward the traffic sent from 10.10.1.0/24 to the Internet.
[DeviceA] interface reth 22
[DeviceA-Reth22] ip policy-based-route bbb
[DeviceA-Reth22] quit
12. Configure Switch A:
|
|
NOTE: The following information provides only the summary procedure to configure Switch A. |
a. Create VLAN 10, VLAN 11, and VLAN 21.
b. Configure GigabitEthernet 1/0/1 and GigabitEthernet 1/0/2 to operate at Layer 2, and assign them to VLAN 11 and VLAN 21 as trunk interfaces.
c. Configure GigabitEthernet 1/0/3 to operate at Layer 2, and assign it to VLAN 10 as an access interface.
d. Assign 51.1.1.1/24, 61.1.1.1/24, and 2.1.1.1/24 to VLAN-interface 11, VLAN-interface 21, and VLAN-interface 10, respectively.
e. Configure routes as follows:
- Specify 51.1.1.2 (IP address of Reth 11) as the next hop of the route to 10.1.1.0/24.
- Specify 61.1.1.2 (IP address of Reth 21) as the next hop of the route to 10.10.1.0/24.
- Specify 2.1.1.2 (IP address of the peer interface of VLAN-interface 10) as the next hop of the route to the Internet.
13. Configure Switch B:
|
|
NOTE: The following information provides only the summary procedure to configure Switch B. |
a. Create VLAN 12, VLAN 20, VLAN 22, and VLAN 30.
b. Configure GigabitEthernet 1/0/1 and GigabitEthernet 1/0/2 to operate at Layer 2, and assign them to VLAN 12 and VLAN 22 as trunk interfaces.
c. Configure GigabitEthernet 1/0/3 to operate at Layer 2, and assign it to VLAN 20 as an access interface.
d. Configure GigabitEthernet 1/0/4 to operate at Layer 2, and assign it to VLAN 30 as an access interface.
e. Assign 52.1.1.1/24, 62.1.1.1/24, 10.1.1.1/24, and 10.10.1.1/24 to VLAN-interface 12, VLAN-interface 22, VLAN-interface 20, and VLAN-interface 30, respectively.
f. Configure PBR policies as follows:
- Specify 52.1.1.2 (IP address of Reth 12) as the next hop for the packets from 10.1.1.0/24.
- Specify 62.1.1.2 (IP address of Reth 22) as the next hop for the packets from 10.10.1.0/24.
14. On Host A, specify 10.1.1.1 (IP address of VLAN-interface 20 on Switch B) as the default gateway. On Host B, specify 10.10.1.1 (IP address of VLAN-interface 30 on Switch B) as the default gateway.
Verifying the configuration
1. Verify the configuration when both Device A and Device B are operating correctly.
# Verify that Device A is the high-priority node in redundancy group a and the member interfaces on both nodes are up.
[DeviceA] display redundancy group a
Redundancy group a (ID 2):
Node ID Slot Priority Status Track weight
1 Slot1 20 Primary 255
2 Slot2 10 Secondary 255
Preempt delay time remained : 0 sec
Preempt delay timer setting : 60 sec
Remaining hold-down time : 0 sec
Hold-down timer setting : 1 sec
Manual switchover request : No
Member interfaces:
Reth11 Reth12
Node 1:
Track info:
Track Status Reduced weight Interface
1 Positive 255 GE1/0/1.11
3 Positive 255 GE1/0/2.12
Node 2:
Track info:
Track Status Reduced weight Interface
5 Positive 255 GE2/0/1.11
7 Positive 255 GE2/0/2.12
# Verify that Device B is the high-priority node in redundancy group b and the member interfaces on both nodes are up.
[DeviceA] display redundancy group b
Redundancy group b (ID 3):
Node ID Slot Priority Status Track weight
1 Slot1 10 Secondary 255
2 Slot2 20 Primary 255
Preempt delay time remained : 0 sec
Preempt delay timer setting : 60 sec
Remaining hold-down time : 0 sec
Hold-down timer setting : 1 sec
Manual switchover request : No
Member interfaces:
Reth21 Reth22
Node 1:
Track info:
Track Status Reduced weight Interface
2 Positive 255 GE1/0/1.21
4 Positive 255 GE1/0/2.22
Node 2:
Track info:
Track Status Reduced weight Interface
6 Positive 255 GE2/0/1.21
8 Positive 255 GE2/0/2.22
2. Verify the configuration when Device A is down.
# Shut down GigabitEthernet 1/0/2 on Device A.
[DeviceA] interface gigabitethernet 1/0/2
[DeviceA-GigabitEthernet1/0/2] shutdown
# Verify that Device B takes over to forward traffic in redundancy group a.
[DeviceA-GigabitEthernet1/0/2] display redundancy group a
Redundancy group a (ID 2):
Node ID Slot Priority Status Track weight
1 Slot1 20 Secondary -255
2 Slot2 10 Primary 255
Preempt delay time remained : 0 sec
Preempt delay timer setting : 60 sec
Remaining hold-down time : 0 sec
Hold-down timer setting : 1 sec
Manual switchover request : No
Member interfaces:
Reth11 Reth12
Node 1:
Track info:
Track Status Reduced weight Interface
1 Negative 255 GE1/0/1.11
3 Negative(Faulty) 255 GE1/0/2.12
Node 2:
Track info:
Track Status Reduced weight Interface
5 Positive 255 GE2/0/1.11
7 Positive 255 GE2/0/2.12
# Verify that Device B is the high-priority node in redundancy group b and the member interfaces on Node 2 are up.
[DeviceA-GigabitEthernet1/0/2] display redundancy group b
Redundancy group b (ID 3):
Node ID Slot Priority Status Track weight
1 Slot1 10 Secondary 0
2 Slot2 20 Primary 255
Preempt delay time remained : 0 sec
Preempt delay timer setting : 60 sec
Remaining hold-down time : 0 sec
Hold-down timer setting : 1 sec
Manual switchover request : No
Member interfaces:
Reth21 Reth22
Node 1:
Track info:
Track Status Reduced weight Interface
2 Positive 255 GE1/0/1.21
4 Negative 255 GE1/0/2.22
Node 2:
Track info:
Track Status Reduced weight Interface
6 Positive 255 GE2/0/1.21
8 Positive 255 GE2/0/2.22
Example: Configuring an IRF hot backup system in dual-active mode with link aggregations
Network configuration
As shown in Figure 20, set up an IRF hot backup system at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the hot backup system to operate in dual-active mode.
· Configure Device A and Device B to load share traffic.
· Connect the hot backup system to the upstream and downstream devices by using link aggregations.
Procedure
1. Configure IRF as described in "Example: Configuring an IRF hot backup system in active/standby mode with one redundancy group."
2. Configure Layer 3 aggregate interfaces:
# Create uplink aggregate interface Route-Aggregation 1 and assign it IP address 51.1.1.2/24.
<DeviceA> system-view
[DeviceA]interface route-aggregation 1
[DeviceA-Route-Aggregation1] ip address 51.1.1.2 24
[DeviceA-Route-Aggregation1] quit
# Create downlink aggregate interface Route-Aggregation 2 and assign it IP address 52.1.1.2/24.
<DeviceA> system-view
[DeviceA]interface route-aggregation 2
[DeviceA-Route-Aggregation2] ip address 52.1.1.2 24
[DeviceA-Route-Aggregation2] quit
# Assign Layer 3 Ethernet interfaces GigabitEthernet 1/0/1 and GigabitEthernet 2/0/1 to aggregation group 1.
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] port link-aggregation group 1
[DeviceA-GigabitEthernet1/0/1] quit
[DeviceA] interface gigabitethernet 2/0/1
[DeviceA-GigabitEthernet2/0/1] port link-aggregation group 1
[DeviceA-GigabitEthernet2/0/1] quit
# Assign Layer 3 Ethernet interfaces GigabitEthernet 1/0/2 and GigabitEthernet 2/0/2 to aggregation group 2.
[DeviceA] interface gigabitethernet 1/0/2
[DeviceA-GigabitEthernet1/0/2] port link-aggregation group 2
[DeviceA-GigabitEthernet1/0/2] quit
[DeviceA] interface gigabitethernet 2/0/2
[DeviceA-GigabitEthernet2/0/2] port link-aggregation group 2
[DeviceA-GigabitEthernet2/0/2] quit
3. Enable session synchronization.
[DeviceA] session synchronization enable
4. Enable session dual-active mode.
[DeviceA] session dual-active enable
5. Assign IP addresses to interfaces and configure routes, security zones, zone pairs, and interzone policies. Make sure the network connections are available. (Details not shown.)
6. Assign Route-Aggregation 1 to security zone Untrust, and assign Route-Aggregation 2 to security zone Trust. (Details not shown.)
7. Configure Switch A:
|
|
NOTE: The following information provides only the summary procedure to configure Switch A. |
a. Create VLAN 10 and VLAN 11.
b. Configure GigabitEthernet 1/0/1 and GigabitEthernet 1/0/2 as Layer 2 access interfaces.
c. Create Layer 2 aggregate interface Bridge-Aggregation 1, assign GigabitEthernet 1/0/1 and GigabitEthernet 1/0/2 to its aggregation group, and assign Bridge-Aggregation 1 to VLAN 11.
d. Configure GigabitEthernet 1/0/3 to operate at Layer 2, and assign it to VLAN 10 as an access interface.
e. Assign 51.1.1.1/24 and 2.1.1.1/24 to VLAN-interface 11 and VLAN-interface 10, respectively.
f. Configure routes as follows:
- Specify 51.1.1.2 (IP address of Route-Aggregate 1 on the IRF fabric) as the next hop of the route to the internal network.
- Specify 2.1.1.2 (an IP address on the router) as the next hop of the route to the Internet.
8. Configure Switch B:
|
|
NOTE: The following information provides only the summary procedure to configure Switch B. |
a. Create VLAN 12 and VLAN 20.
b. Configure GigabitEthernet 1/0/1 and GigabitEthernet 1/0/2 as Layer 2 access interfaces.
c. Create Layer 2 aggregate interface Bridge-Aggregation 1, assign GigabitEthernet 1/0/1 and GigabitEthernet 1/0/2 to its aggregation group, and assign Bridge-Aggregation 1 to VLAN 12.
d. Configure GigabitEthernet 1/0/3 to operate at Layer 2, and assign it to VLAN 20 as an access interface.
e. Assign 52.1.1.1/24 and 10.1.1.1/24 to VLAN-interface 12 and VLAN-interface 20, respectively.
f. Specify 52.1.1.2 (IP address of Route-Aggregation 2 on the IRF fabric) as the next hop of the route to the Internet.
9. On the host, specify 10.1.1.1 (IP address of VLAN-interface 20 on Switch B) as the default gateway.
Verifying the configuration
1. Verify that both Device A and Device B have session entries when they are operating correctly. How traffic is distributed among the member interfaces of an aggregation group depends on the load sharing mode.
[DeviceA] display session table ipv4 verbose
Slot 1:
Initiator:
Source IP/port: 10.1.1.1/19401
Destination IP/port: 123.125.115.110/80
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Route-Aggregation1
Source security zone: Trust
Responder:
Source IP/port: 123.125.115.110/80
Destination IP/port: 10.1.1.1/19401
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Route-Aggregation2
Source security zone: Untrust
State: INACTIVE
Application: HTTP
Rule ID: 2
Rule name: 3
Start time: 2018-01-21 15:59:58 TTL: 295s
Initiator->Responder: 0 packets 0 bytes
Responder->Initiator: 0 packets 0 bytes
Initiator:
Source IP/port: 10.1.1.1/19400
Destination IP/port: 123.125.115.110/443
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Route-Aggregation1
Source security zone: Trust
Responder:
Source IP/port: 123.125.115.110/443
Destination IP/port: 10.1.1.1/19400
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Route-Aggregation2
Source security zone: Untrust
State: INACTIVE
Application: HTTPS
Rule ID: 2
Rule name: 3
Start time: 2018-01-21 15:59:58 TTL: 295s
Initiator->Responder: 110 packets 4493 bytes
Responder->Initiator: 178 packets 9065 bytes
Total sessions found: 2
Slot 2:
Initiator:
Source IP/port: 10.1.1.1/19401
Destination IP/port: 123.125.115.110/80
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Route-Aggregation1
Source security zone: Trust
Responder:
Source IP/port: 123.125.115.110/80
Destination IP/port: 10.1.1.1/19401
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Route-Aggregation2
Source security zone: Untrust
State: INACTIVE
Application: HTTP
Rule ID: 2
Rule name: 3
Start time: 2018-01-21 15:59:58 TTL: 295s
Initiator->Responder: 1110 packets 5493 bytes
Responder->Initiator: 1718 packets 8065 bytes
Initiator:
Source IP/port: 10.1.1.1/19400
Destination IP/port: 123.125.115.110/443
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Route-Aggregation1
Source security zone: Trust
Responder:
Source IP/port: 123.125.115.110/443
Destination IP/port: 10.1.1.1/19400
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Route-Aggregation2
Source security zone: Untrust
State: INACTIVE
Application: HTTPS
Rule ID: 2
Rule name: 3
Start time: 2018-01-21 15:59:58 TTL: 295s
Initiator->Responder: 0 packets 0 bytes
Responder->Initiator: 0 packets 0 bytes
Total sessions found: 2
2. Verify that only Device B has session entries after GigabitEthernet 1/0/1 and GigabitEthernet 1/0/2 on Device A fail.
[DeviceA] display session table ipv4 verbose
Slot 1:
Initiator:
Source IP/port: 10.1.1.1/19401
Destination IP/port: 123.125.115.110/80
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Route-Aggregation1
Source security zone: Trust
Responder:
Source IP/port: 123.125.115.110/80
Destination IP/port: 10.1.1.1/19401
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Route-Aggregation2
Source security zone: Untrust
State: INACTIVE
Application: HTTP
Rule ID: 2
Rule name: 3
Start time: 2018-01-21 16:10:58 TTL: 295s
Initiator->Responder: 0 packets 0 bytes
Responder->Initiator: 0 packets 0 bytes
Initiator:
Source IP/port: 10.1.1.1/19400
Destination IP/port: 123.125.115.110/443
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Route-Aggregation1
Source security zone: Trust
Responder:
Source IP/port: 123.125.115.110/443
Destination IP/port: 10.1.1.1/19400
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Route-Aggregation2
Source security zone: Untrust
State: INACTIVE
Application: HTTPS
Rule ID: 2
Rule name: 3
Start time: 2018-01-21 16:10:58 TTL: 295s
Initiator->Responder: 0 packets 0 bytes
Responder->Initiator: 0 packets 0 bytes
Total sessions found: 2
Slot 2:
Initiator:
Source IP/port: 10.1.1.1/19401
Destination IP/port: 123.125.115.110/80
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Route-Aggregation1
Source security zone: Trust
Responder:
Source IP/port: 123.125.115.110/80
Destination IP/port: 10.1.1.1/19401
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Route-Aggregation2
Source security zone: Untrust
State: INACTIVE
Application: HTTP
Rule ID: 2
Rule name: 3
Start time: 2018-01-21 16:10:58 TTL: 295s
Initiator->Responder: 1110 packets 5493 bytes
Responder->Initiator: 1718 packets 8065 bytes
Initiator:
Source IP/port: 10.1.1.1/19400
Destination IP/port: 123.125.115.110/443
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Route-Aggregation1
Source security zone: Trust
Responder:
Source IP/port: 123.125.115.110/443
Destination IP/port: 10.1.1.1/19400
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: Route-Aggregation2
Source security zone: Untrust
State: INACTIVE
Application: HTTPS
Rule ID: 2
Rule name: 3
Start time: 2018-01-21 16:10:58 TTL: 295s
Initiator->Responder: 110 packets 4493 bytes
Responder->Initiator: 178 packets 9065 bytes
Total sessions found: 2