- Table of Contents
-
- 10-Security Configuration Guide
- 00-Preface
- 01-AAA configuration
- 02-802.1X configuration
- 03-MAC authentication configuration
- 04-Portal configuration
- 05-Port security configuration
- 06-Password control configuration
- 07-Keychain configuration
- 08-Public key management
- 09-PKI configuration
- 10-IPsec configuration
- 11-SSH configuration
- 12-SSL configuration
- 13-Attack detection and prevention configuration
- 14-TCP attack prevention configuration
- 15-IP source guard configuration
- 16-ARP attack protection configuration
- 17-ND attack defense configuration
- 18-uRPF configuration
- 19-MFF configuration
- 20-FIPS configuration
- 21-MACsec configuration
- 22-802.1X client configuration
- 23-Web authentication configuration
- 24-Object group configuration
- 25-Triple authentication configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 19-MFF configuration | 130.33 KB |
Processing of ARP packets in MFF
Enabling periodic gateway probe
Specifying the IP addresses of servers
Displaying and maintaining MFF
Manual-mode MFF configuration example in a tree network
Manual-mode MFF configuration example in a ring network
Configuring MFF
Overview
MAC-forced forwarding (MFF) implements Layer 2 isolation and Layer 3 communication between hosts in the same broadcast domain.
An MFF-enabled device intercepts ARP requests and returns the MAC address of a gateway (or server) to the senders. In this way, the senders are forced to send packets to the gateway for traffic monitoring and attack prevention.
MFF network model
As shown in Figure 1, hosts are connected to Switch C through Switch A and Switch B, which are called Ethernet access nodes (EANs). The MFF-enabled EANs forward packets from hosts to the gateway for further forwarding. The hosts are isolated at Layer 2, but they can communicate at Layer 3.
Figure 1 Network diagram for MFF
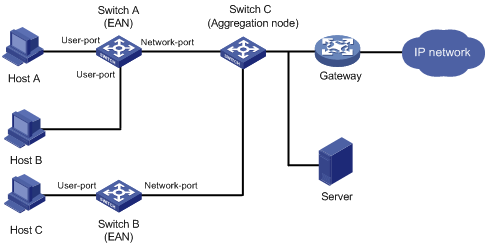
MFF works with any of the following features to implement traffic filtering and Layer 2 isolation on the EANs:
· ARP snooping (see Layer 3—IP Services Configuration Guide).
· IP source guard (see "Configuring IP source guard").
· ARP detection (see "Configuring ARP attack protection").
· VLAN mapping (see Layer 2—LAN Switching Configuration Guide).
Port roles
Two types of ports, user port and network port, exist in an MFF-enabled device.
User port
An MFF user port is directly connected to a host and processes the following packets differently:
· Allows multicast packets to pass.
· Delivers ARP packets to the CPU.
· Processes unicast packets as follows:
¡ If gateways' MAC addresses have been learned, the user port allows only the unicast packets with the gateways' MAC addresses as the destination MAC addresses to pass.
¡ If no gateways' MAC addresses have been learned, the user port discards all received unicast packets.
Network port
An MFF network port is connected to any of the following networking devices:
· An access switch.
· A distribution switch.
· A gateway.
· A server.
A network port processes the following packets differently:
· Allows multicast packets to pass.
· Delivers ARP packets to the CPU.
· Denies broadcast packets other than DHCP and ARP packets.
Processing of ARP packets in MFF
An MFF-enabled device implements Layer 3 communication between hosts by intercepting ARP requests from the hosts and replies with the MAC address of a gateway. This mechanism helps reduce the number of broadcast messages.
The MFF device processes ARP packets as follows:
· After receiving an ARP request from a host, the MFF device sends the MAC address of the corresponding gateway to the host. In this way, hosts in the network have to communicate at Layer 3 through a gateway.
· After receiving an ARP request from a gateway, the MFF device sends the requested host's MAC address to the gateway if the corresponding entry is available. If the entry is not available, the MFF device forwards the ARP request.
· The MFF device forwards ARP replies between hosts and gateways.
· If the source MAC addresses of ARP requests from gateways are different from those recorded, the MFF device updates and broadcasts the IP and MAC addresses of the gateways.
MFF default gateway
MFF applies to only networks where the hosts' IP addresses are manually configured. Because the hosts cannot obtain the gateway information through DHCP, the default gateway must be specified by the mac-forced-forwarding default-gateway command. MFF maintains only one default gateway for each VLAN. MFF updates the MAC address of the default gateway upon receiving an ARP packet with a different sender MAC address from the default gateway.
Protocols and standards
RFC 4562, MAC-Forced Forwarding
Configuration procedure
Enabling MFF
For MFF to take effect, make sure ARP snooping is enabled on the VLAN where MFF is enabled.
To enable MFF:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view. |
vlan vlan-id |
N/A |
|
3. Enable MFF. |
mac-forced-forwarding default-gateway gateway-ip |
By default, MFF is disabled. |
Configuring a network port
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
·
Enter Layer 2 Ethernet interface view: ·
Enter Layer 2 aggregate interface view: |
N/A |
|
3. Configure the port as a network port. |
mac-forced-forwarding network-port |
By default, the port is a user port. |
Enabling periodic gateway probe
You can configure the MFF device to detect gateways every 30 seconds for the change of MAC addresses by sending forged ARP packets. The ARP packets use 0.0.0.0 as the sender IP address and bridge MAC address as the sender MAC address.
To enable periodic gateway probe:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view. |
vlan vlan-id |
N/A |
|
3. Enable periodic gateway probe. |
mac-forced-forwarding gateway probe |
By default, this feature is disabled. |
Specifying the IP addresses of servers
When the MFF device receives an ARP request from a server, the device searches IP-to-MAC address entries it has stored. Then the device replies with the requested MAC address to the server.
As a result, packets from a host to a server are forwarded by the gateway. However, packets from a server to a host are not forwarded by the gateway.
MFF does not check whether the IP address of a server is on the same network segment as that of a gateway. Instead, it checks whether the IP address of a server is all-zero or all-one. An all-zero or all-one server IP address is invalid.
To specify the IP addresses of servers:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view. |
vlan vlan-id |
N/A |
|
3. Specify the IP addresses of servers. |
mac-forced-forwarding server server-ip&<1-10> |
By default, no server IP address is specified. If the server's interface connecting to the MFF device uses secondary IP addresses to send ARP packets, include all these IP addresses in the server IP address list. |
Displaying and maintaining MFF
Execute display commands in any view.
|
Task |
Command |
|
Display MFF port configuration. |
display mac-forced-forwarding interface |
|
Display the MFF configuration for a VLAN. |
display mac-forced-forwarding vlan vlan-id |
MFF configuration examples
Manual-mode MFF configuration example in a tree network
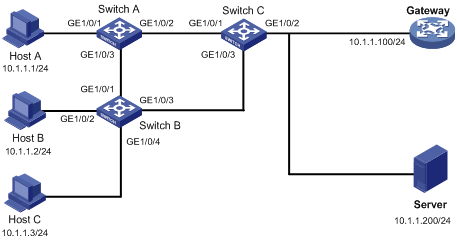
Network requirements
As shown in Figure 2, all the devices are in VLAN 100. Hosts A, B, and C are assigned IP addresses manually.
Configure MFF to isolate the hosts at Layer 2 and allow them to communicate with each other through the gateway at Layer 3.

Configuration procedure
1. Configure the IP addresses of the hosts and the gateway, as shown in Figure 2.
2. Configure Switch A:
# Configure manual-mode MFF on VLAN 100.
[SwitchA] vlan 100
[SwitchA-vlan100] mac-forced-forwarding default-gateway 10.1.1.100
# Specify the IP address of the server.
[SwitchA-vlan100] mac-forced-forwarding server 10.1.1.200
# Enable ARP snooping on VLAN 100.
[SwitchA-vlan100] arp snooping enable
[SwitchA-vlan100] quit
# Configure GigabitEthernet 1/0/1 as a network port.
[SwitchA] interface gigabitethernet 1/0/1
[SwitchA-GigabitEthernet1/0/1] mac-forced-forwarding network-port
3. Configure Switch B:
# Configure manual-mode MFF on VLAN 100.
[SwitchB] vlan 100
[SwitchB-vlan100] mac-forced-forwarding default-gateway 10.1.1.100
# Specify the IP address of the server.
[SwitchB-vlan100] mac-forced-forwarding server 10.1.1.200
# Enable ARP snooping on VLAN 100.
[SwitchB-vlan100] arp snooping enable
[SwitchB-vlan100] quit
# Configure GigabitEthernet 1/0/2 as a network port.
[SwitchB] interface gigabitethernet 1/0/2 1/0/6
[SwitchB-GigabitEthernet1/0/2] mac-forced-forwarding network-port
Manual-mode MFF configuration example in a ring network
Network requirements
As shown in Figure 3, all the devices are in VLAN 100, and the switches form a ring. Hosts A, B, and C are assigned IP addresses manually.
Configure MFF to isolate the hosts at Layer 2 and allow them to communicate with each other through the gateway at Layer 3.
Configuration procedure
1. Configure the IP addresses of the hosts and the gateway, as in shown in Figure 3.
2. Configure Switch A:
# Enable STP globally to make sure STP is enabled on interfaces.
[SwitchA] stp global enable
# Configure manual-mode MFF on VLAN 100.
[SwitchA] vlan 100
[SwitchA-vlan100] mac-forced-forwarding default-gateway 10.1.1.100
# Specify the IP address of the server.
[SwitchA-vlan100] mac-forced-forwarding server 10.1.1.200
# Enable ARP snooping on VLAN 100.
[SwitchA-vlan100] arp snooping enable
[SwitchA-vlan100] quit
# Configure GigabitEthernet 1/0/2 and GigabitEthernet 1/0/3 as network ports.
[SwitchA] interface gigabitethernet 1/0/2
[SwitchA-GigabitEthernet1/0/2] mac-forced-forwarding network-port
[SwitchA-GigabitEthernet1/0/2] quit
[SwitchA] interface gigabitethernet 1/0/3
[SwitchA-GigabitEthernet1/0/3] mac-forced-forwarding network-port
3. Configure Switch B:
# Enable STP globally to make sure STP is enabled on interfaces.
[SwitchB] stp global enable
# Configure manual-mode MFF on VLAN 100.
[SwitchB] vlan 100
[SwitchB-vlan100] mac-forced-forwarding default-gateway 10.1.1.100
# Specify the IP address of the server.
[SwitchB-vlan100] mac-forced-forwarding server 10.1.1.200
# Enable ARP snooping on VLAN 100.
[SwitchB-vlan100] arp snooping enable
[SwitchB-vlan100] quit
# Configure GigabitEthernet 1/0/1 and GigabitEthernet 1/0/3 as network ports.
[SwitchB] interface gigabitethernet 1/0/1
[SwitchB-GigabitEthernet1/0/1] mac-forced-forwarding network-port
[SwitchB-GigabitEthernet1/0/1] quit
[SwitchB] interface gigabitethernet 1/0/3
[SwitchB-GigabitEthernet1/0/3] mac-forced-forwarding network-port
4. Enable STP on Switch C globally to make sure STP is enabled on interfaces.
<SwitchC> system-view
[SwitchC] stp global enable

