Country / Region
Carrier Cloud Security Solution
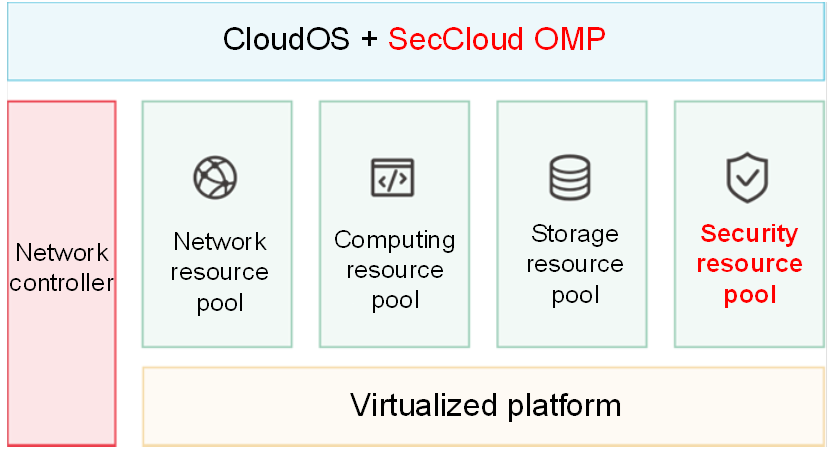
H3C Group is among vendors that boast capabilities simultaneously in cloud platform construction, network construction, as well as security construction in the industry. With the advantages of the cloud and network, H3C can deeply integrate the cloud security with the cloud network to form the integrated capability of "cloud network security". Based on SecCloud OMP, H3C proposes a security-as-a-service concept, enabling a security service directory of the cloud platform. In addition, H3C can directly deploy the security components required by tenants in the tenant network through interworking between security and network controllers without diversion of traffic. The cloud security solution provides multiple protection capabilities, including cloud firewall, cloud intrusion protection, cloud load, cloud WAF, cloud database audit, cloud bastion host, cloud leakage scanning, and cloud log audit, to realize flexible deployment while ensuring compliance with information classified security protection.
Features
Security as a service
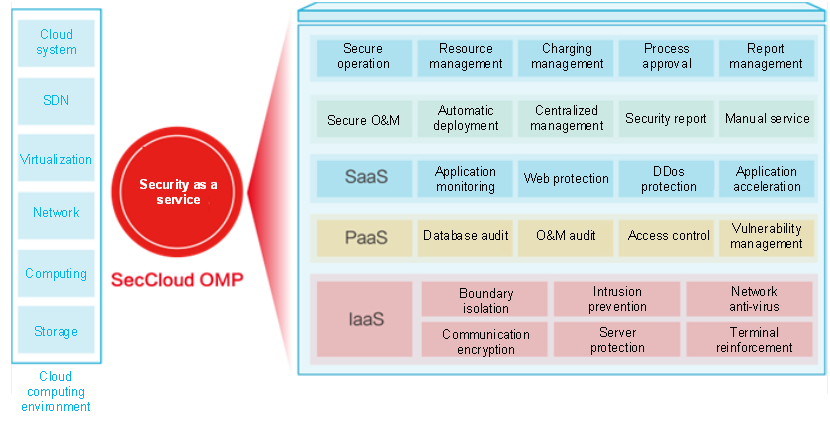
In the cloud security solutions, H3C proposed the concept of security as a service and built a "cloud security store" through the SecCloud OMP, to meet requirements in different scenarios. Security requirements include IaaS layer security requirements (such as border isolation, intrusion prevention, communication encryption and server protection), PaaS layer security requirements (such as database audit, O&M audit and vulnerability management), and SaaS layer security requirements (such as application monitoring, Web protection and application acceleration). Security service components can be selected as required, flexibly distributed, automatically deployed, and flexibly extended. From the O&M and operation perspectives, the visualization of cloud security and the allocation and management of cloud security resources are realized.
Security service orchestration capability
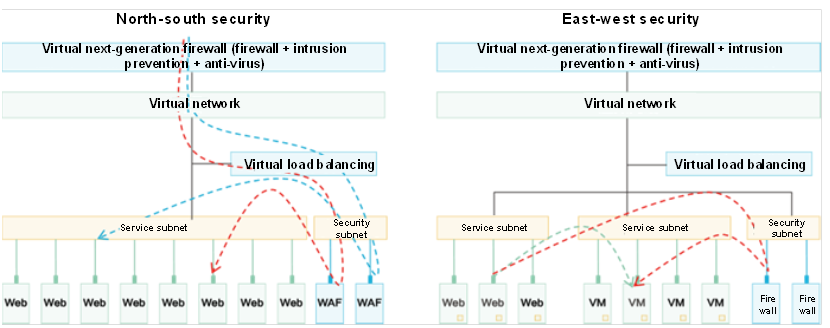
In the cloud security solutions, H3C connected security components to the virtual network of a tenant through the SecCloud OMP. After the tenant creates a network, the security components can be deployed according to a standard model, eliminating the need to consider the connection of security components and virtual network. The north-south and east-west security models are shown in the figure. The north-south security incorporates the border protection capability, intrusion prevention capability and network anti-virus capability, and enhances the security capability of the application layer, such as load balancing capability and Web application protection capability. The east-west security relies on the cooperation between the network controller and the firewall to realize the security access control, intrusion prevention and virus protection inside VPC through the security service chain. In the east-west security, the server security monitoring components are deployed to assist in the security management at the service VM level.
Innovation of security resource pool
The H3C Group has creatively enhanced the pool management of security resources. Based on the characteristics of mainstream security products, H3C proposed the concept of a hardware resource pool while ensuring compatibility with common software resource pools in the industry. Specifically, a flexible, extensible security resource pool can be formed only through hardware security devices. Security hardware provides virtual interfaces for different services in the cloud through security cloud, to efficiently use and share hardware resources. A resource pool composed of hardware has advantages of high performance and good stability, and can also avoid compatibility and authorization management issues typical of a virtualization platform. In addition, the existing resources can be fully utilized to save cost.
Independent hardware resource pool
The device comes with a virtual security capability. Due to this capability, each virtual instance is completely independent of each other, such as FW and LB.
Shared hardware resource pool
The hardware does not have a virtualization capability. Multiple virtual instances are realized through SecCloud OMP and a tenant can share only one hardware security capability to save cost, such as anti-DDoS and leakage scanning.
Independent software resource pool
The security product is in a NFV form. Each tenant independently uses one NFV resource to form a pure software resource pool, such as vFW, vLB, vWAF, virtual bastion host, virtual database audit, and virtual log audit.
Mixed soft/hard resource pool
The software resource pool is mixed with a shared hardware resource pool, making full use of all security resources and optimizing the resource pool capability to a greater extent, such as database audit, bastion host and log audit.


