Security Announcement-Statement on VMware vCenter Server arbitrary file read vulnerability security notice
25-02-2021Overview
The Background of security vulnerability
Recently, the New H3C Group Attack and Defense Lab has detected an arbitrary file reading vulnerability in VMware vCenter Server. Unauthenticated attackers can use this vulnerability to read all files of the affected target server.
At present, the POC of this vulnerability has been publicly disclosed on the Internet. Its use method is simple and harmful. The Xinhua Three Attack and Defense Laboratory recommends that users upgrade the affected vCenter Server to the latest security version in time.
The details of vulnerability
VMware vCenter Server provides a scalable and extensible platform that can centrally manage the VMware vSphere environment, which greatly improves IT administrators' control over the virtual environment. It improves centralized control and visibility at every level of the virtual infrastructure, and unleashes the potential of vSphere through active management.
VMware vCenter versions prior to 6.5 have arbitrary file reading vulnerabilities. Unauthenticated attackers can access all directories of the target server through the id parameter and read the content of the file, and then access the configuration file of the target server, read the user account password, and finally control vCenter server.
The reproduce of security vulnerability
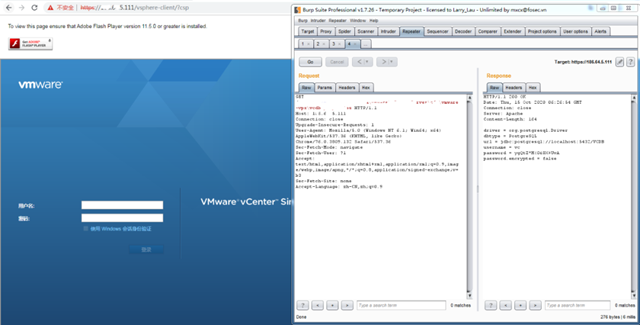
Set up the vCenter Server 6.0 test environment and send the payload to successfully read the configuration file.
The scope of influence
Sphere of influence
Affected version:
VMware vCenter Server <=6.5.0f
Risk level
High risk
Solution
The official patch
VMware has fixed this vulnerability in version 6.5.0u1. It is recommended to upgrade to the latest security version:
https://my.vmware.com/cn/web/vmware/downloads/details?downloadGroup=VC700D&productId=974&rPId=52117
The temporary solution
If it is not convenient to upgrade, you can temporarily mitigate the impact through the following steps:
Close the vCenter console to the public network and restrict the internal network to only allow trusted IP access.
The solution of H3C
The 1.0.108 version of the H3C IPS rule library will support the identification of this vulnerability. It is recommended to pay attention to the timely upgrade of the H3C official website and enable relevant rules.
H3C security emergency response external service
H3C advocates that every effort be made to safeguard the ultimate interests of product users, to abide by principles of responsible disclosure of security incidents, and to handle product security issues in accordance with security issues mechanisms. For information on H3C's security emergency response service and H3C product vulnerabilities, please visit https://www.h3c.com/en/Support/Online_Help/psirt/.

