Security Announcement -Statement on Microsoft Windows Defender remote code execution vulnerability (CVE-2021-1647)
25-02-2021Overview
The Background of security vulnerabilities
Windows Defender, an anti-virus software officially released by Microsoft, can run on Windows XP and later Windows operating systems, and is currently built into Windows Vista and later versions of Windows.
On January 8, 2021, the Threat Early Warning Team of the New H3C Offensive and Defense Laboratory monitored that Microsoft officially issued a security bulletin, reporting that Windows Defender has a remote code execution vulnerability, the vulnerability number is CVE-2021-1647, the vulnerability levelis the high.
Vulnerability principle
There is a remote code execution vulnerability in Windows Defender. Attackers can induce victims to download malicious files constructed by the attackers by sending emails or malicious links to the target machine. When Windows Defender is automatically scanning, the malicious file will trigger the vulnerability and execute arbitrary code on the victim's machine. According to Microsoft's official description, the wild use of CVE-2021-1647 has been discovered, and users are requested to update the patch as soon as possible.
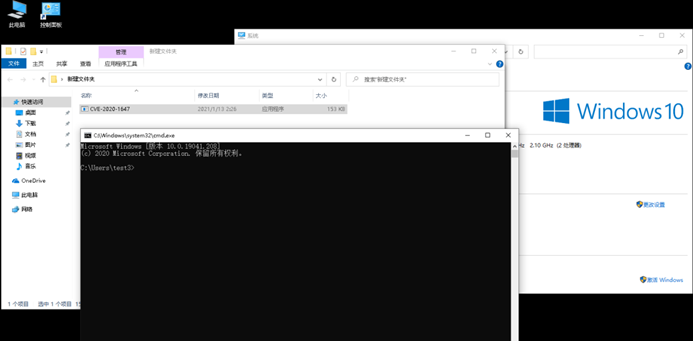
The reproduce of security vulnerability
Set up the Windows 10 version environment and enable the Windows Defender component. When Windows Defender scans the malicious file, a command line will pop up.
The scope of influence
Affected version:
Windows 7 SP1
Windows 8.1
Windows RT 8.1
Windows 10
Windows 10 Version 1607, 1803, 1809, 1909, 2004, 20H2
Windows Server 2008 SP2
Windows Server 2008 R2 SP1
Windows Server 2012, 2012R2 ,2016, 2019
Windows Server Version 1909,2004, 20h2
Solution
The official patch
The latest version of the official release has fixed this vulnerability, affected users are requested to update the patch as soon as possible. Patch download address:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-1667
H3C security emergency response external service
H3C advocates that every effort be made to safeguard the ultimate interests of product users, to abide by principles of responsible disclosure of security incidents, and to handle product security issues in accordance with security issues mechanisms. For information on H3C's security emergency response service and H3C product vulnerabilities, please visit https://www.h3c.com/en/Support/Online_Help/psirt/.

